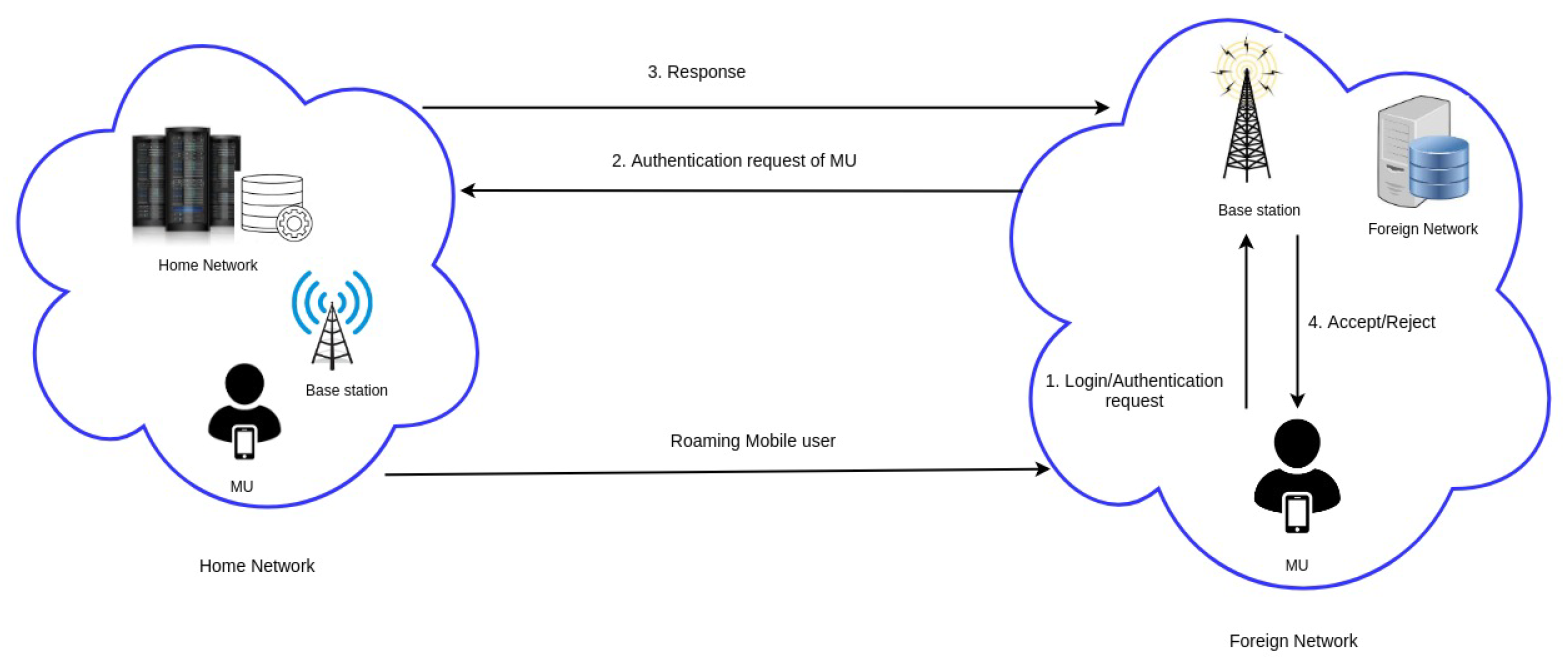
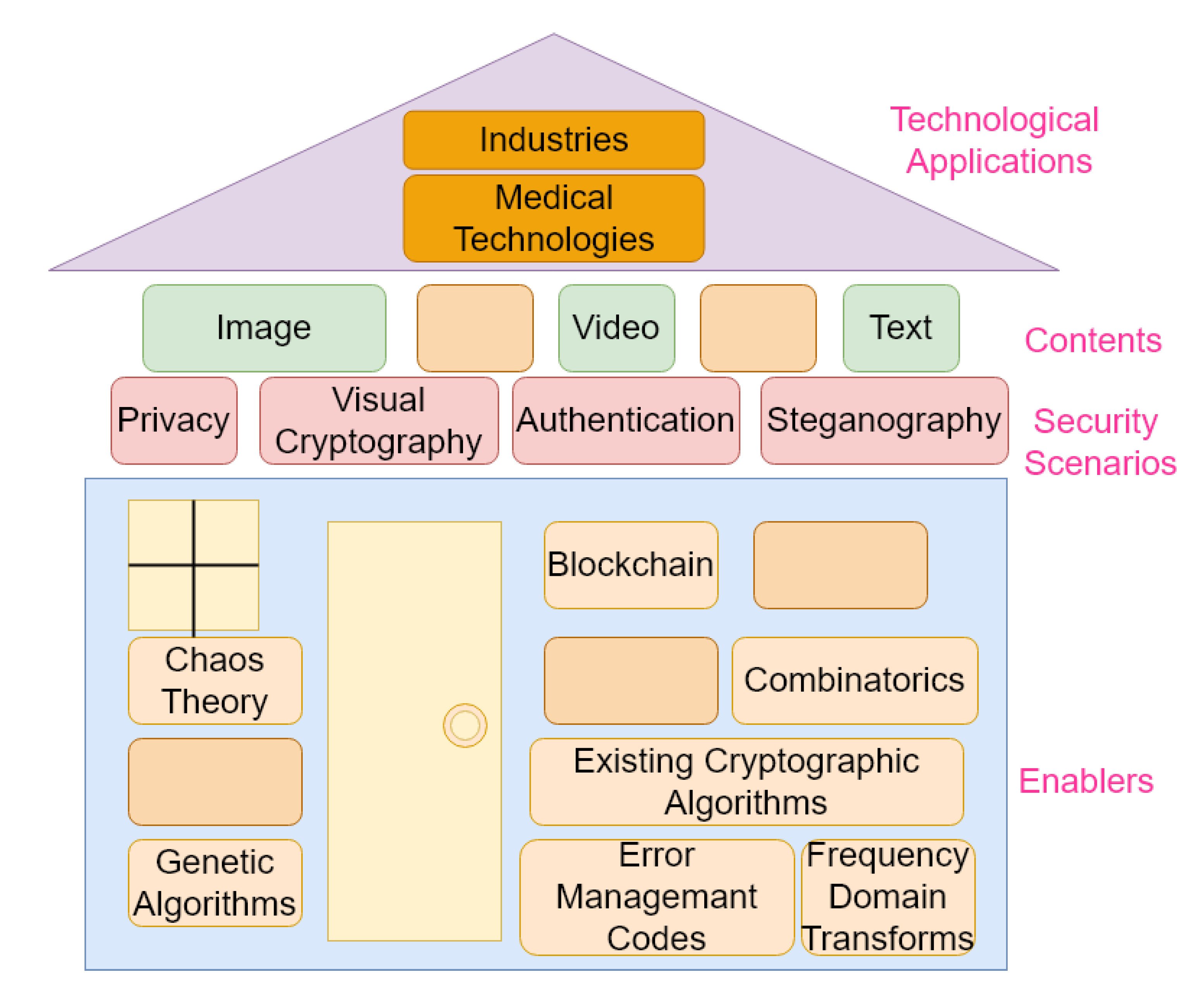
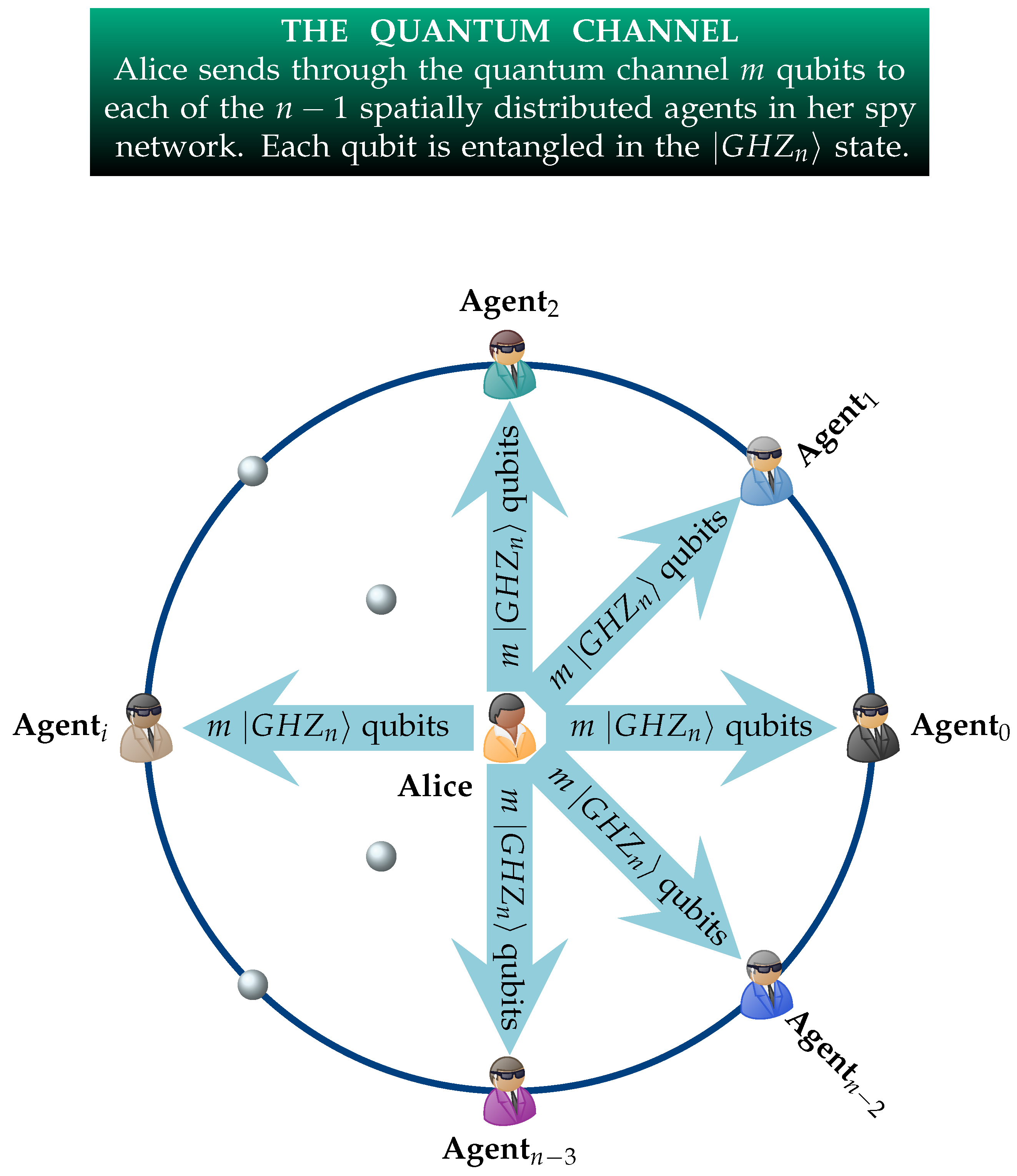
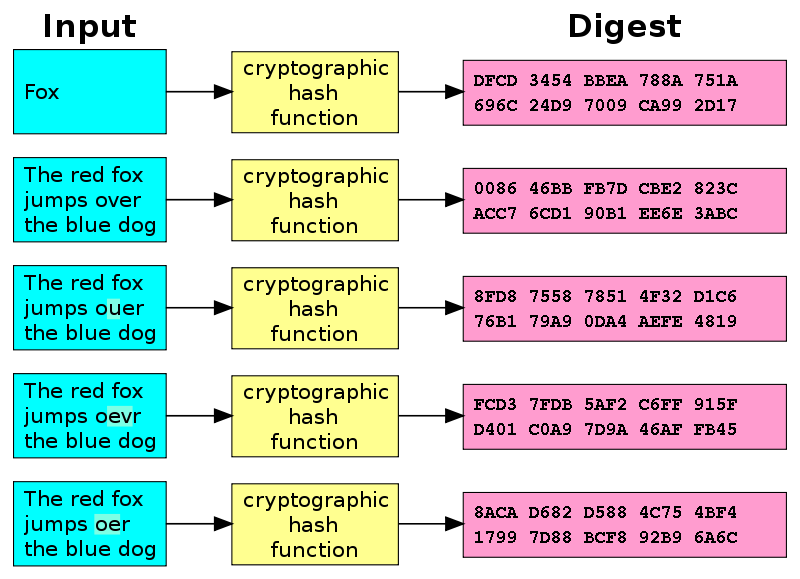
Sustainability | Free Full-Text | Quantum Key Distribution Protocol Selector Based on Machine Learning for Next-Generation Networks
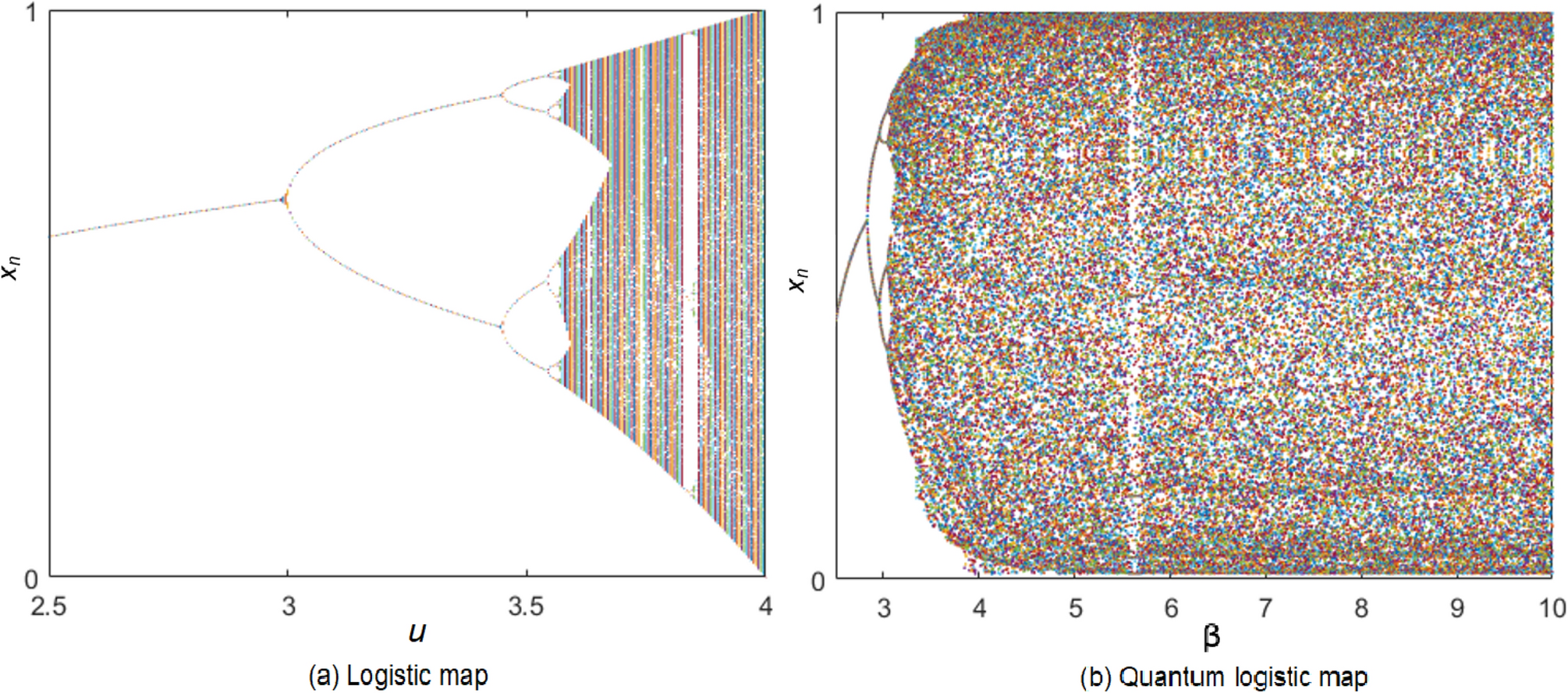
An image encryption scheme based on public key cryptosystem and quantum logistic map | Scientific Reports
A NOVEL CRYPTOSYSTEM BASED ON ABSTRACT AUTOMATA AND LATIN CUBES∗ 1. Introduction Automata theory provides a natural basis for
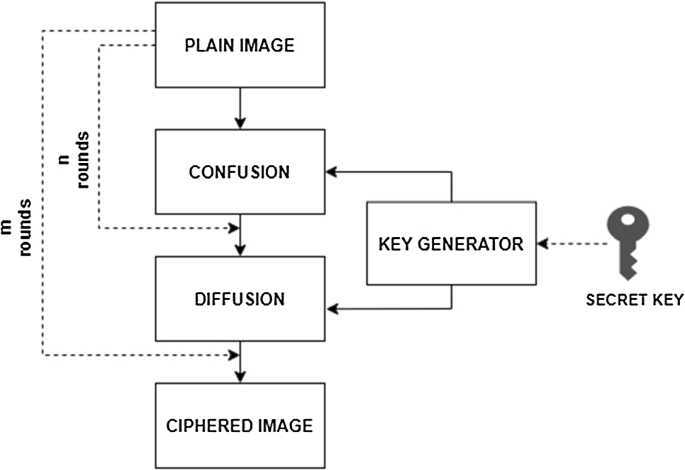
Survey on image encryption techniques using chaotic maps in spatial, transform and spatiotemporal domains | SpringerLink
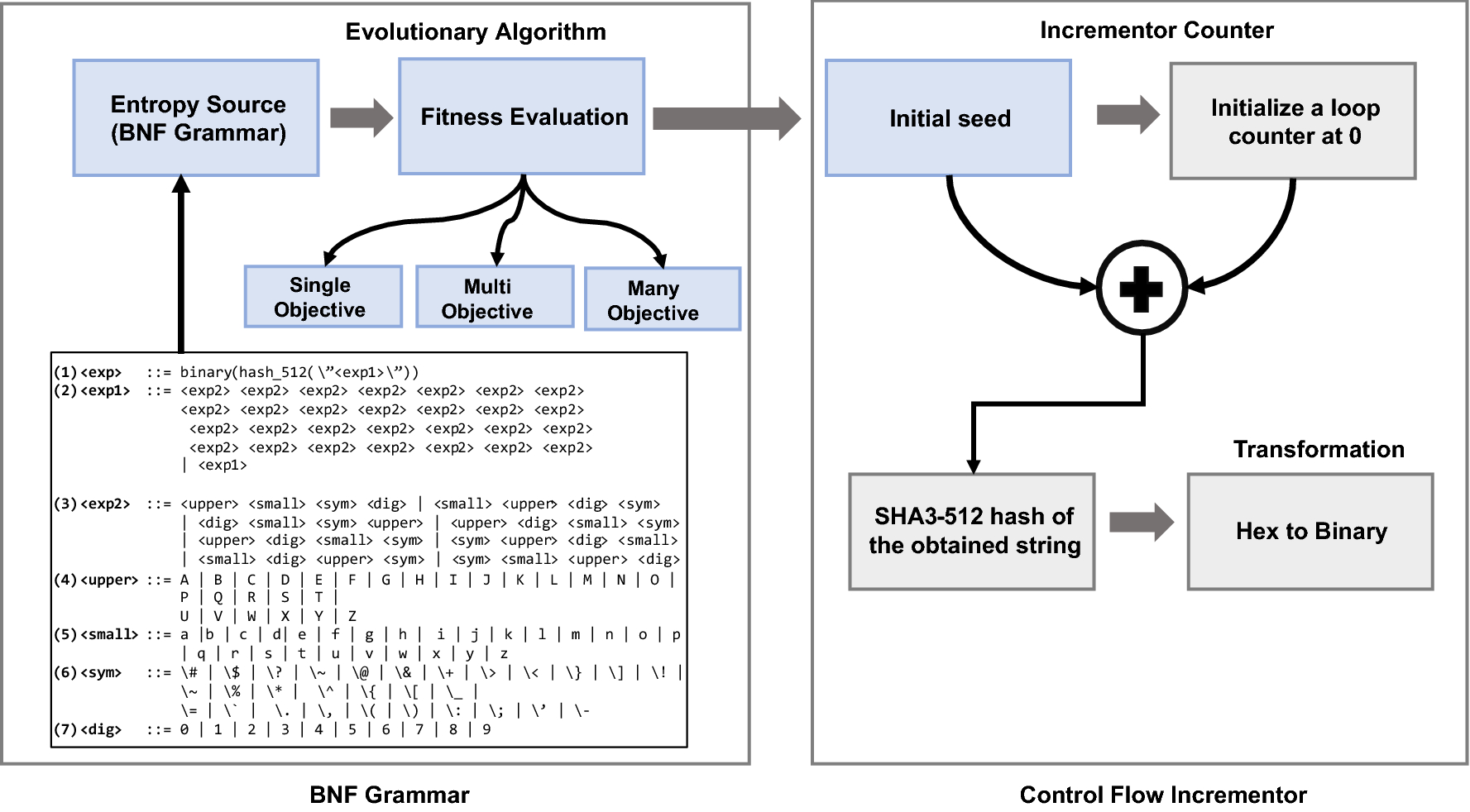
Design of a cryptographically secure pseudo random number generator with grammatical evolution | Scientific Reports

Correspondence between cellular automata and cryptography according to... | Download Scientific Diagram

Cryptographic models of nanocommunicaton network using quantum dot cellular automata: A survey - Debnath - 2021 - IET Quantum Communication - Wiley Online Library