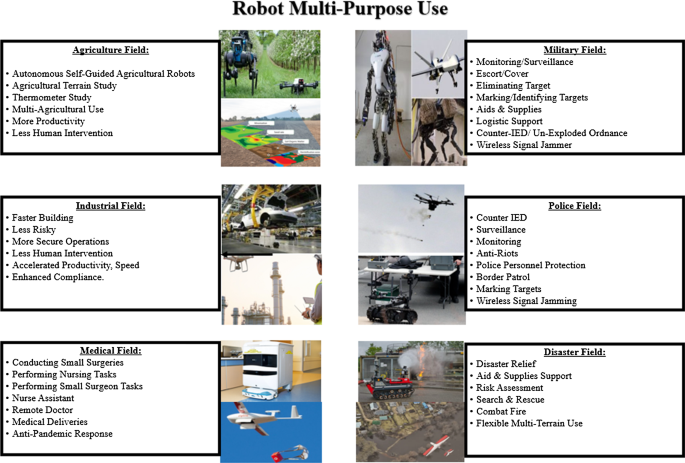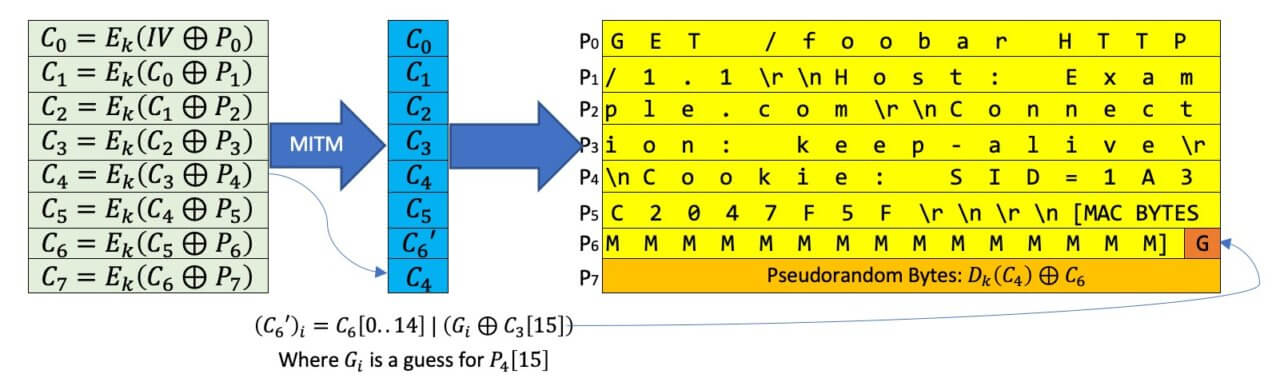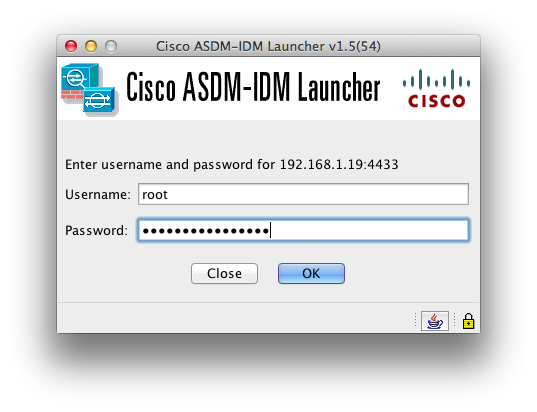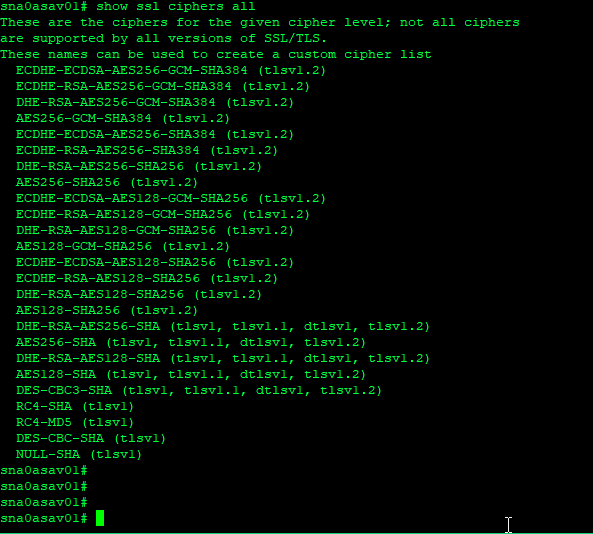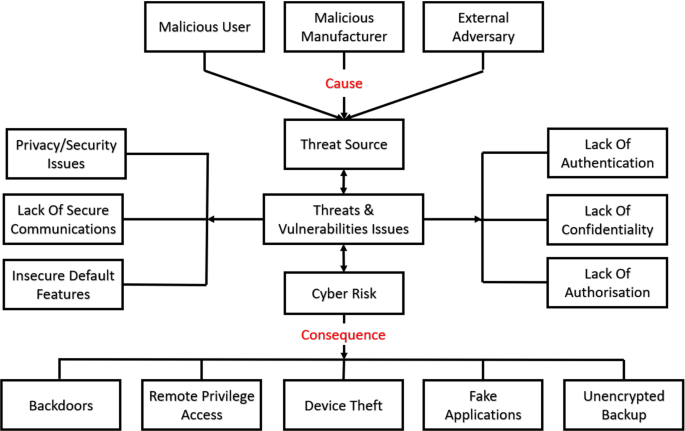
Robotics cyber security: vulnerabilities, attacks, countermeasures, and recommendations | SpringerLink
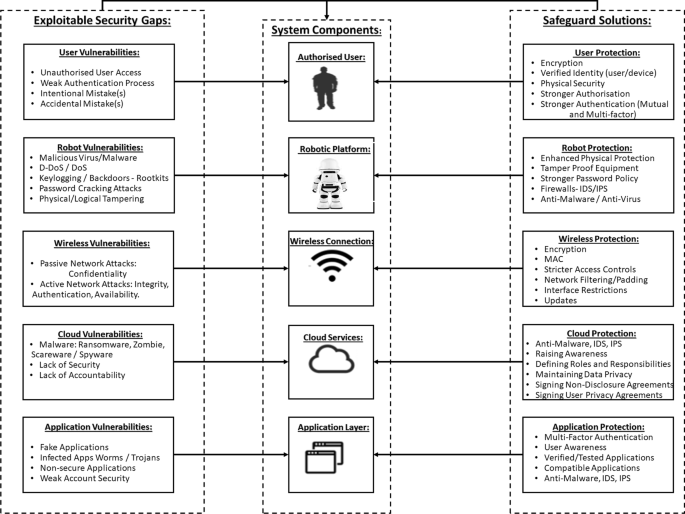
Robotics cyber security: vulnerabilities, attacks, countermeasures, and recommendations | SpringerLink
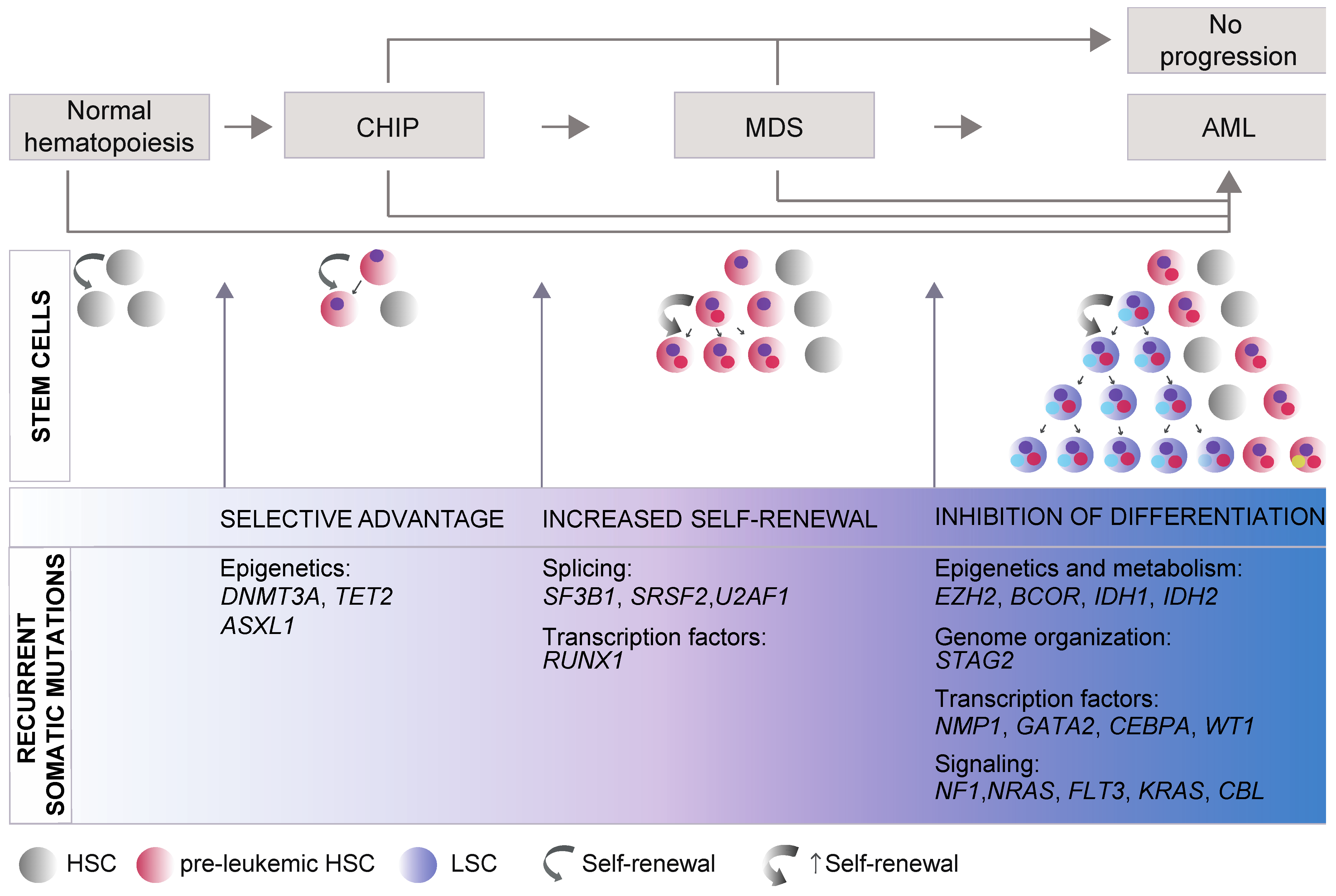
Cancers | Free Full-Text | Transcription Factors, R-Loops and Deubiquitinating Enzymes: Emerging Targets in Myelodysplastic Syndromes and Acute Myeloid Leukemia
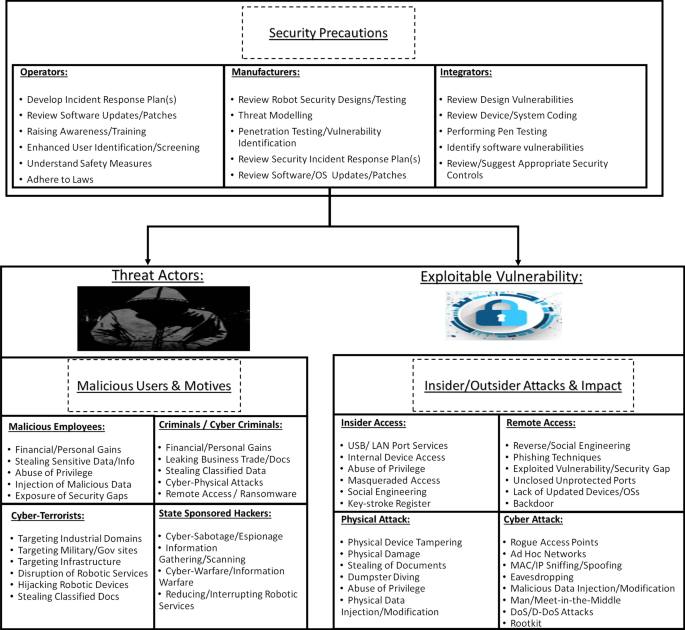
Robotics cyber security: vulnerabilities, attacks, countermeasures, and recommendations | SpringerLink