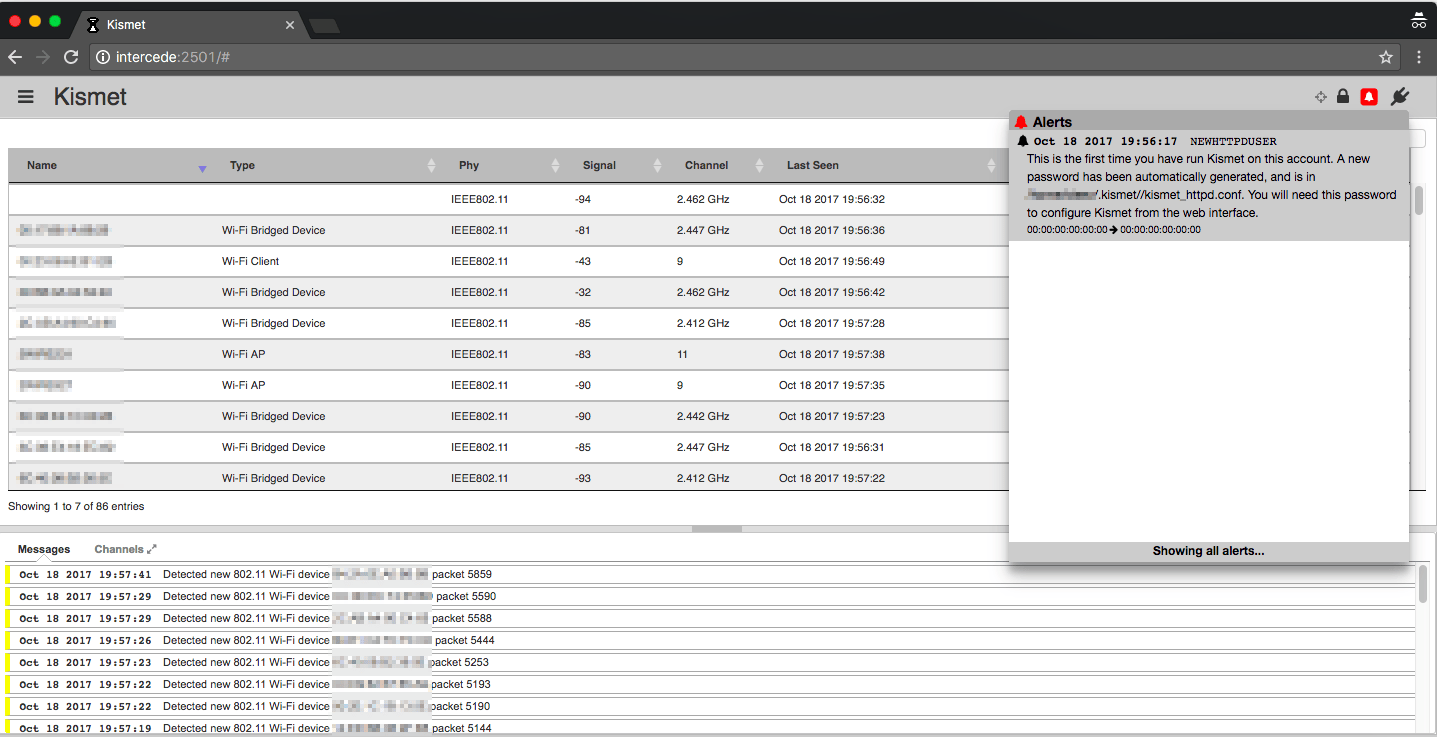
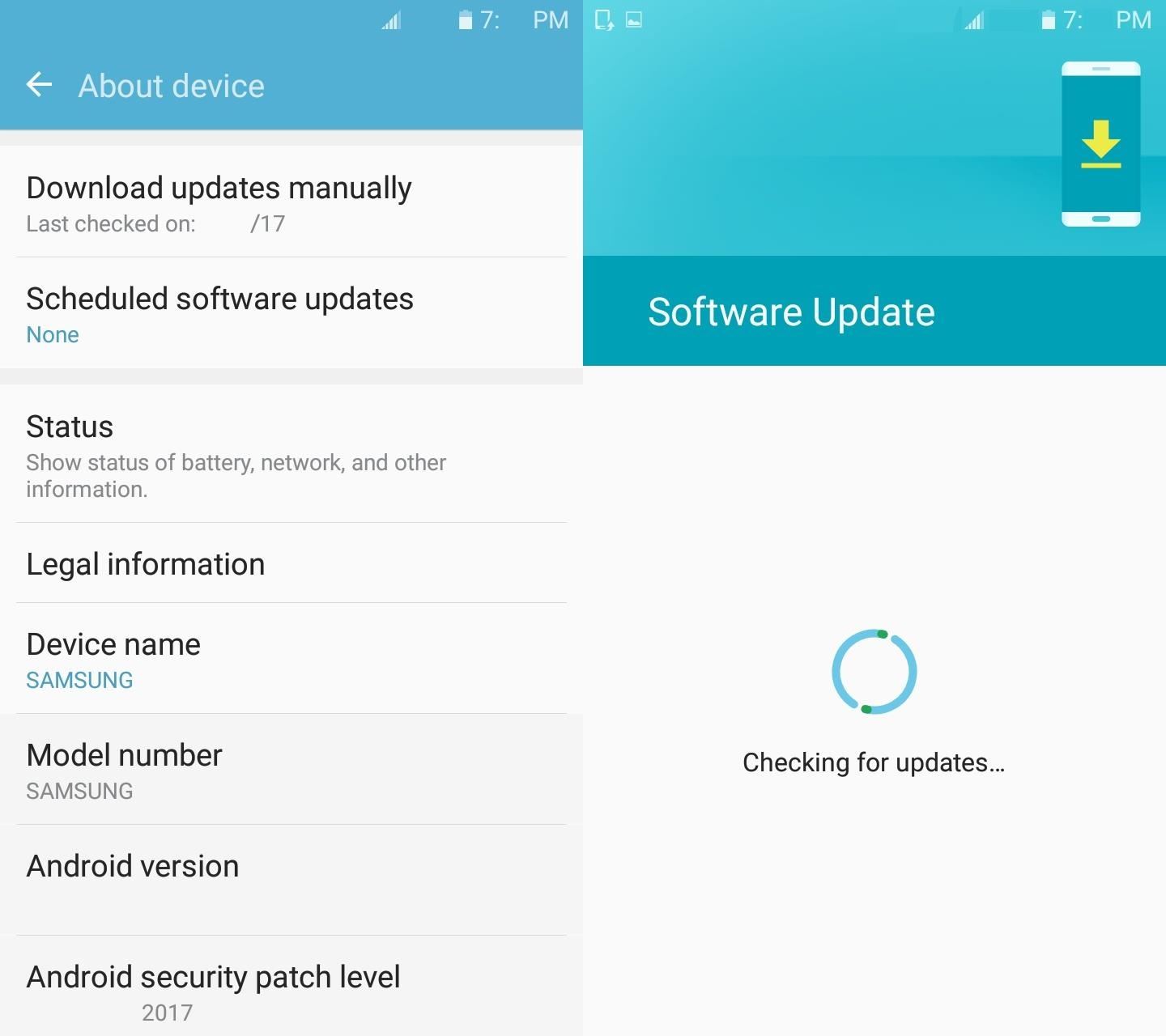
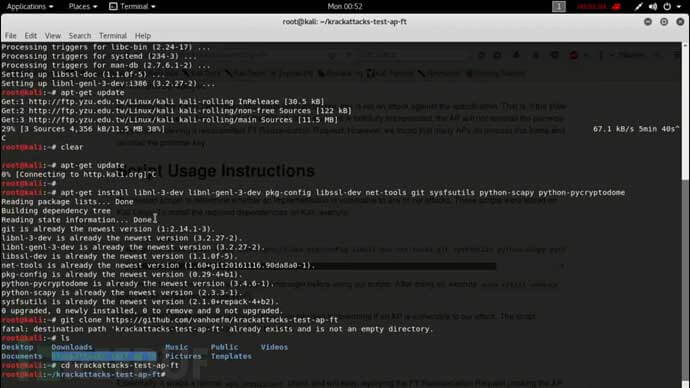
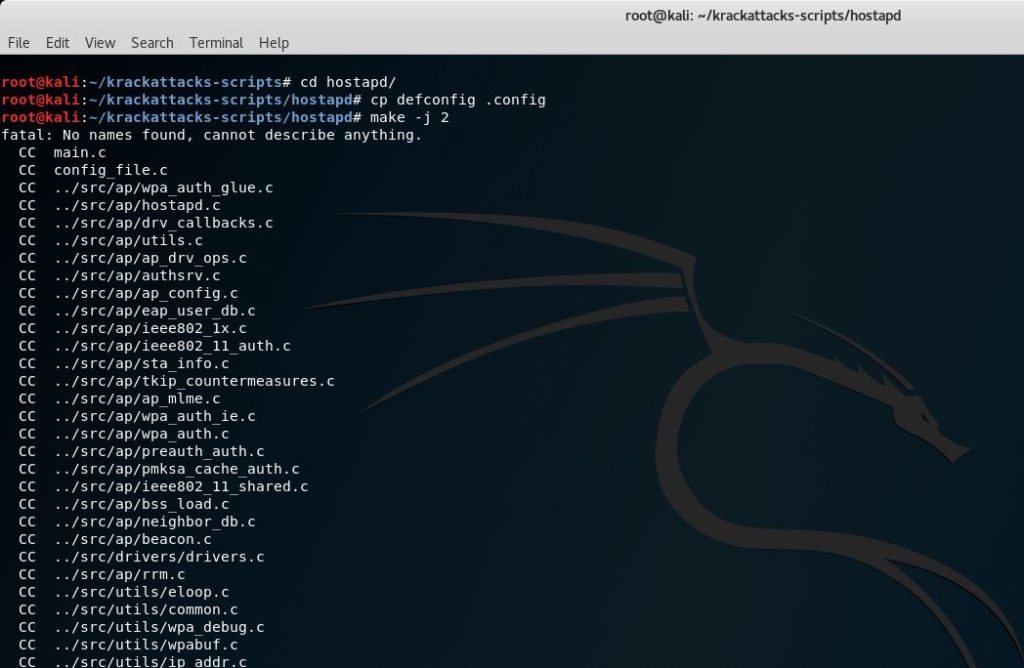
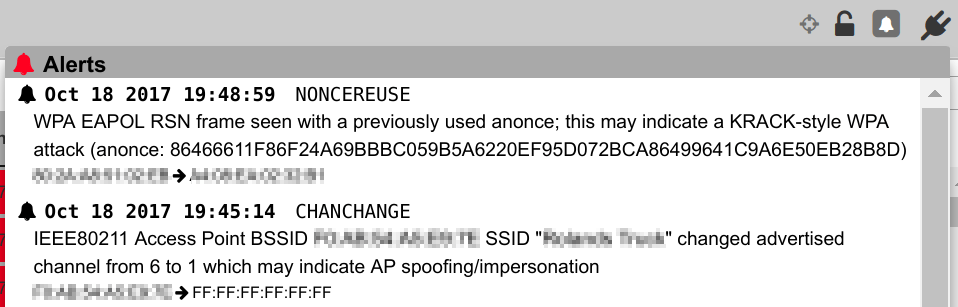
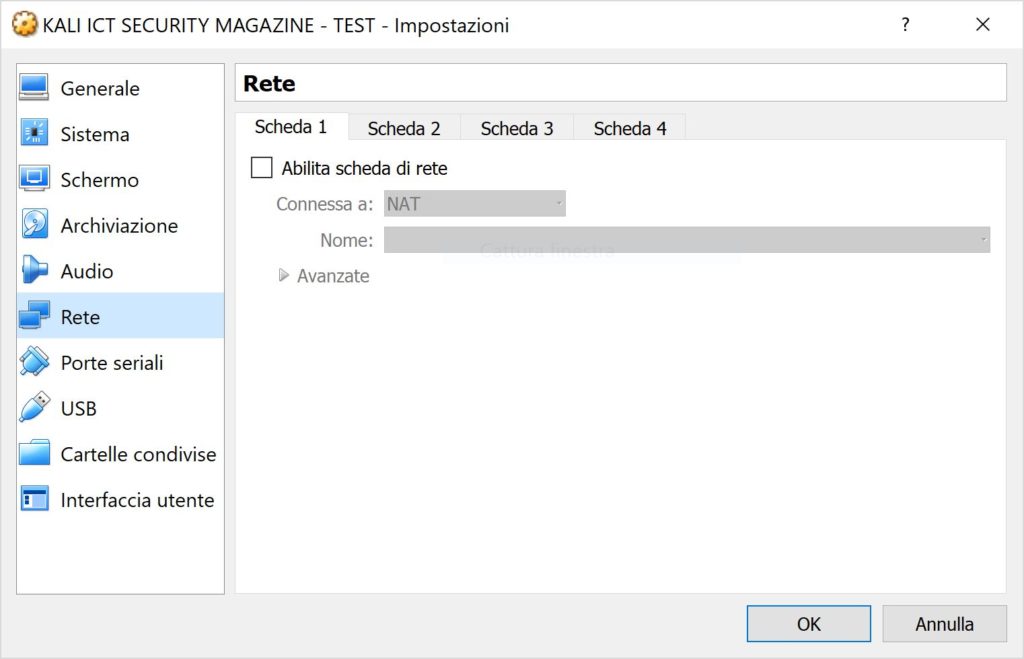
KRACK Kali Vulnerability Test - Test Your WiFi Router for KRACK (FT) - Arduino Projects and Robotics Tutorial
KRACK Kali Vulnerability Test - Test Your WiFi Router for KRACK (FT) - Arduino Projects and Robotics Tutorial

KRACK Kali Vulnerability Test - Test Your WiFi Router for KRACK (FT) - Arduino Projects and Robotics Tutorial

Amazon | Kali Linux Wireless Penetration Testing Beginner's Guide - Third Edition: Master wireless testing techniques to survey and attack wireless networks with Kali Linux, including the KRACK attack | Buchanan, Cameron,

Release the KRACKen: WPA2 Wi-Fi Encryption Hackable Until All Clients & APs Are Patched « Null Byte :: WonderHowTo