Kali Linux: Professional Penetration-Testing Distro - HostDime India Blog - Managed Dedicated Servers and Data Centers

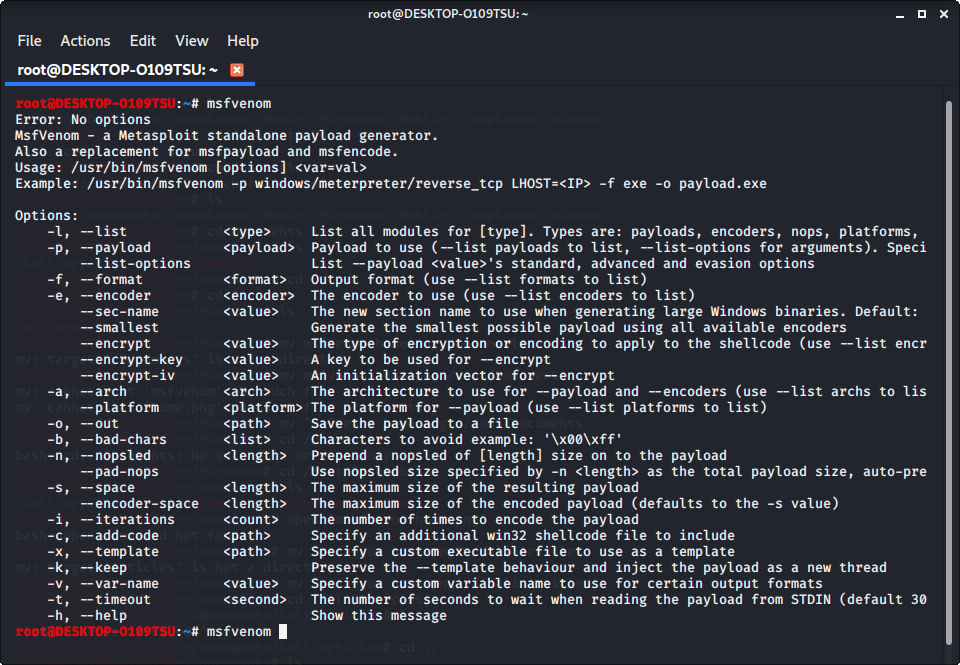
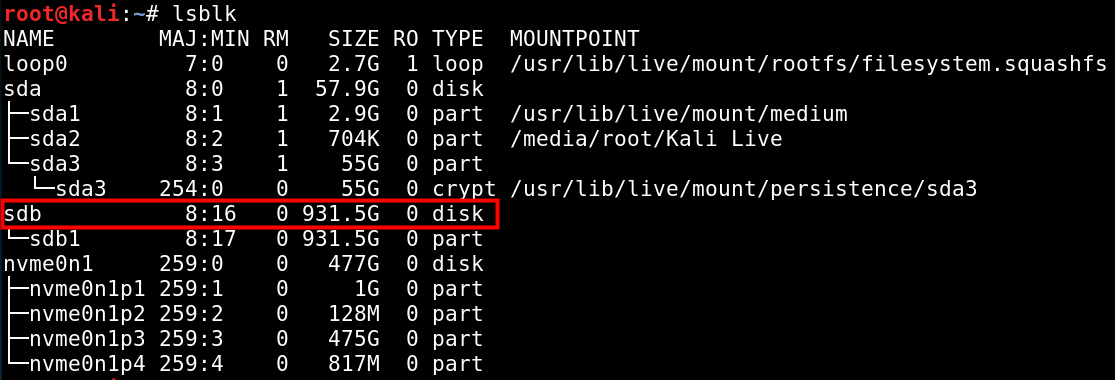
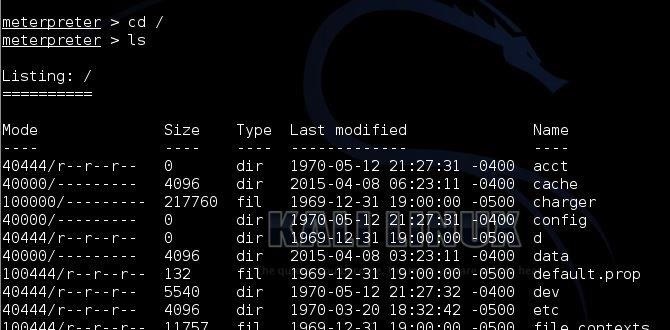
Kali Linux: Full Disk Encryption with Plausible Deniability and Detached LUKS Header on Encrypted USB Boot Drive
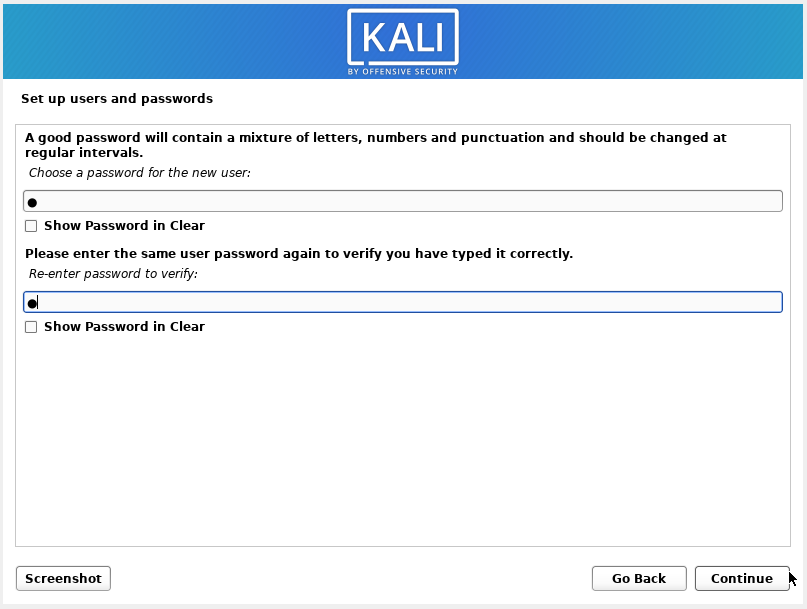
How to install Kali Linux with full disk encryption or encrypted user's home folder - Ethical hacking and penetration testing