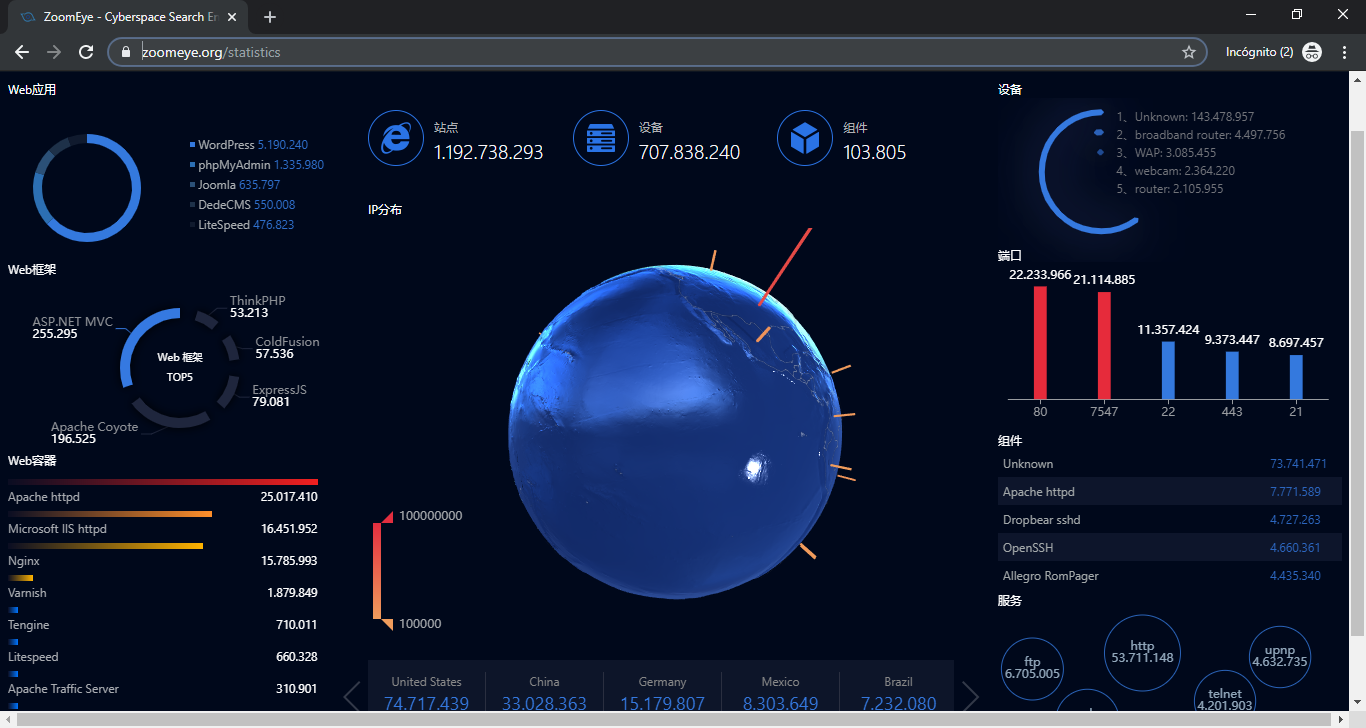
The best Internet search engines used by hackers | Ma-No Tech News & Analysis, javascript, angular, react, vue, php
GitHub - cve-search/cve-search: cve-search - a tool to perform local searches for known vulnerabilities
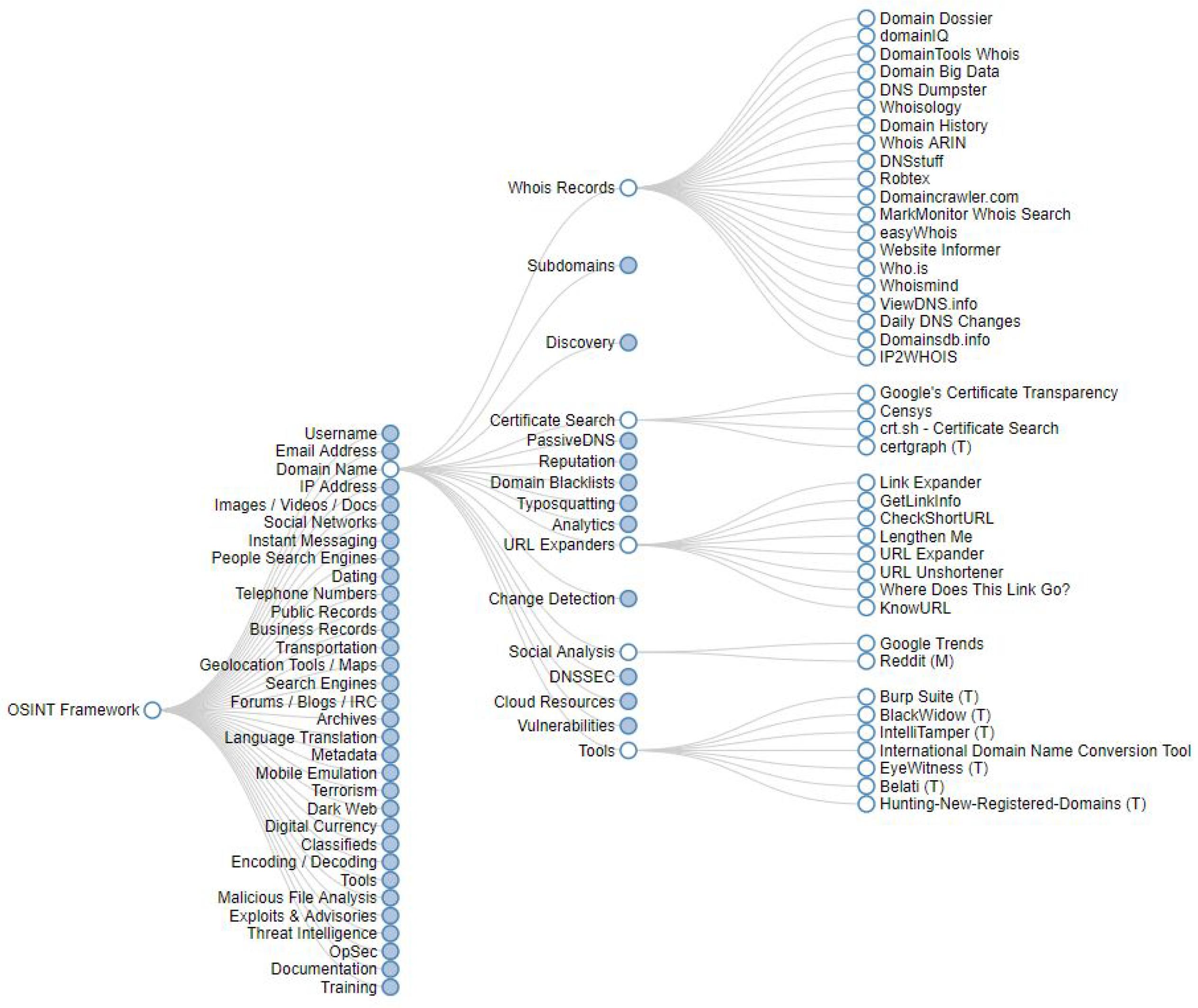
Mathematics | Free Full-Text | Mapping Tools for Open Source Intelligence with Cyber Kill Chain for Adversarial Aware Security
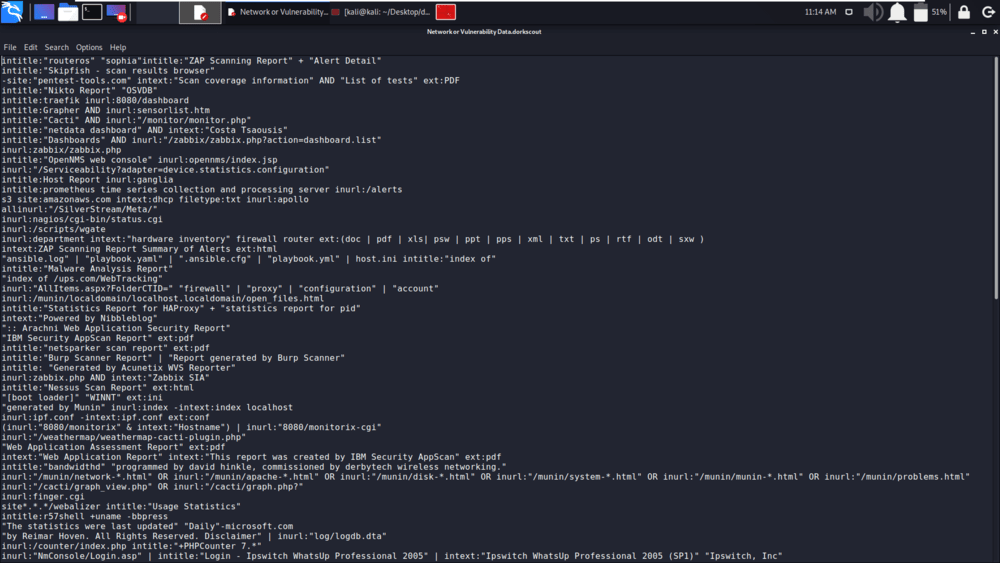
DorkScout - Automate google dork scan against the entire internet or specific targets - GeeksforGeeks
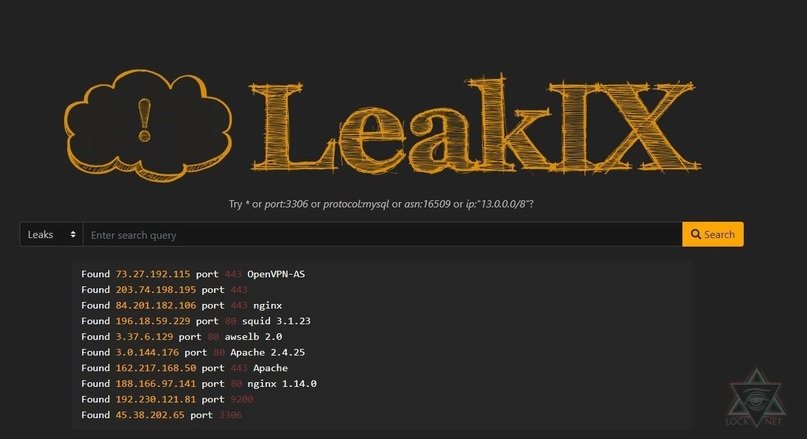
How to use Leakix, the new search engine for cybersecurity professionals that makes it easier to detect vulnerable devices
![YouSearch interface] A user browsing a YouSearch enabled website can... | Download Scientific Diagram YouSearch interface] A user browsing a YouSearch enabled website can... | Download Scientific Diagram](https://www.researchgate.net/publication/2559505/figure/fig1/AS:279328152670210@1443608429216/YouSearch-interface-A-user-browsing-a-YouSearch-enabled-website-can-issue-queries-using.png)