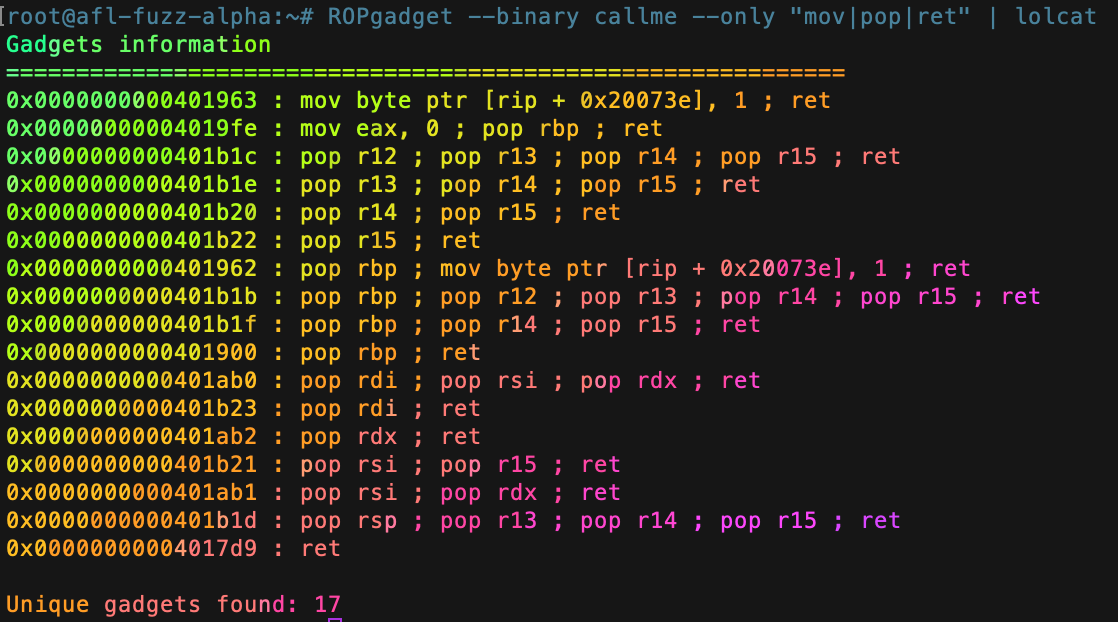
POP POP RET" T-shirt for Sale by NetworkEng | Redbubble | hacking t-shirts - assembly t-shirts - programming t-shirts

POP POP RET" T-shirt for Sale by NetworkEng | Redbubble | hacking t-shirts - assembly t-shirts - programming t-shirts
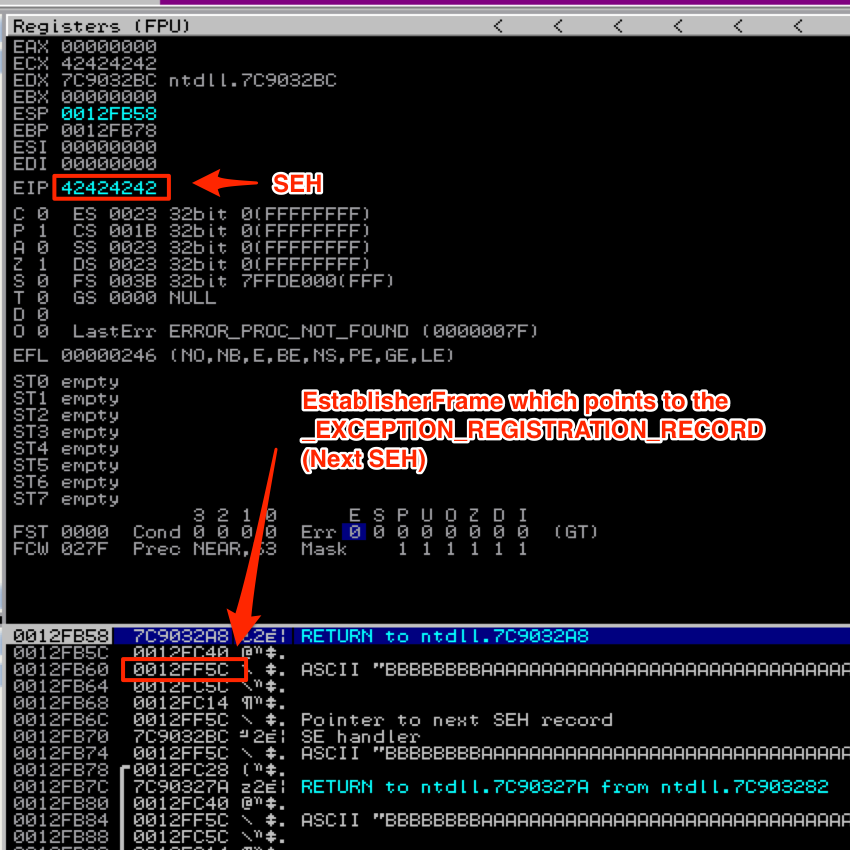
GitHub - ancat/ppr-finder: A WinDbg script to find pop-pop-ret sequences within a module loaded in memory


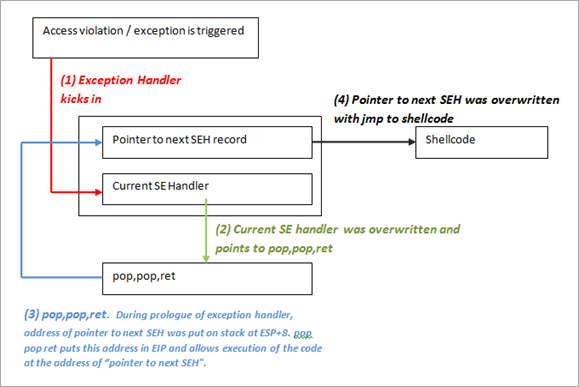




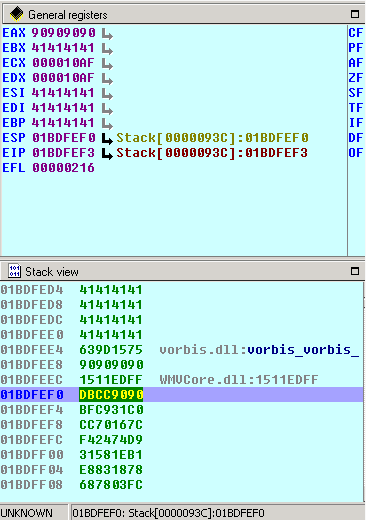
![Lab 08 - Return-Oriented Programming [CS Open CourseWare] Lab 08 - Return-Oriented Programming [CS Open CourseWare]](https://ocw.cs.pub.ro/courses/_media/cns/labs/drawing4.png?w=600&tok=0eb20d)