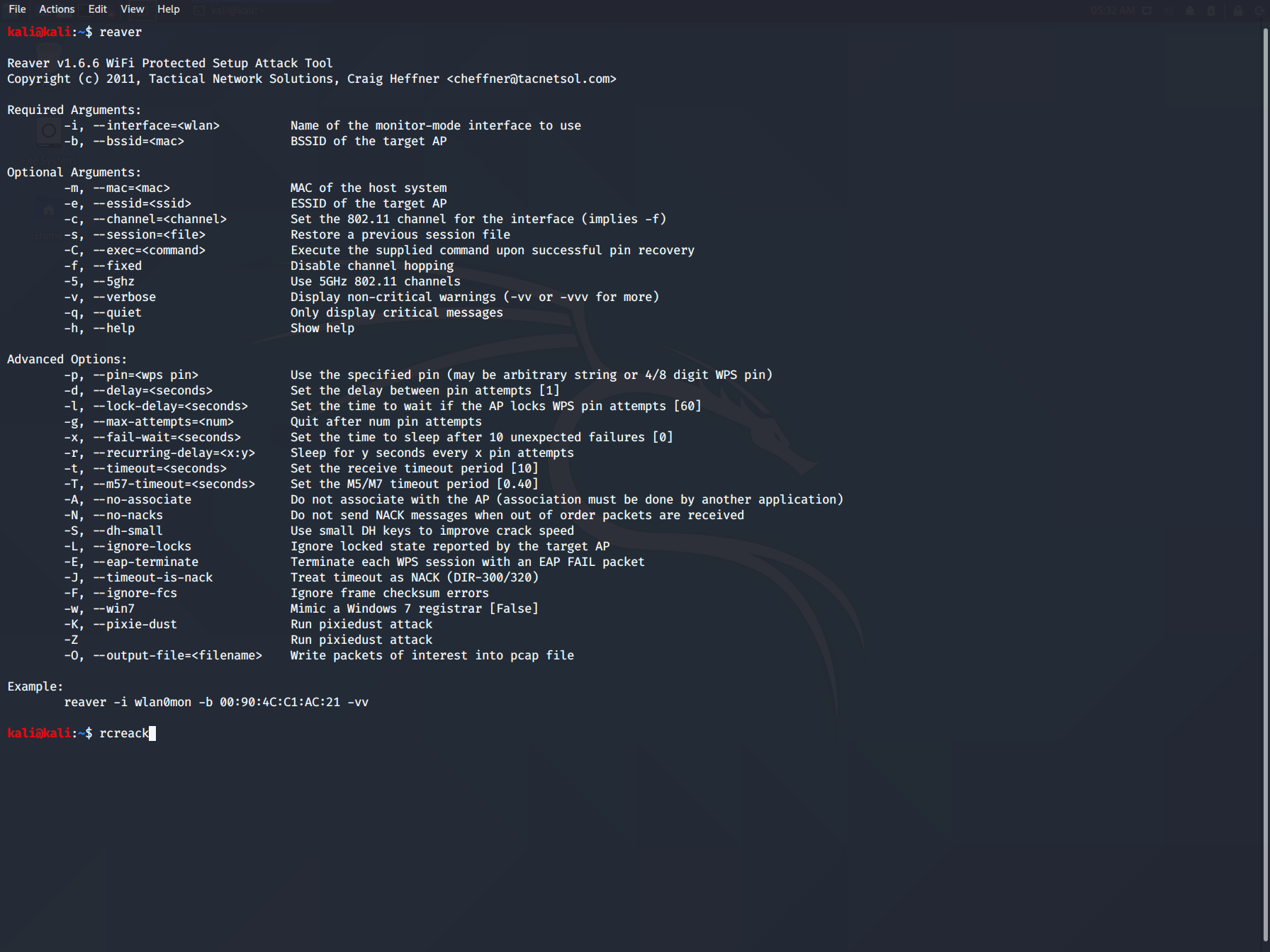
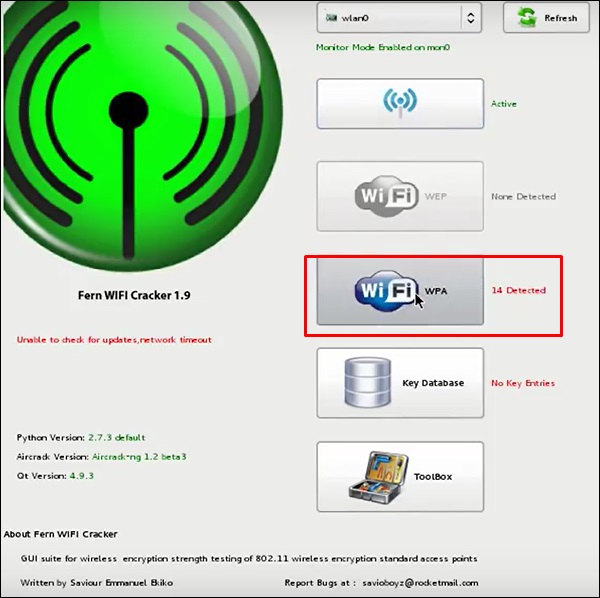
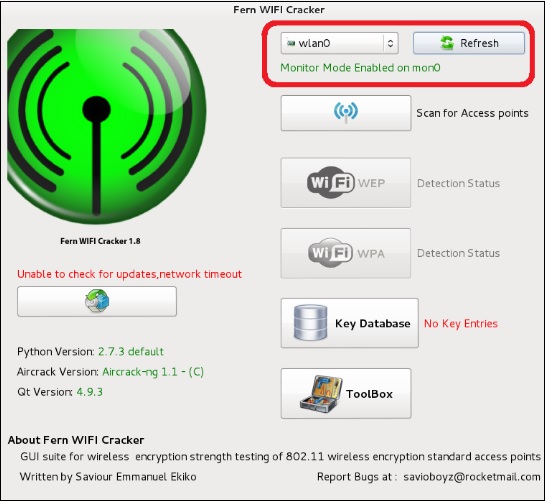
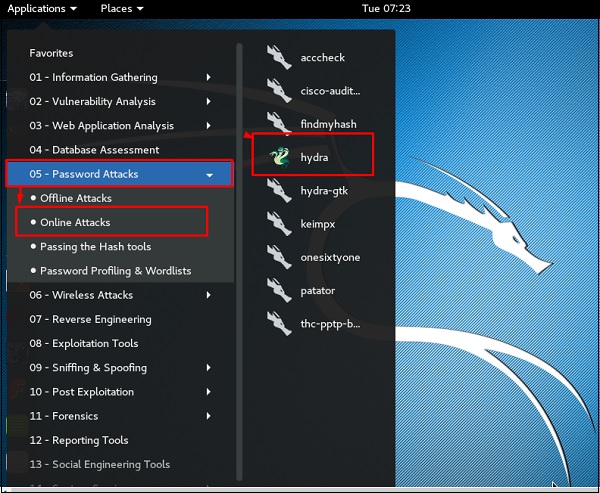
Kali Linux Wireless Penetration Testing: Beginner's Guide: Master wireless testing techniques to survey and attack wireless networks with Kali Linux : Ramachandran, Vivek, Buchanan, Cameron: Amazon.in: Books
![Creating a Spear-Phishing Attack with the Social Engineering Toolkit - Kali Linux 2: Windows Penetration Testing [Book] Creating a Spear-Phishing Attack with the Social Engineering Toolkit - Kali Linux 2: Windows Penetration Testing [Book]](https://www.oreilly.com/api/v2/epubs/9781782168492/files/graphics/B00248_08_025-1.jpg)
Creating a Spear-Phishing Attack with the Social Engineering Toolkit - Kali Linux 2: Windows Penetration Testing [Book]

DDOS ATTACK WITH WEBSITE USING KALI LINUX _2019 | DDOS ATTACK WITH WEBSITE USING KALI LINUX _2019 Ahmed Production Limited | By Cyber Haxer Crew | Facebook

Amazon.co.jp: Kali Linux Wireless Penetration Testing Beginner's Guide - Third Edition: Master wireless testing techniques to survey and attack wireless networks with Kali Linux, including the KRACK attack : Buchanan, Cameron, Ramachandran,