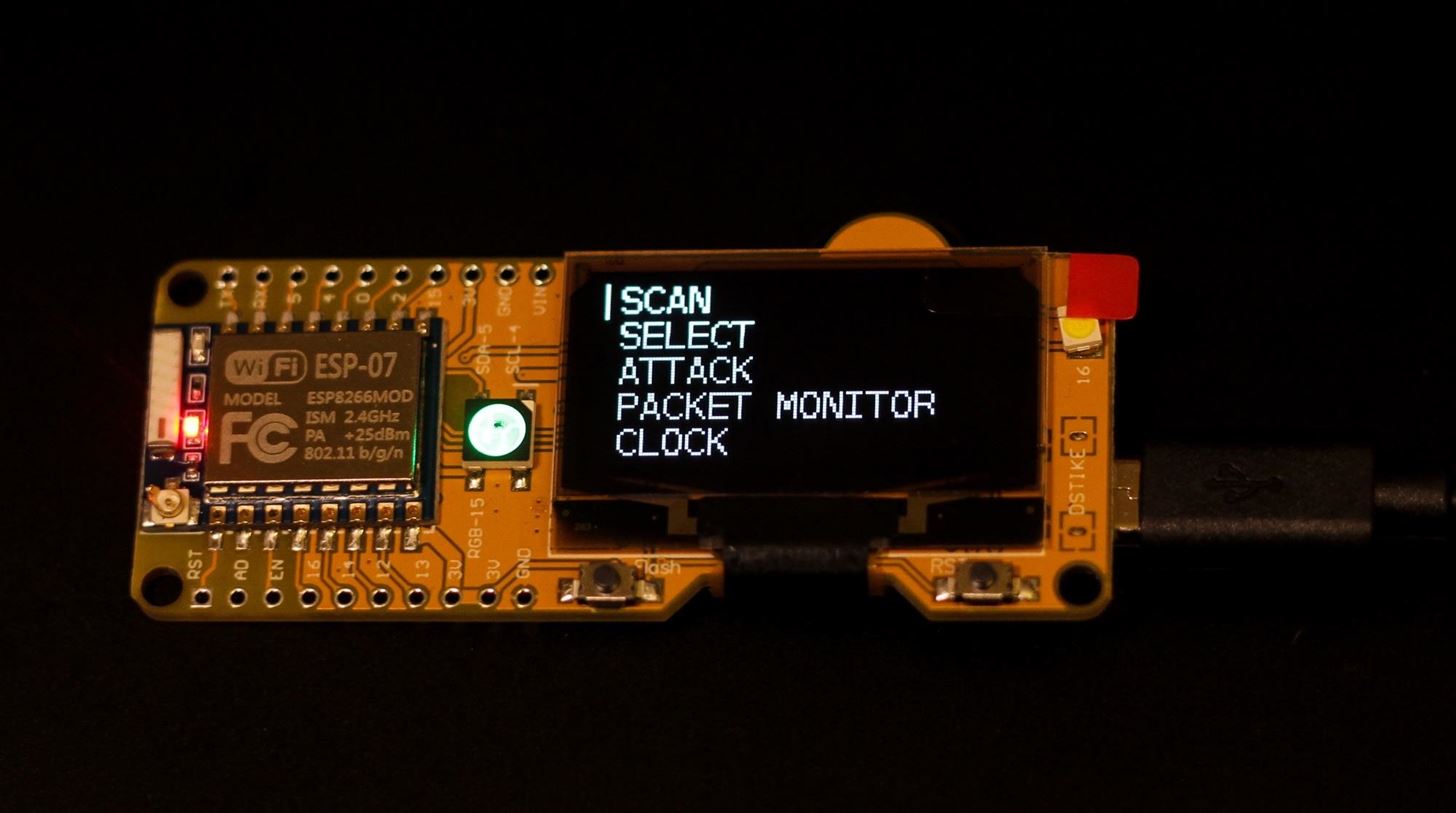
How to Scan, Fake & Attack Wi-Fi Networks with the ESP8266-Based WiFi Deauther « Null Byte :: WonderHowTo

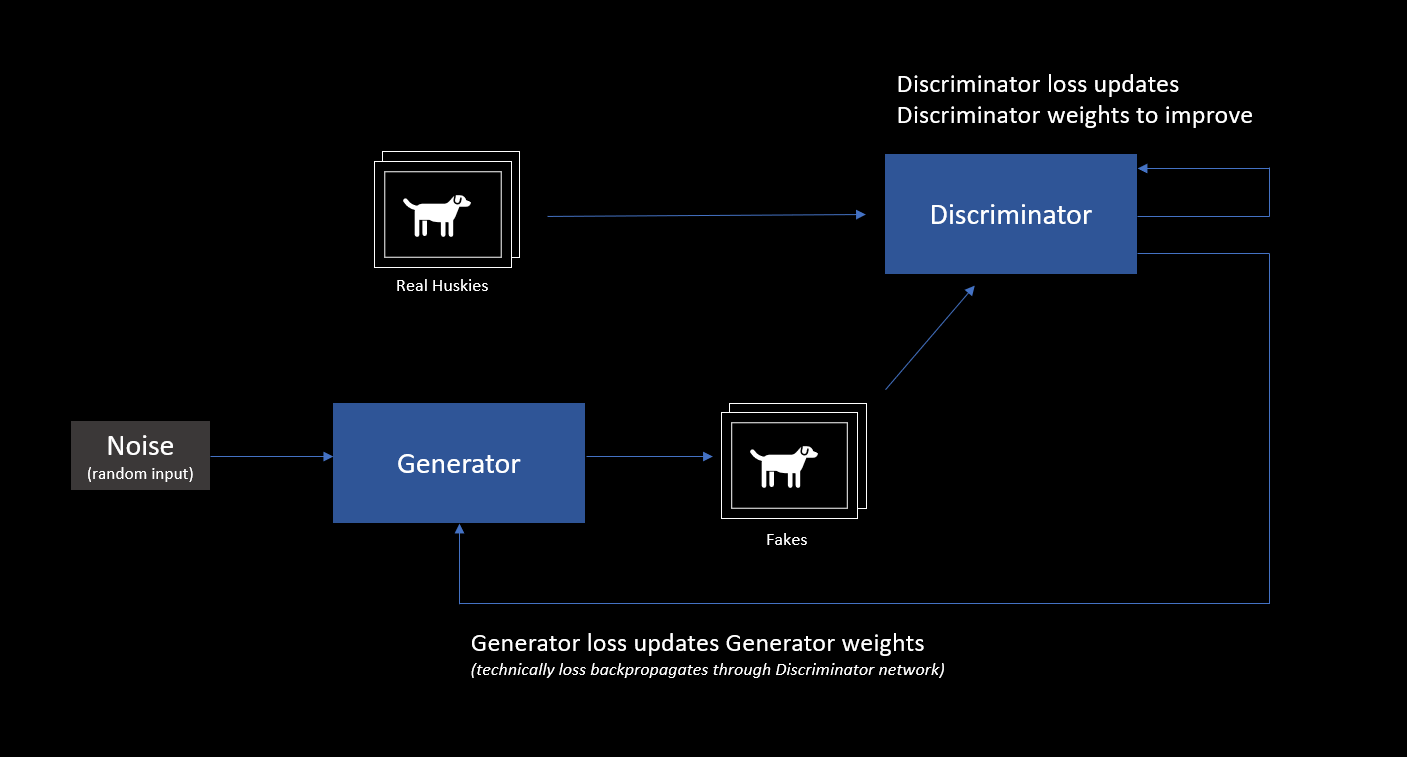
Applied Sciences | Free Full-Text | Palmprint False Acceptance Attack with a Generative Adversarial Network (GAN)

Cybersecurity: Internet security 101: Six ways hackers can attack you and how to stay safe - The Economic Times
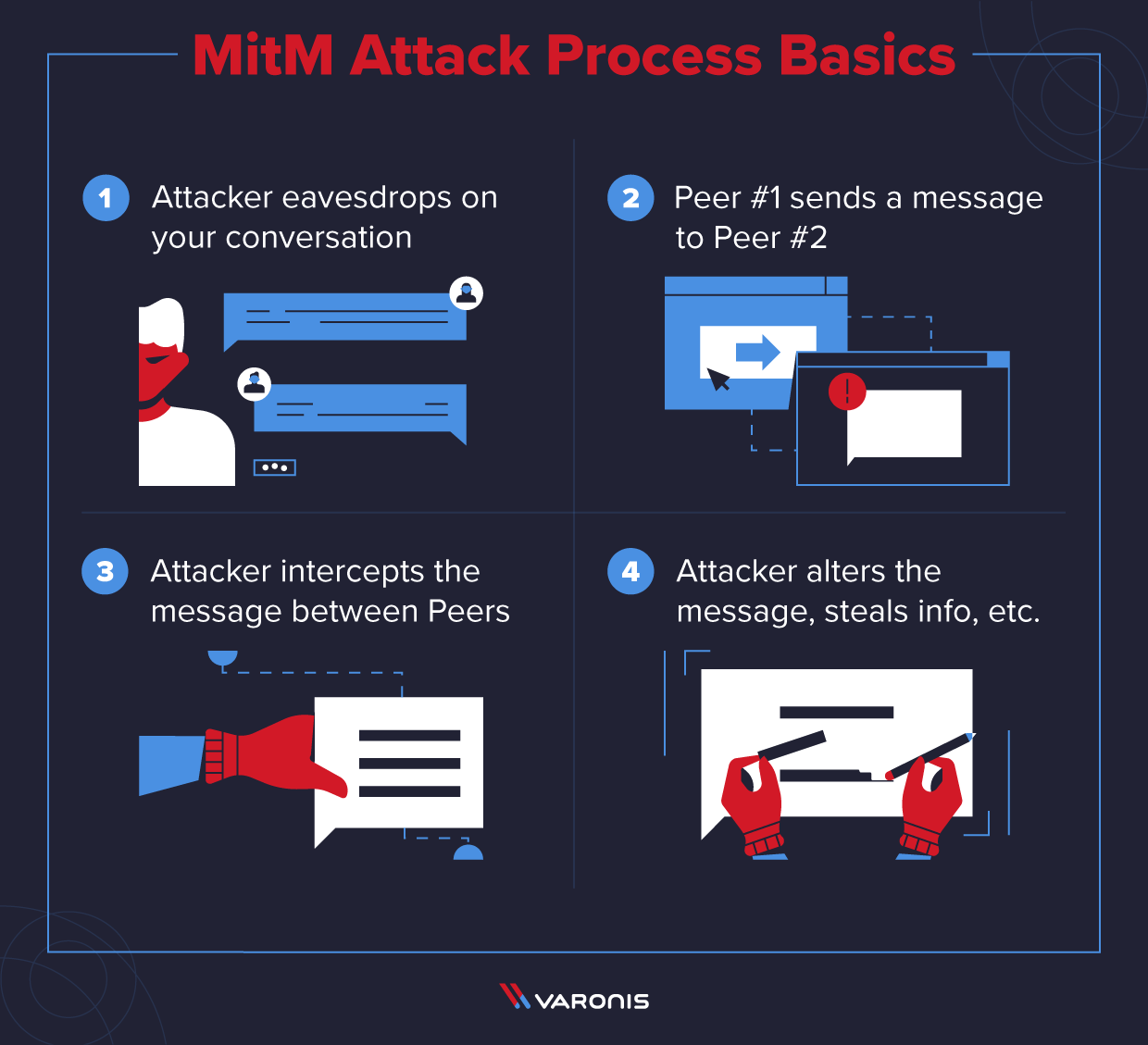
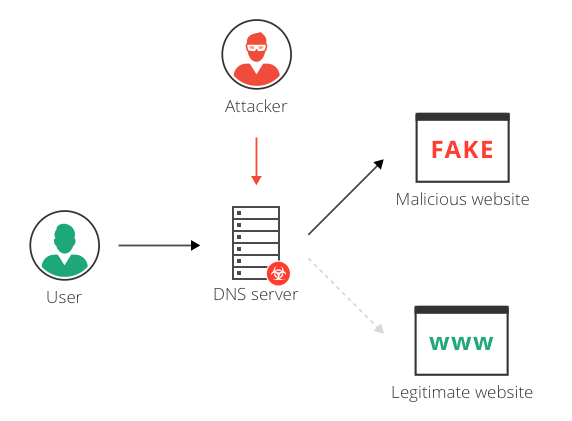
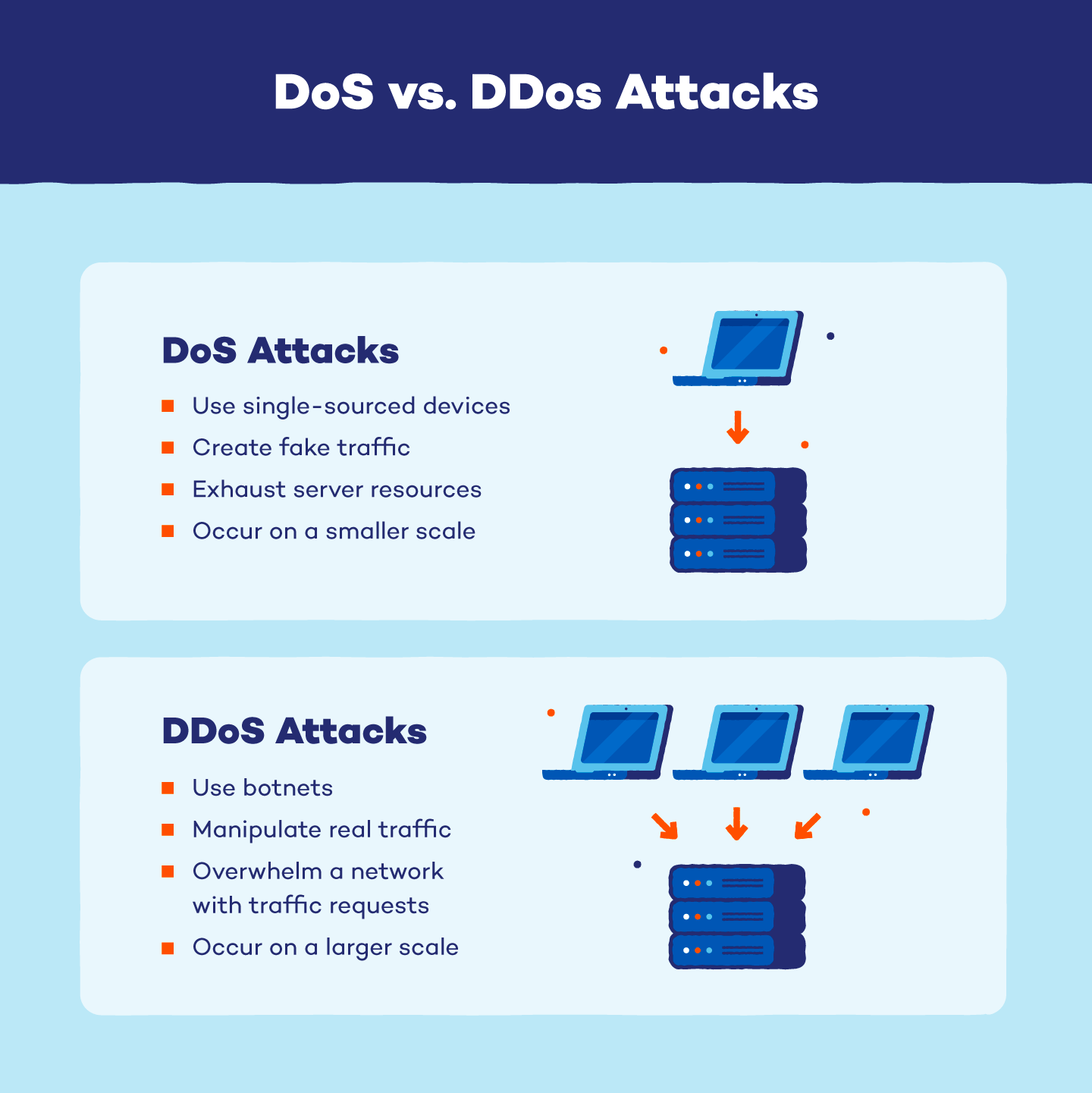

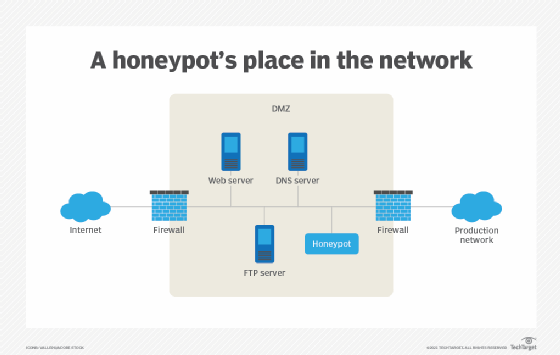


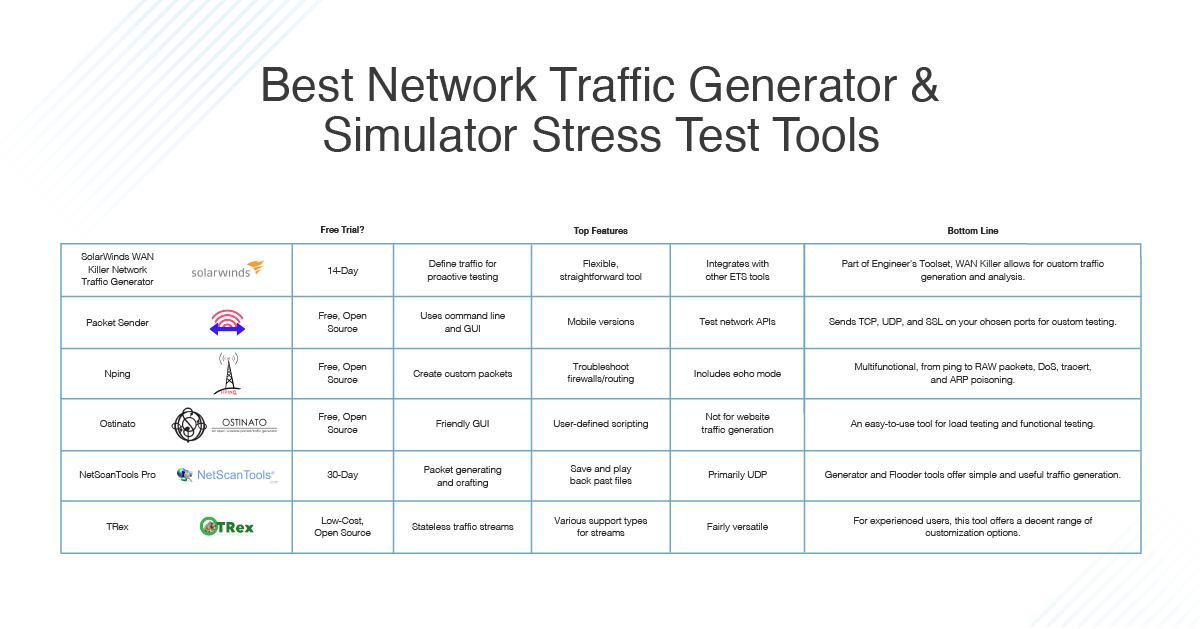
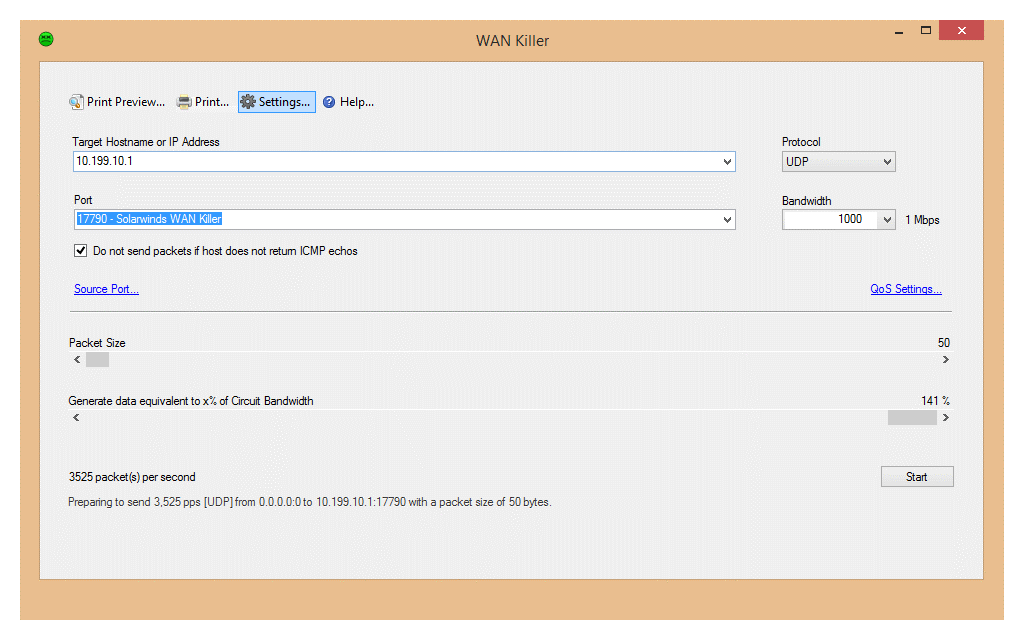

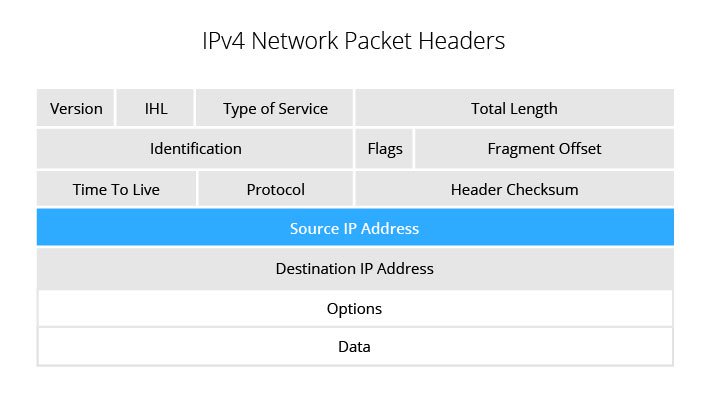
![PDF] SynGAN: Towards Generating Synthetic Network Attacks using GANs | Semantic Scholar PDF] SynGAN: Towards Generating Synthetic Network Attacks using GANs | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/e4a6f3b86811f6d30f7713395f4c2260fe64bc5f/2-Figure1-1.png)