Tor and the Dark Art of Anonymity (deep web, kali linux, hacking, bitcoins) Defeat NSA Spying - Segurança em Tecnologia da Informa

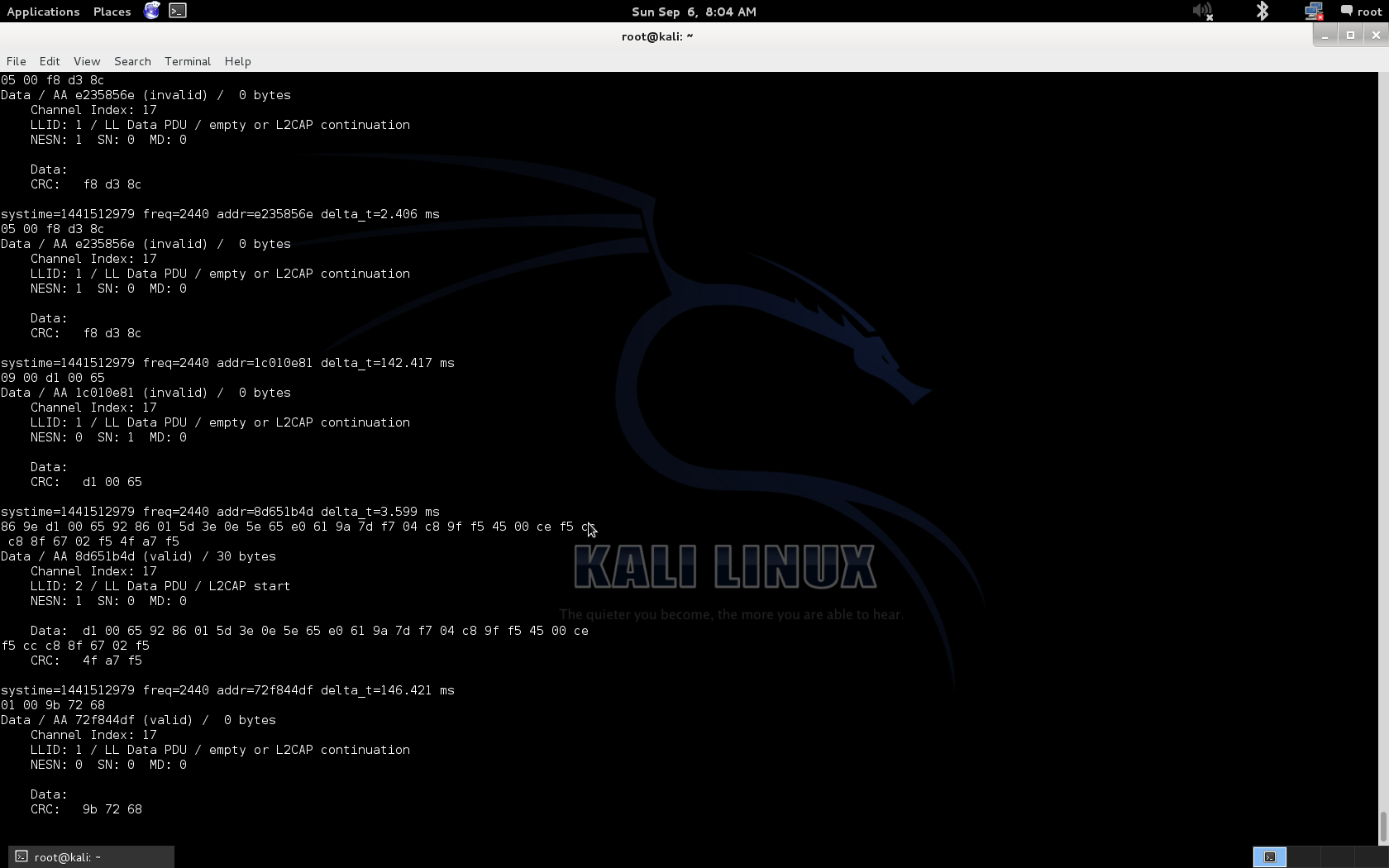
Sophisticated Spearphishing Campaign Targets Government Organizations, IGOs, and NGOs - blackMORE Ops

Linux Basics for Hackers: Getting Started with Networking, Scripting, and Security in Kali: OccupyTheWeb: 9781593278557: Books - Amazon.ca