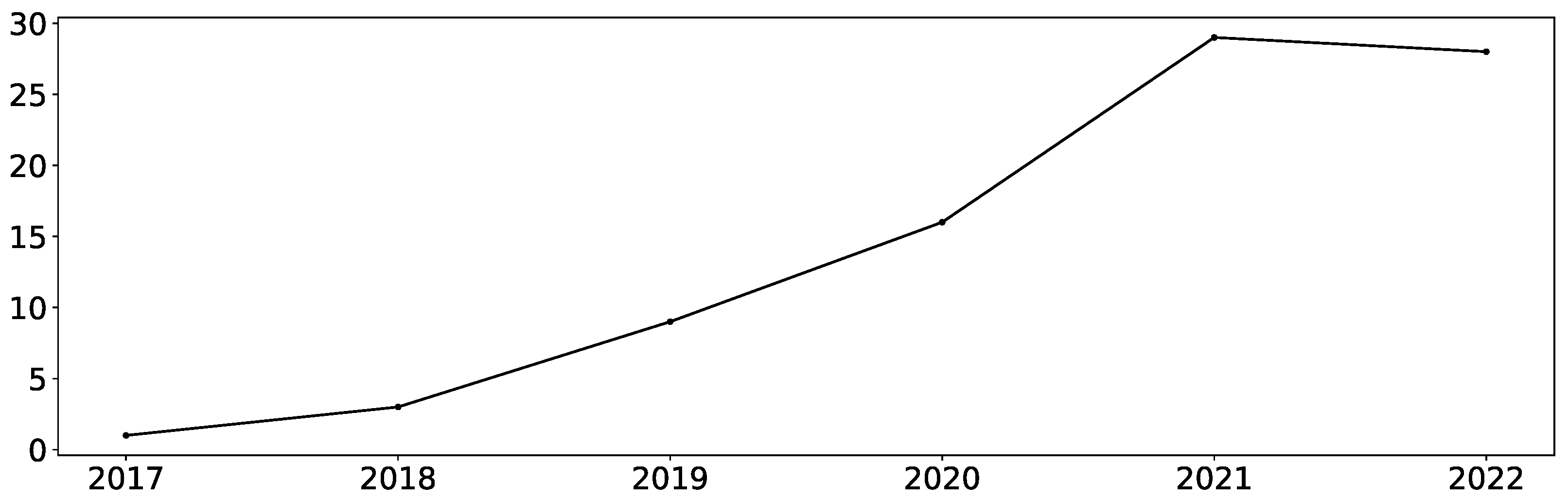
JLPEA | Free Full-Text | Comprehensive Study of Security and Privacy of Emerging Non-Volatile Memories

SEMTION Window Breaker Seat belt Cutter Car Emergency Escape Tool Safety Hammer, Pack of 2 (Black-Yellow), Escape Tools - Amazon Canada

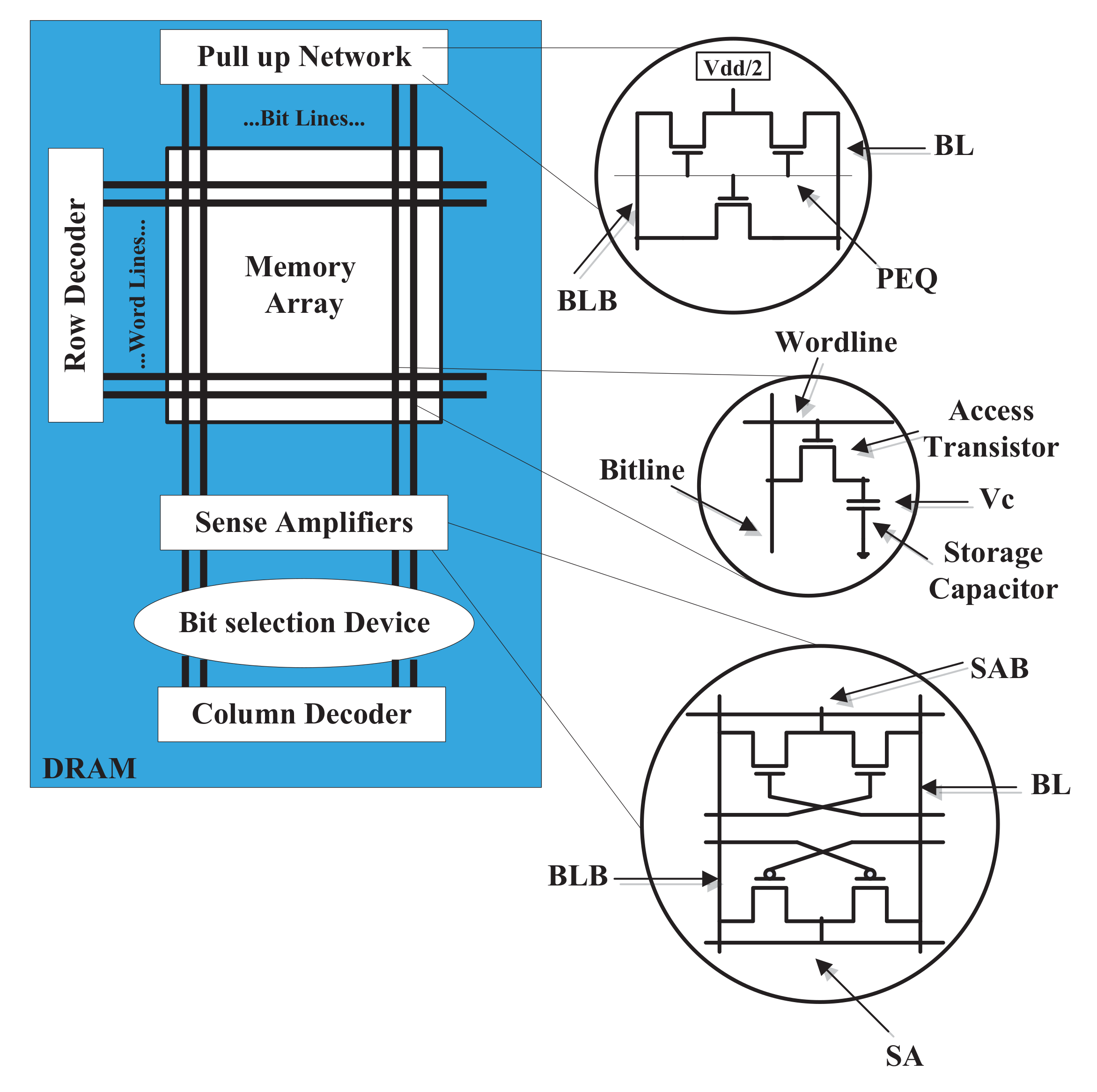
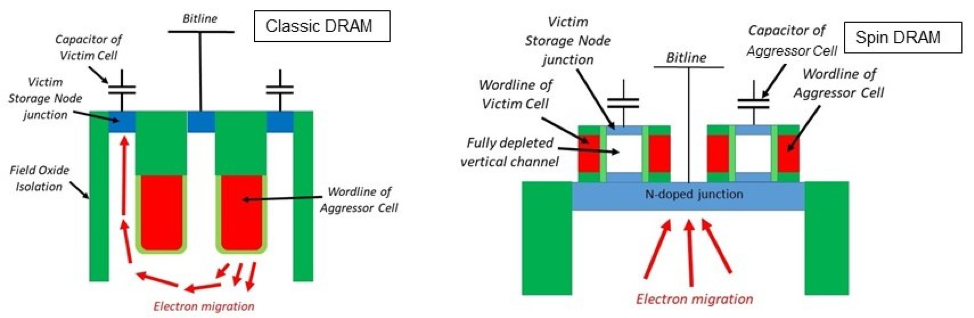
The Story of Rowhammer - Secure Hardware, Architectures, and Operating Systems Keynote - Onur Mutlu - YouTube
![Security] How to exploit DRAM with Hammertime (Rowhammer🔨 attack step by step) | by Anna Kim | Medium Security] How to exploit DRAM with Hammertime (Rowhammer🔨 attack step by step) | by Anna Kim | Medium](https://cdn-images-1.medium.com/fit/t/1600/480/1*KyZqWOj1uYmaAOo93fVLfg.jpeg)
Security] How to exploit DRAM with Hammertime (Rowhammer🔨 attack step by step) | by Anna Kim | Medium

2pcs Car Safety Hammer Life Saving Escape Emergency Hammer Seat Belt Cutter Window Glass Breaker Car Rescue Red Hammer Car Emergency Rescue Kit AliExpress | In Emergency Window Glass Breaker And Seat