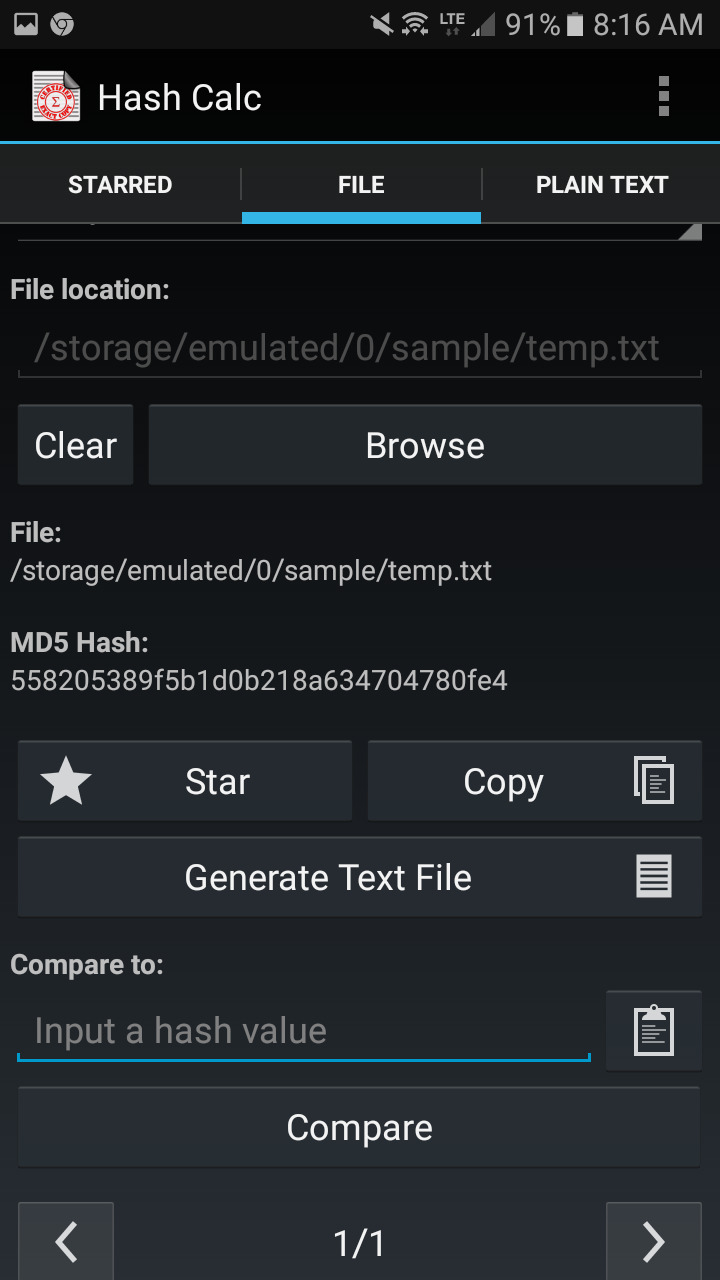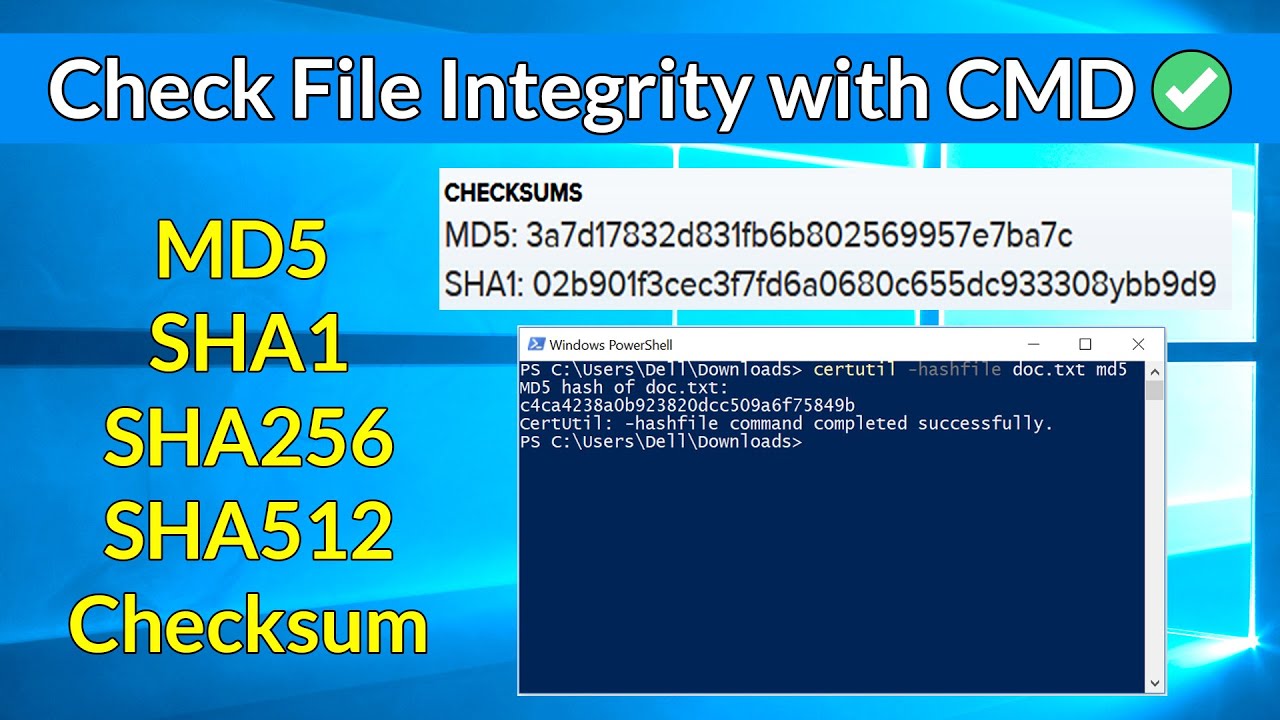
How to quickly verify MD5, SHA1 and SHA2 (256, 384, 512) Checksum in Windows using Command Prompt - YouTube
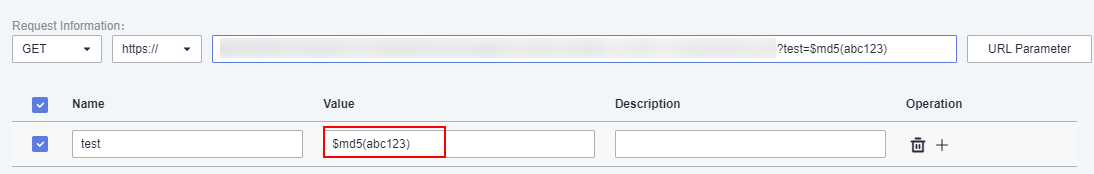
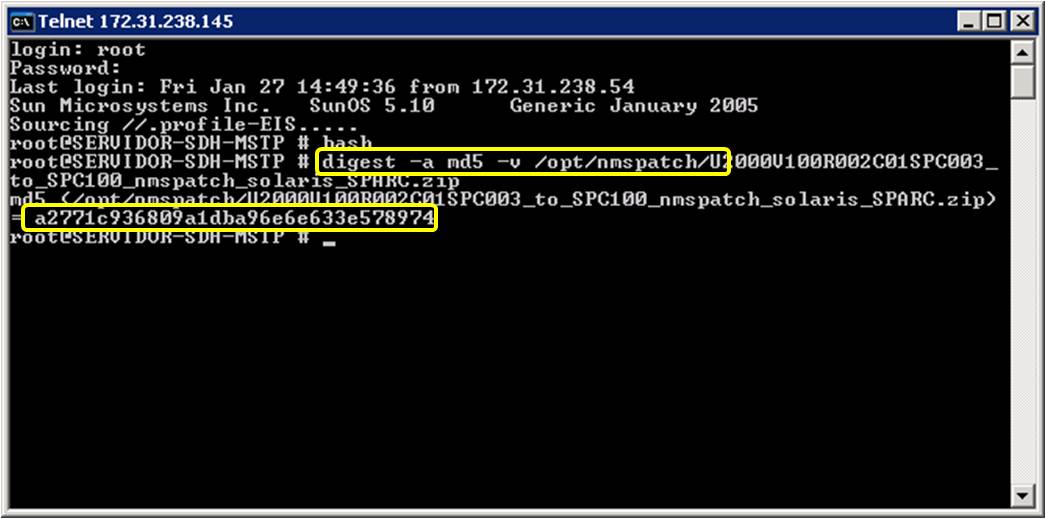
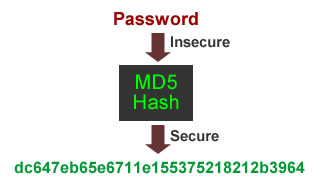
Generating an MD5 Hash Value_CodeArts TestPlan_User Guide_Test Case_Advanced Configurations of API Automation_Built-in Functions_Huawei Cloud
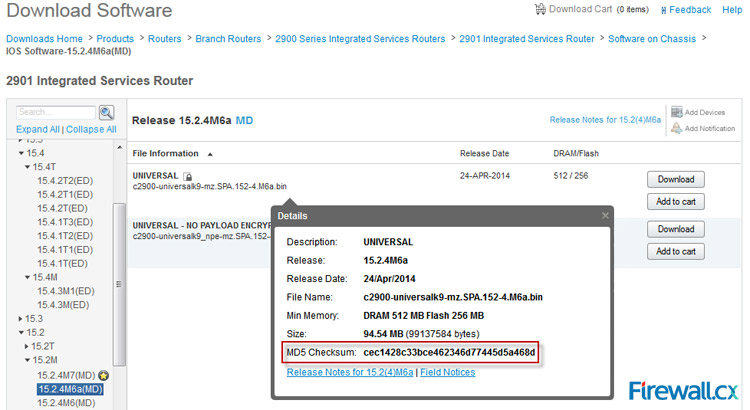
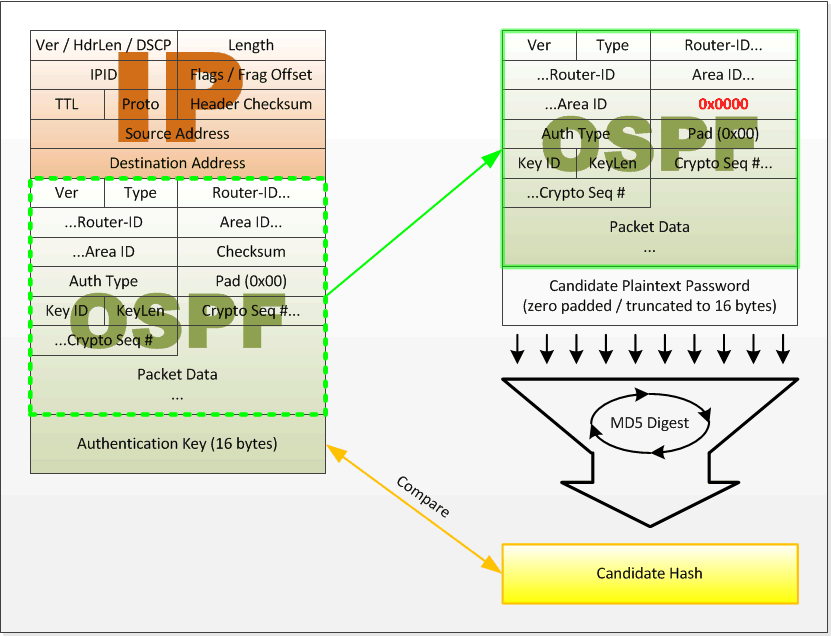
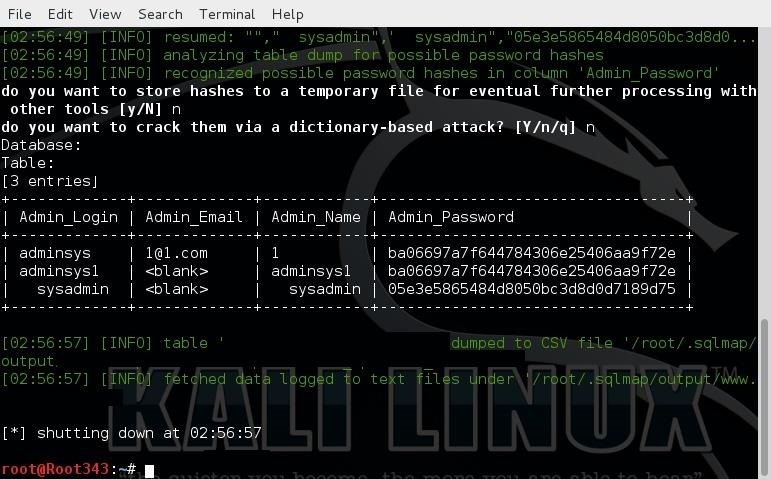
How and Why You Should Verify IOS Images On Cisco Routers & Catalyst Switches. Identify Corrupt & Tampered Images using SHA2 or MD5 Verification