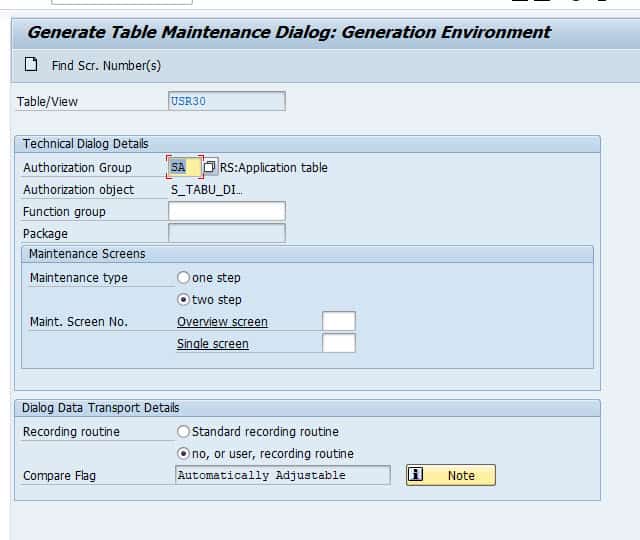
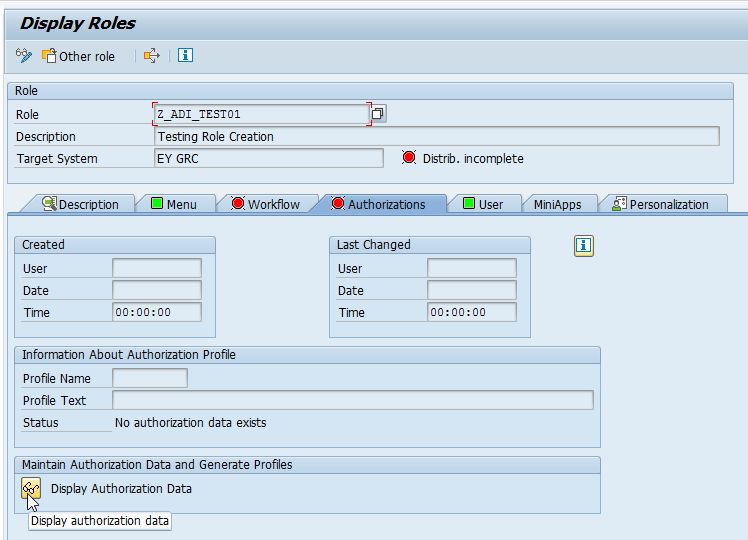
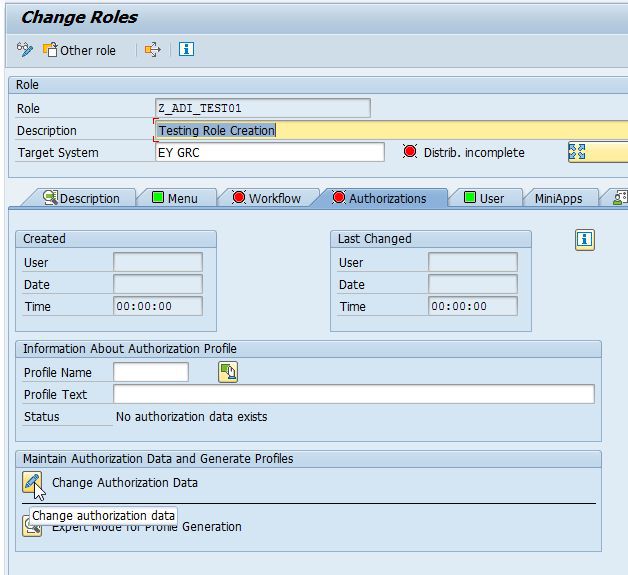
Some Important Information about SAP Authorization Objects as a Functional/Technical Consultant | SAP Blogs

Some Important Information about SAP Authorization Objects as a Functional/Technical Consultant | SAP Blogs

Some Important Information about SAP Authorization Objects as a Functional/Technical Consultant | SAP Blogs