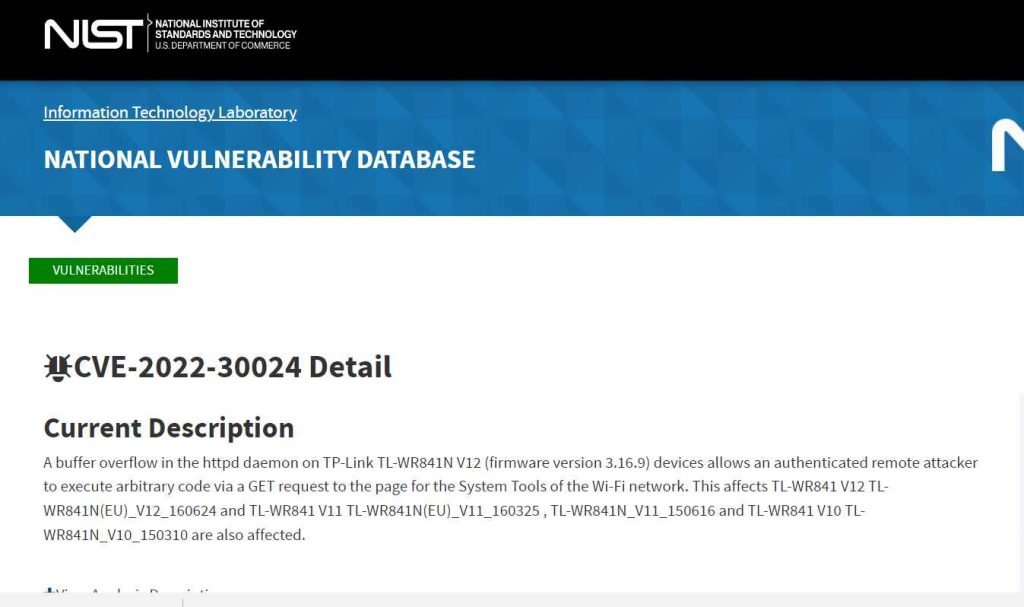
How To Fix CVE-2021-34991- A Pre-Authentication Buffer Overflow On Multiple Netgear Products? - The Sec Master

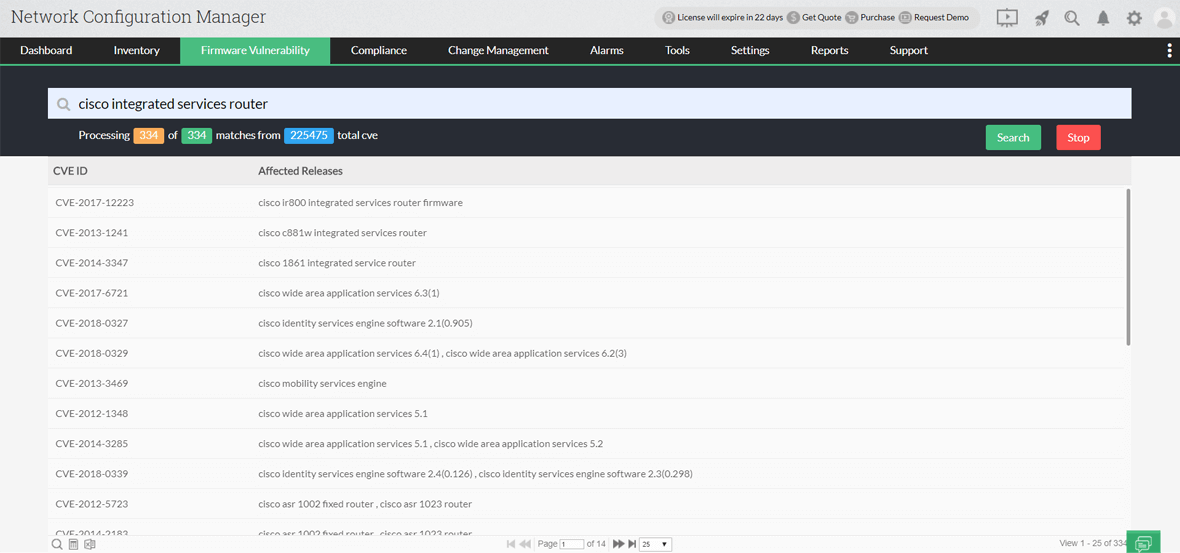
Advisory: Cisco Small Business RV Series Routers Web Filter Database Update Command Injection Vulnerability - ONEKEY

PDF) Classifying Common Vulnerabilities and Exposures Database Using Text Mining and Graph Theoretical Analysis

Hundreds of thousands of Realtek-based devices under attack from IoT botnet - The Record from Recorded Future News
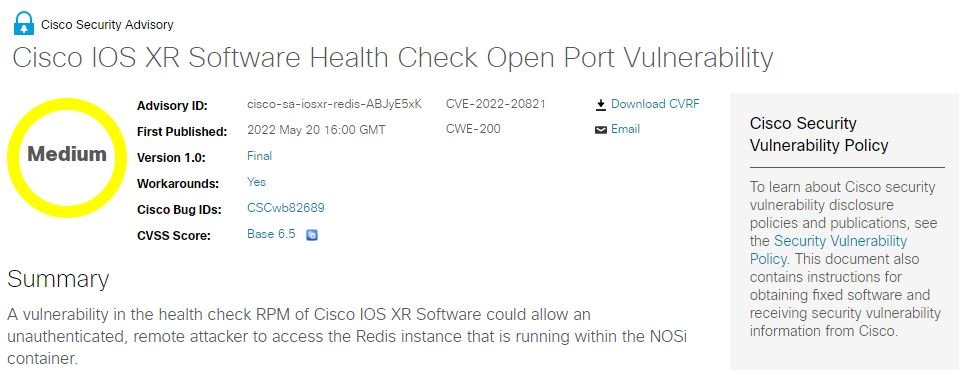
Zero-day vulnerability in Cisco IOS XR router software allows unauthenticated hackers to access these devices remotely
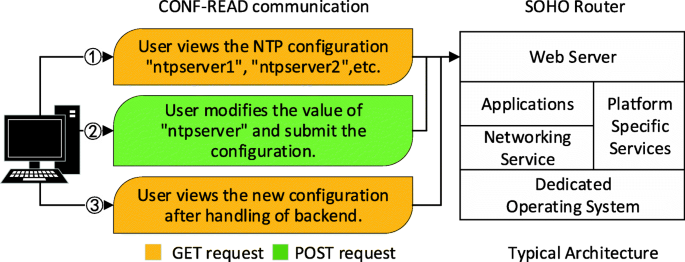
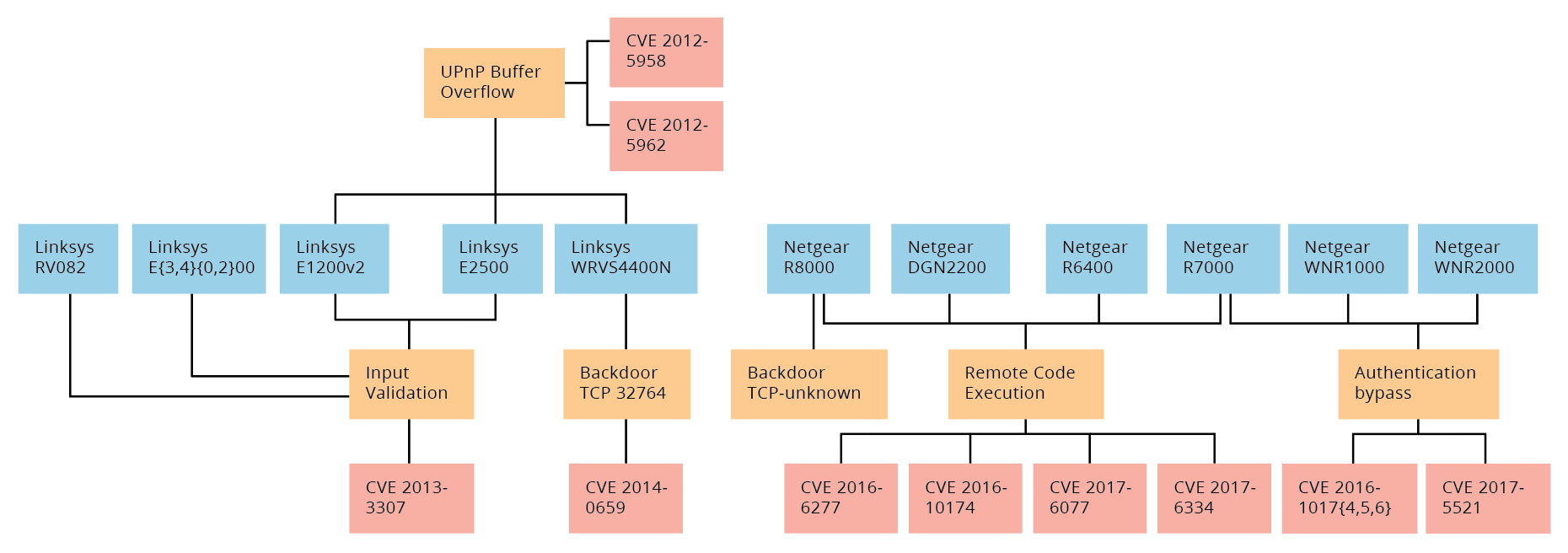
ESRFuzzer: an enhanced fuzzing framework for physical SOHO router devices to discover multi-Type vulnerabilities | Cybersecurity | Full Text
![IPA Information-technology Promotion Agency, Japan : Vulnerability Countermeasure Information Database JVN iPedia Registration Status [2017 3rd Quarter (Jul. - Sep.)] IPA Information-technology Promotion Agency, Japan : Vulnerability Countermeasure Information Database JVN iPedia Registration Status [2017 3rd Quarter (Jul. - Sep.)]](https://www.ipa.go.jp/files/000062671.png)
IPA Information-technology Promotion Agency, Japan : Vulnerability Countermeasure Information Database JVN iPedia Registration Status [2017 3rd Quarter (Jul. - Sep.)]

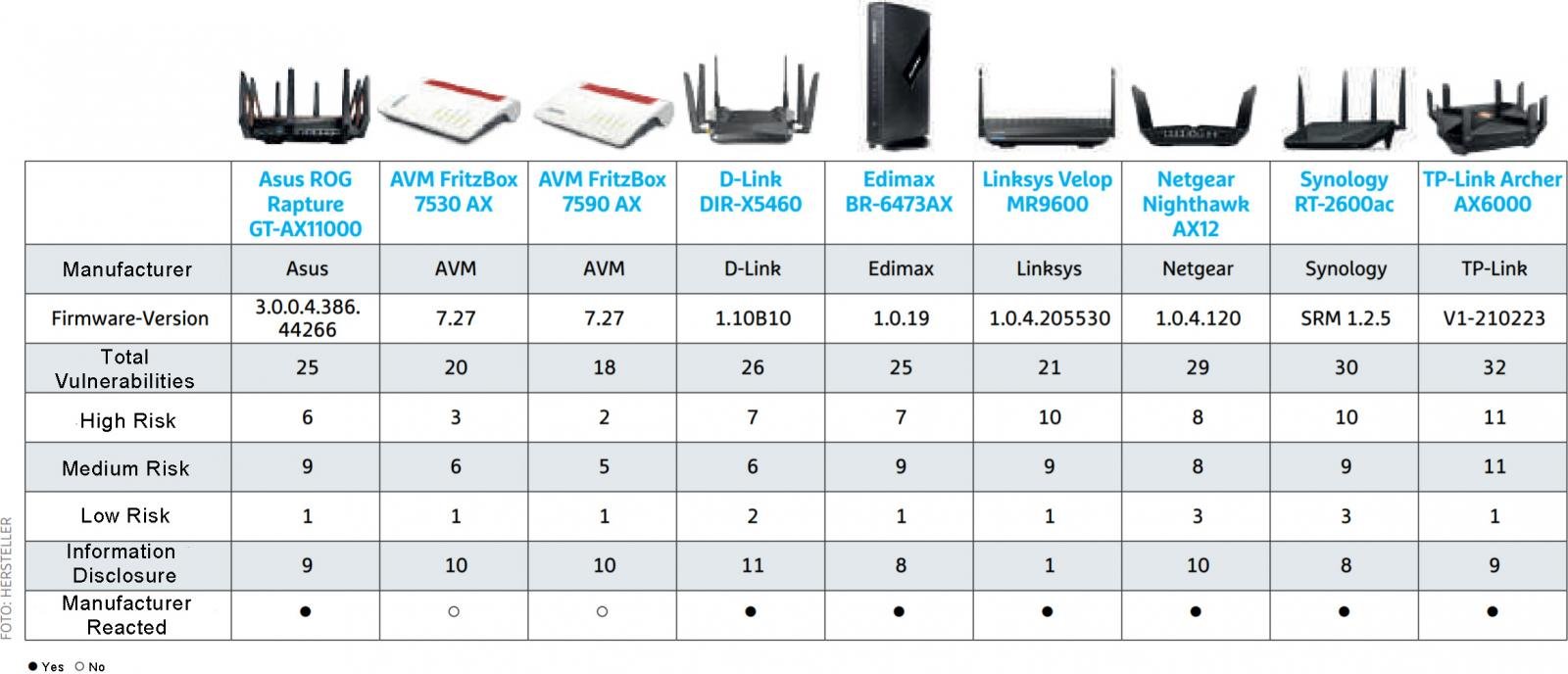
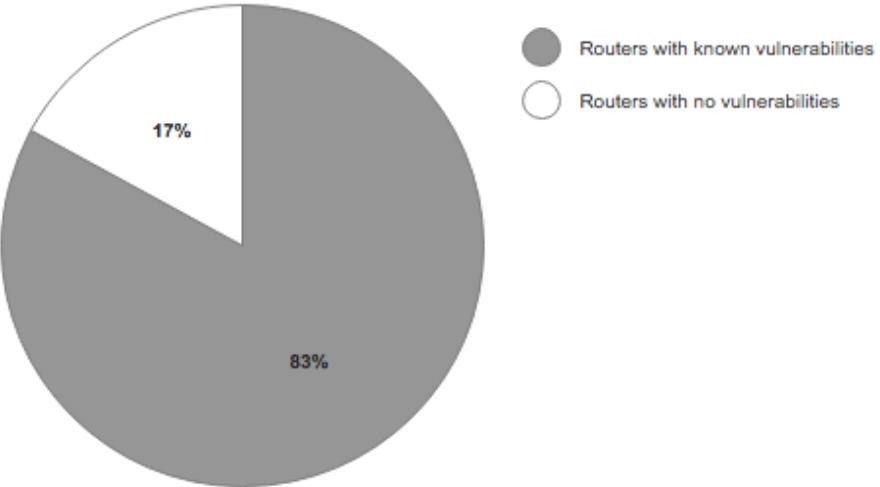
2020 H1 Cybersecurity Trends - NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks.