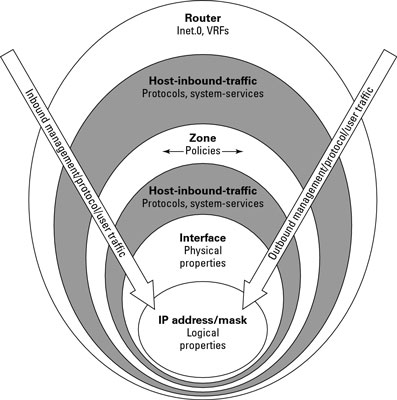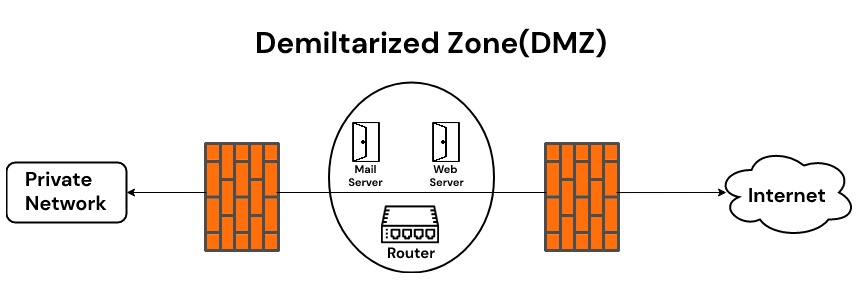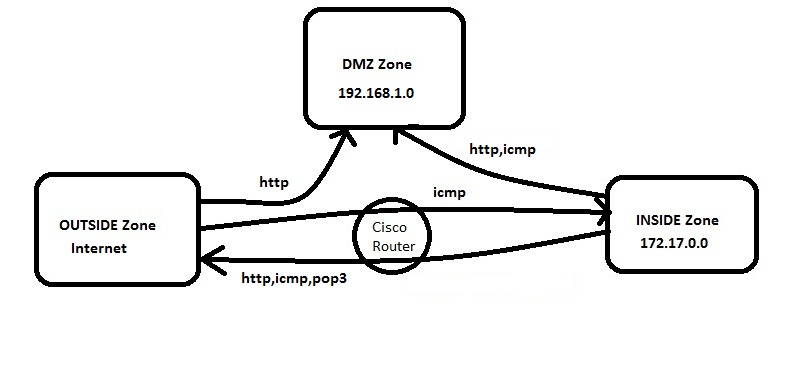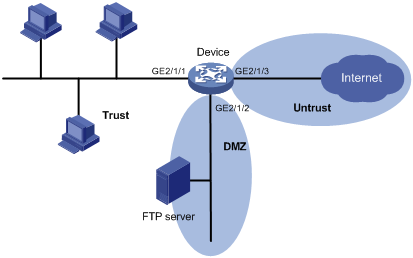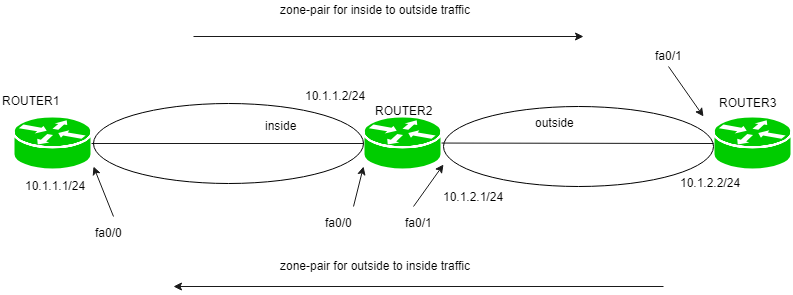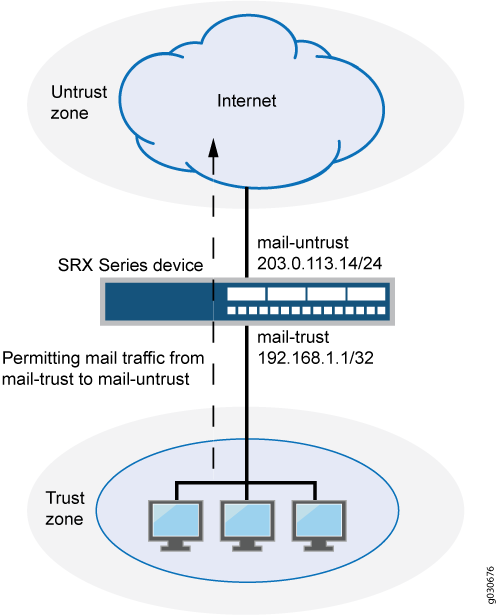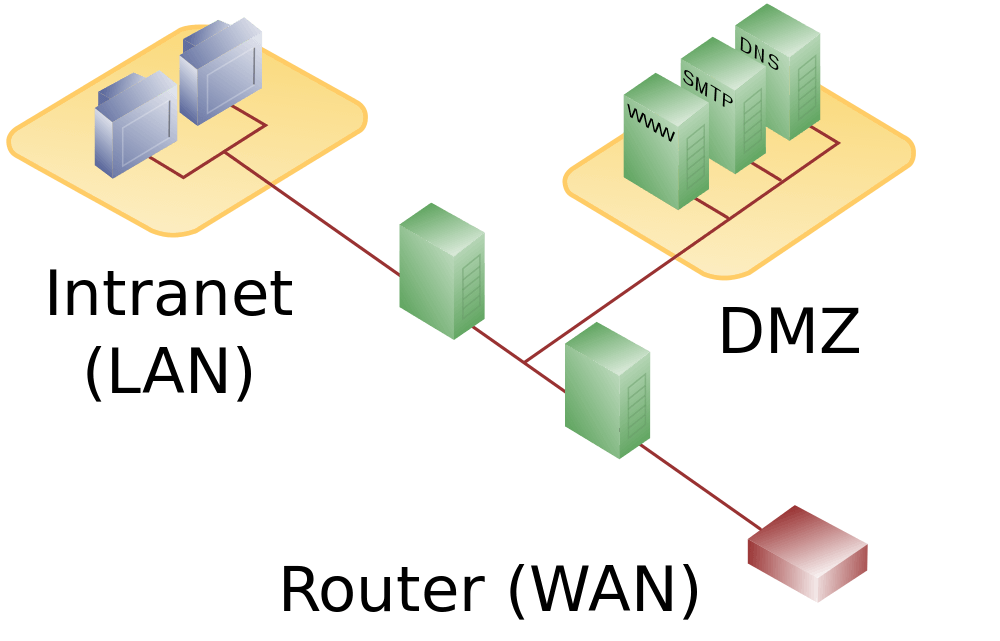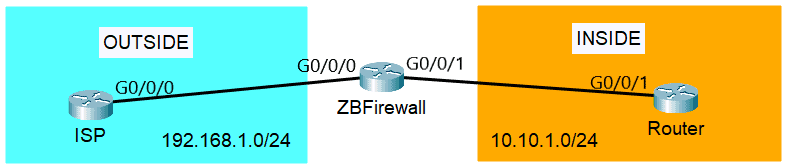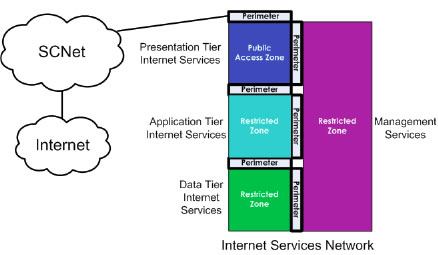
Network security zoning - Design considerations for placement of services within zones (ITSG-38) - Canadian Centre for Cyber Security

Realtime Security zone - COFE Presenting The Most Awaited 4G WiFi Router With External Voice Landline Support Fast 4G LTE Speed Share Your fast 4G LTE Category4 Mobile Internet Anywhere anytime. Support
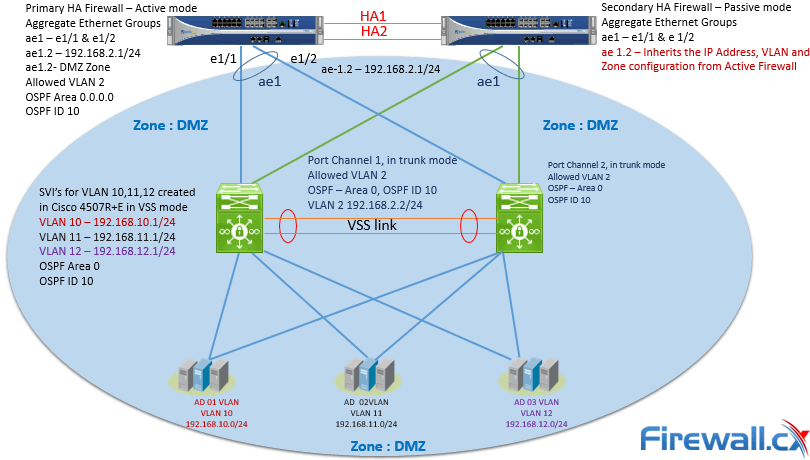
Security Policies Based on Zone Assignment for VPN Tunnel Inter... - Knowledge Base - Palo Alto Networks