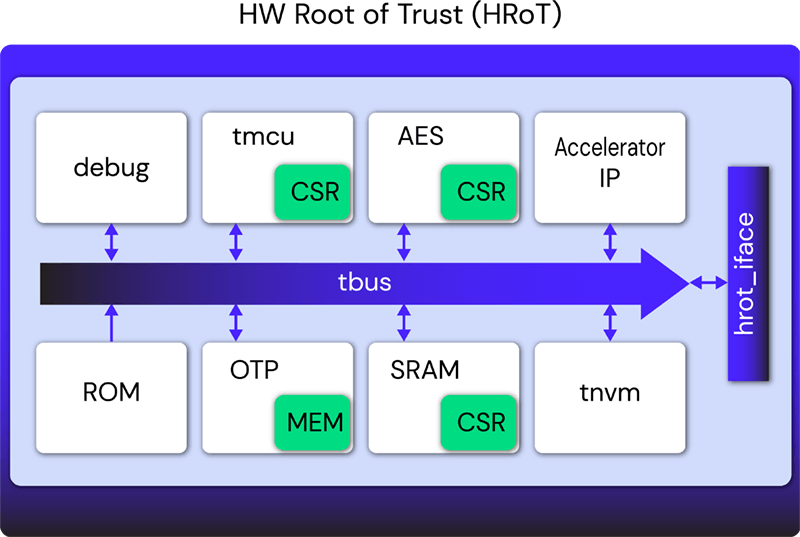
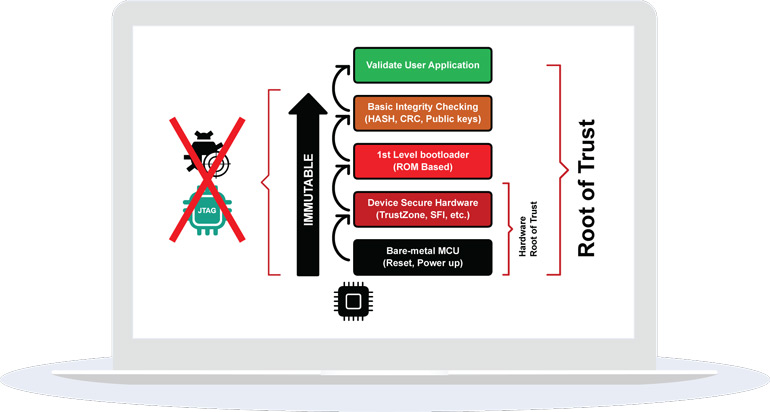
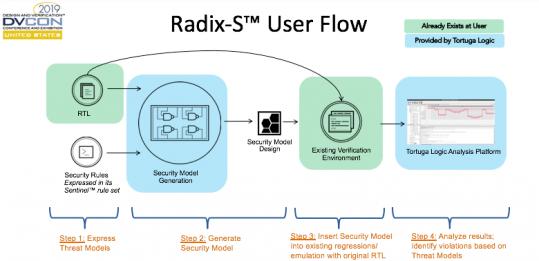
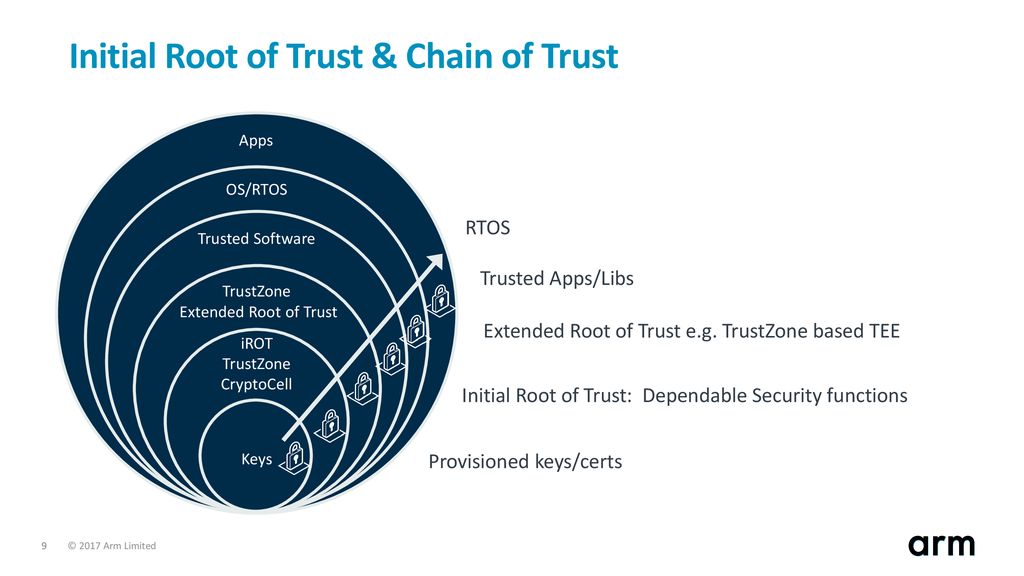
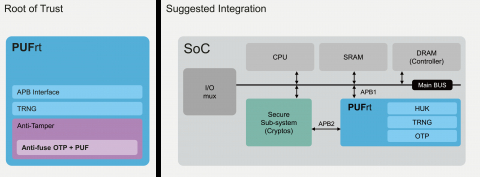
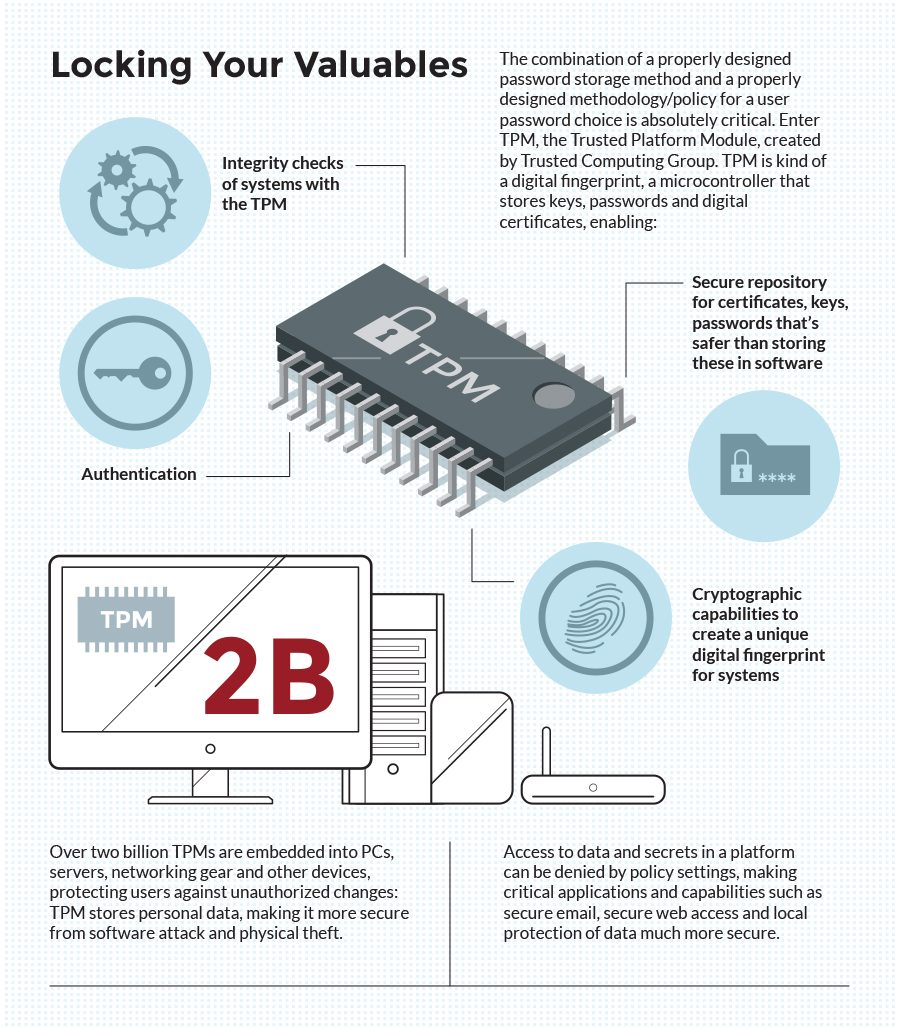
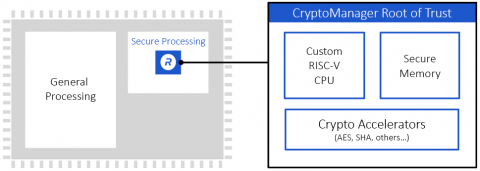
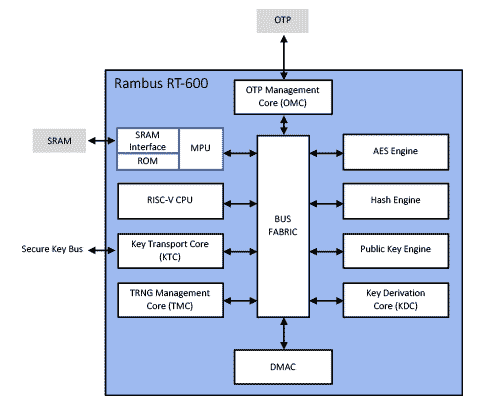
Using a Trusted Platform Module for endpoint device security in AWS IoT Greengrass | The Internet of Things on AWS – Official Blog
![PDF] Trusted Secure Embedded Linux From Hardware Root Of Trust To Mandatory Access Control | Semantic Scholar PDF] Trusted Secure Embedded Linux From Hardware Root Of Trust To Mandatory Access Control | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/027f005758189b38bb74095290cbc9ccdbad42f7/4-Figure2-1.png)
PDF] Trusted Secure Embedded Linux From Hardware Root Of Trust To Mandatory Access Control | Semantic Scholar