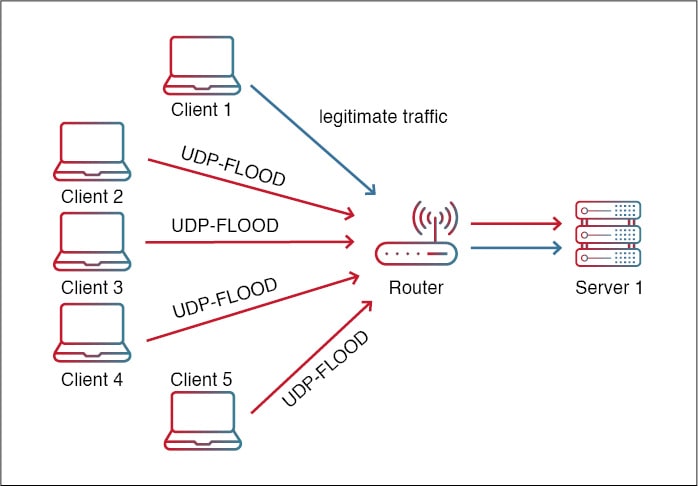
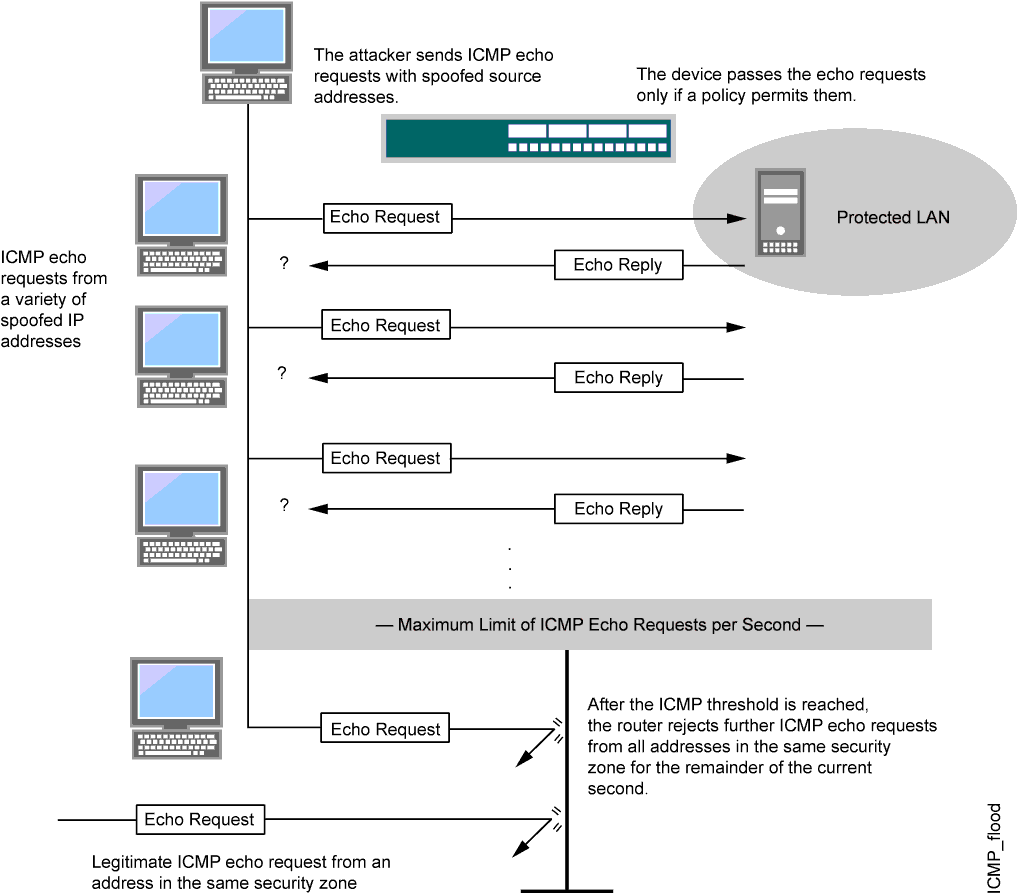
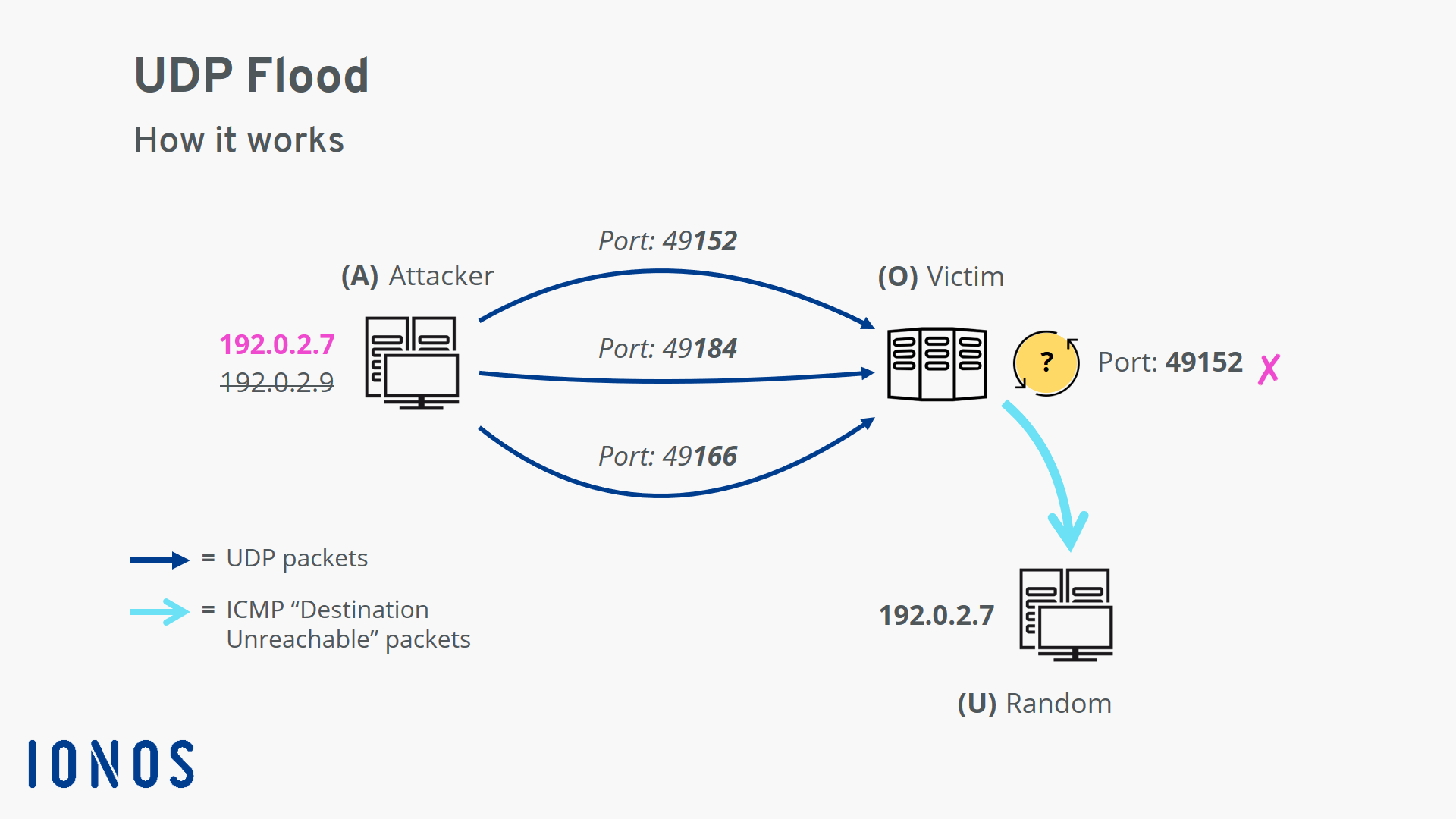
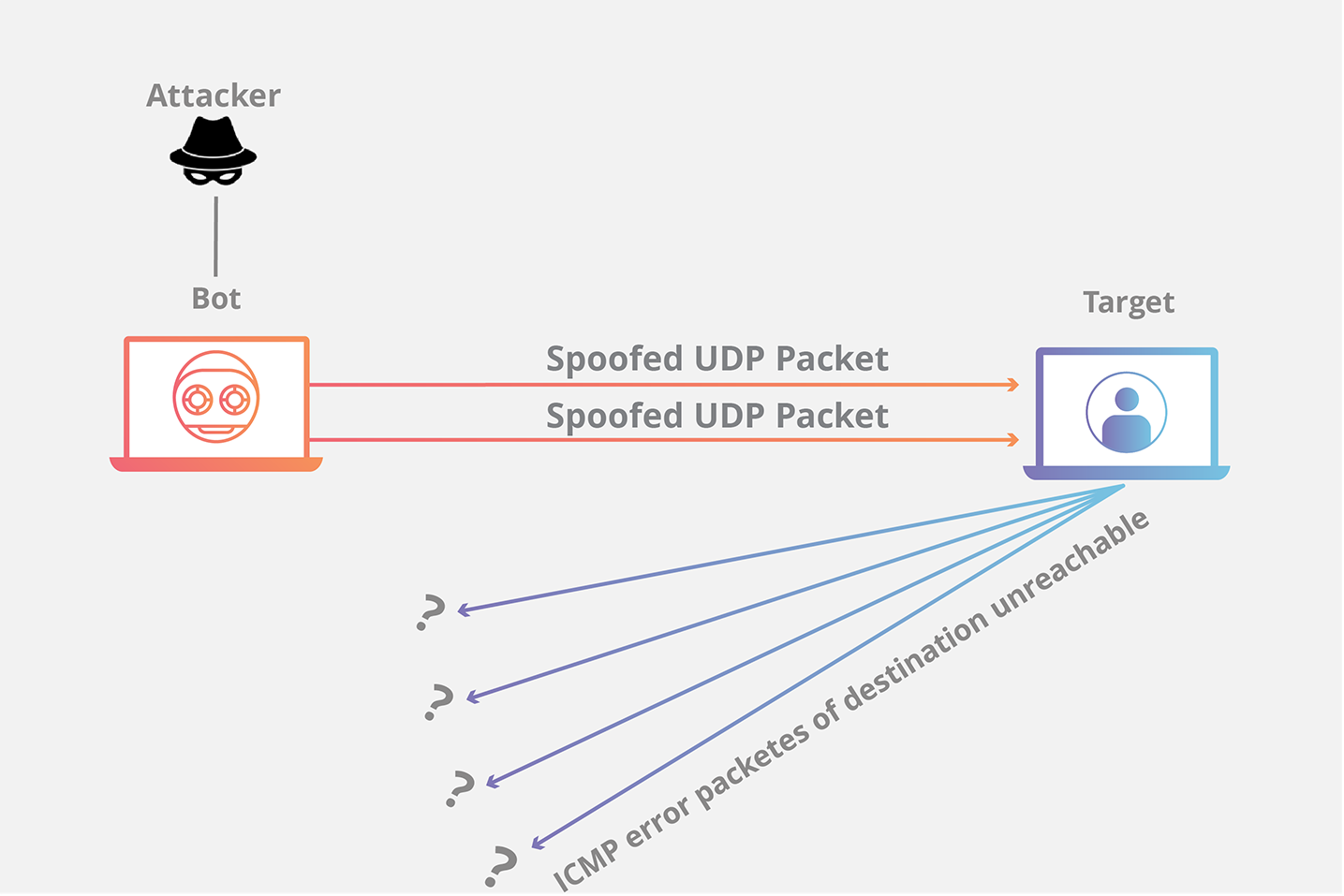
UDP Flood attack not interrupted and the two communicating hosts' will... | Download Scientific Diagram

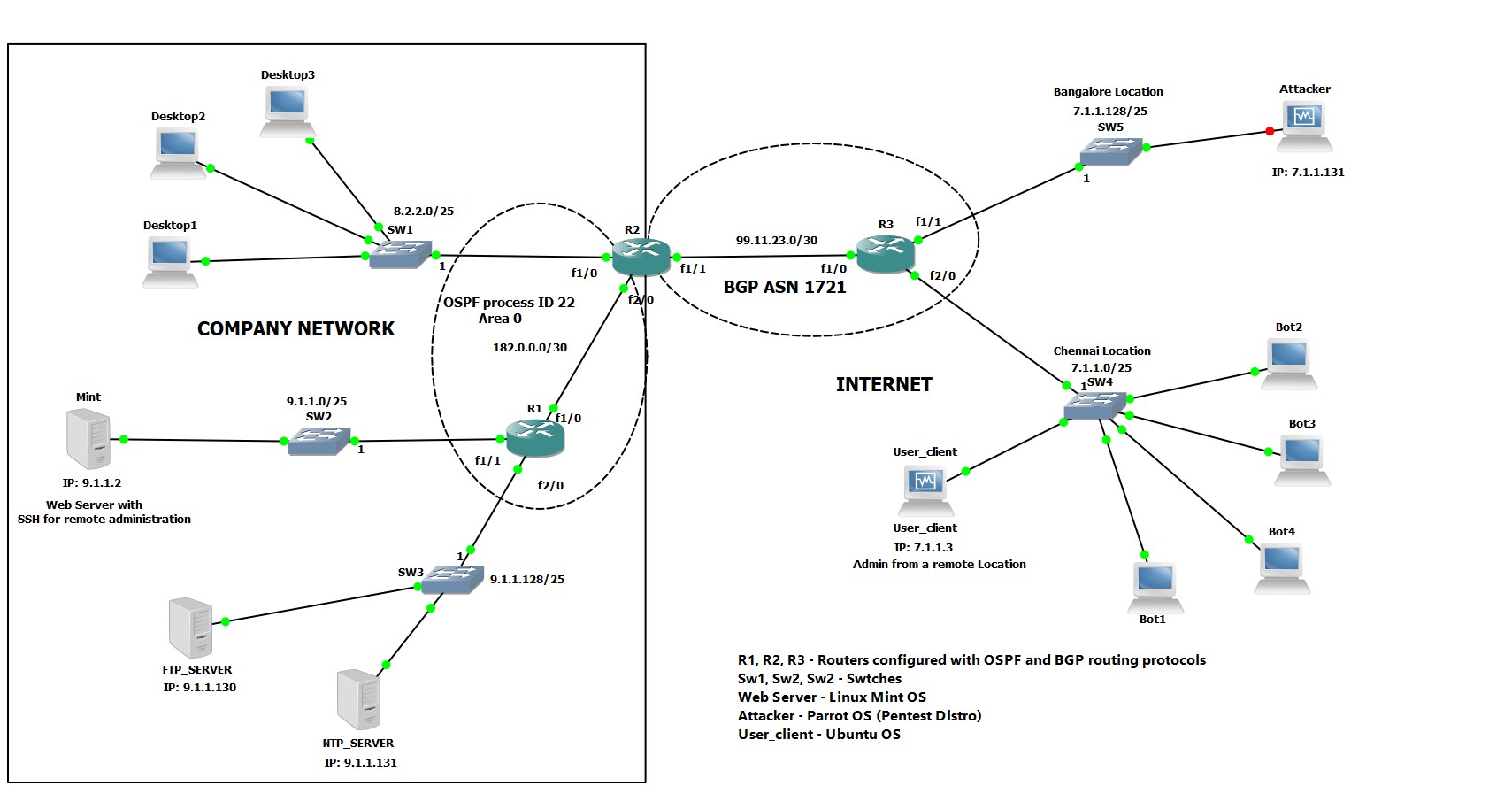
Detection and mitigation of UDP flooding attack in a multicontroller software defined network using secure flow management model - Gurusamy - 2019 - Concurrency and Computation: Practice and Experience - Wiley Online Library

First layer of SOM for classifying UDP flood attack using TCP SYN flood... | Download Scientific Diagram