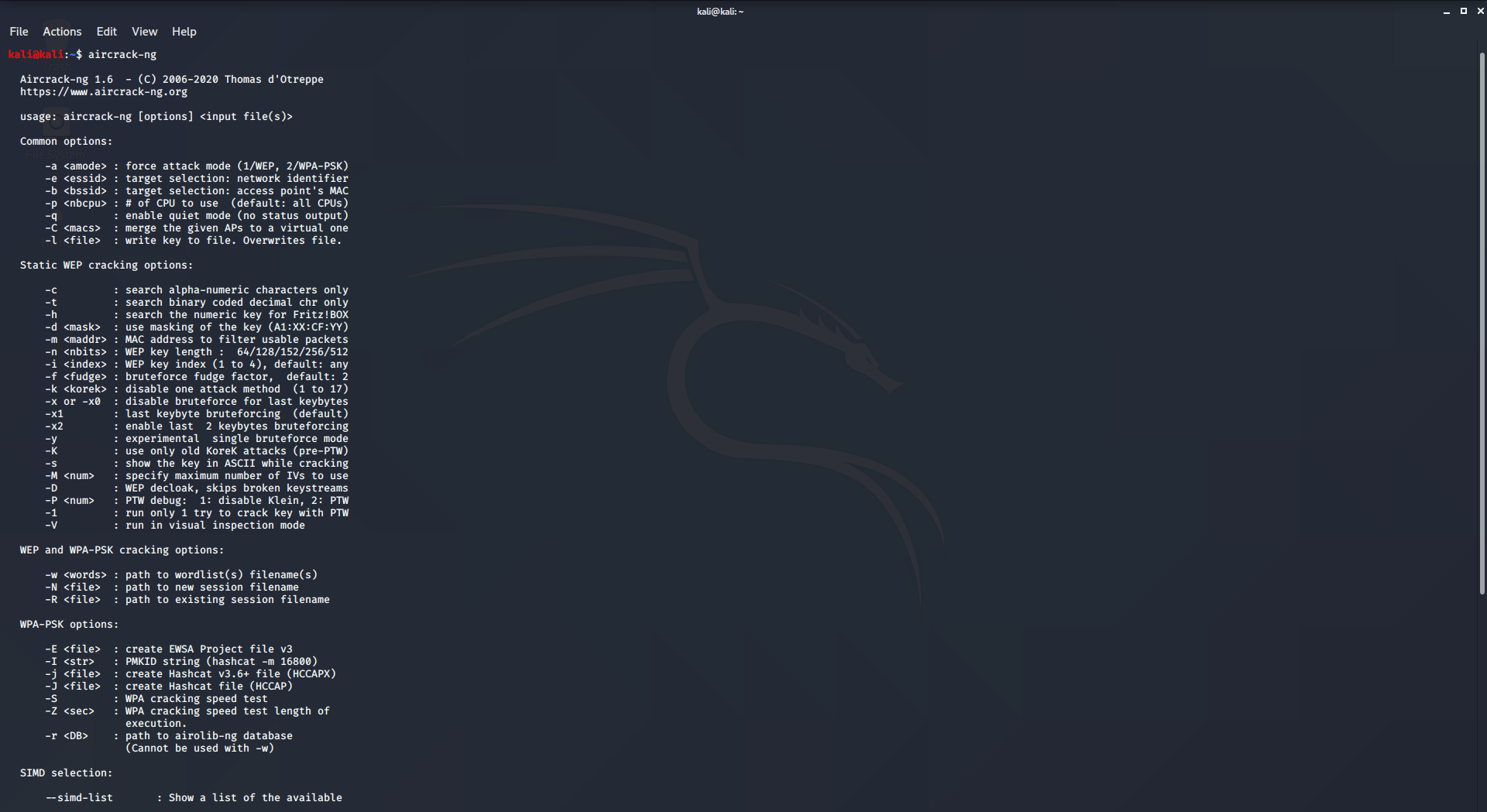
FinSpy (aka FinFisher) spyware for Windows, macOS, Linux, Android, and iOS | Kaspersky official blog

Hands-On Penetration Testing with Kali NetHunter: Spy on and protect vulnerable ecosystems using the power of Kali Linux for pentesting on the go 1, Singh, Glen D., Oriyano, Sean-Philip, eBook - Amazon.com








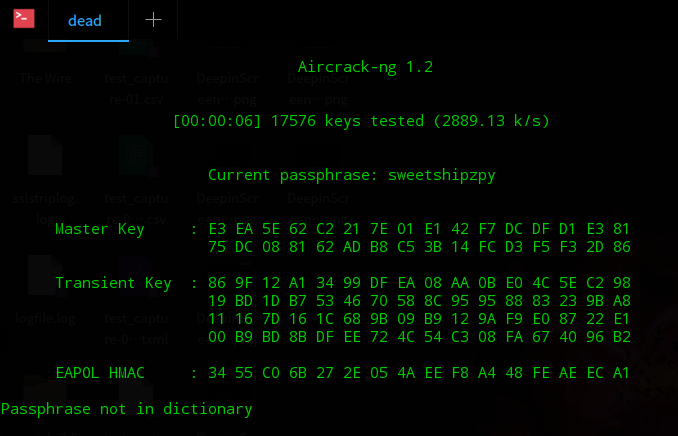
![Spy on Network Relationships with Airgraph-ng [Tutorial] - YouTube Spy on Network Relationships with Airgraph-ng [Tutorial] - YouTube](https://i.ytimg.com/vi/noCaFsvgRX0/maxresdefault.jpg)