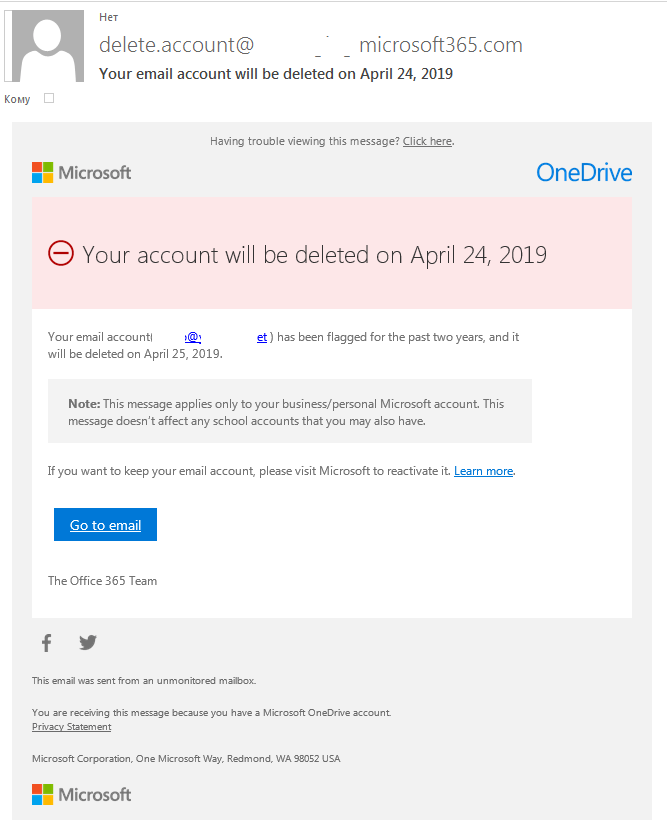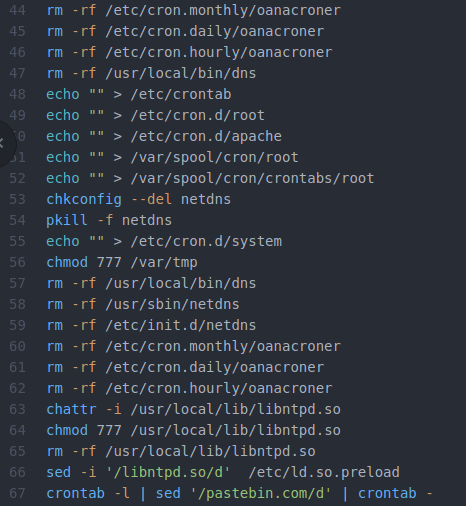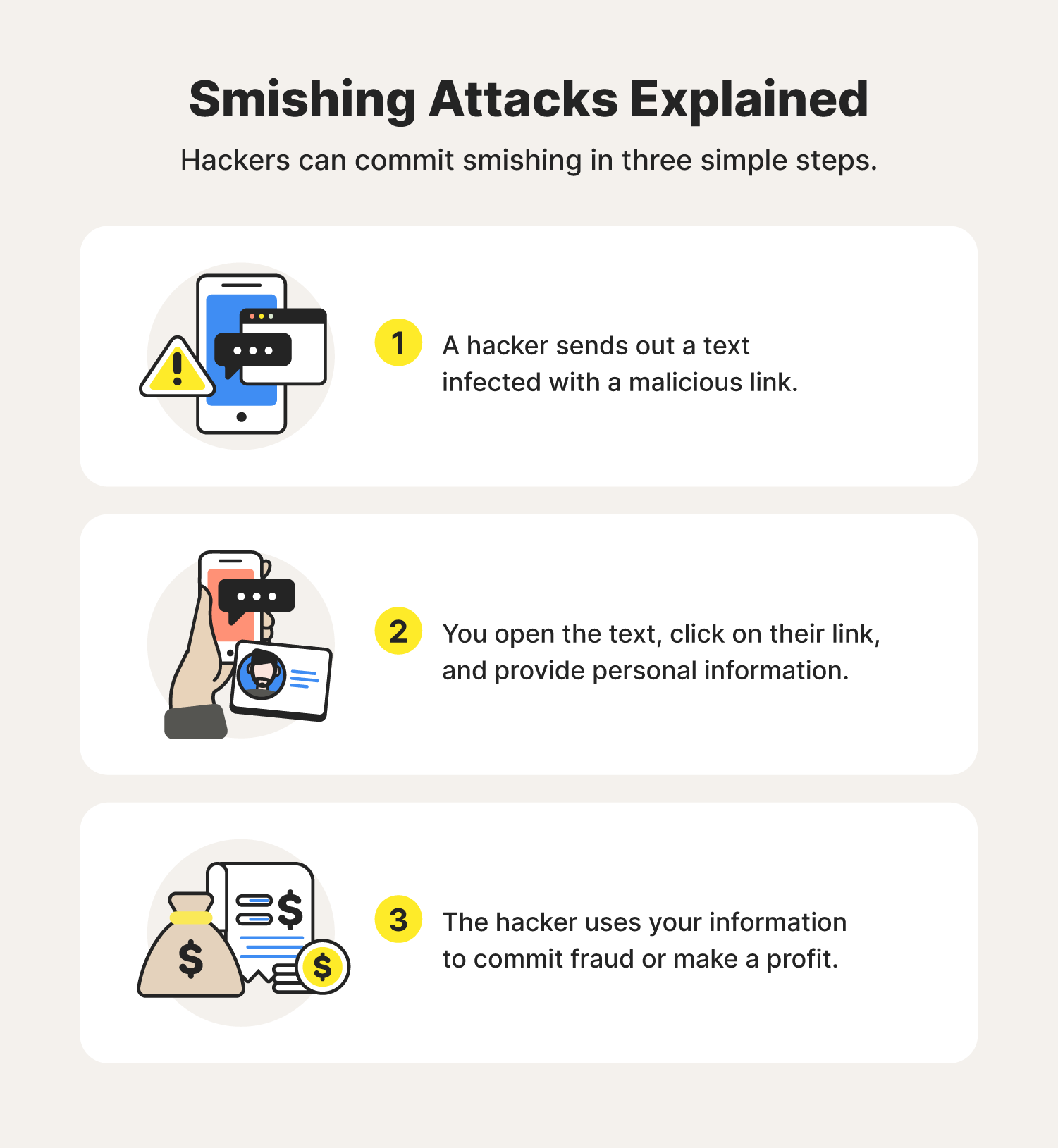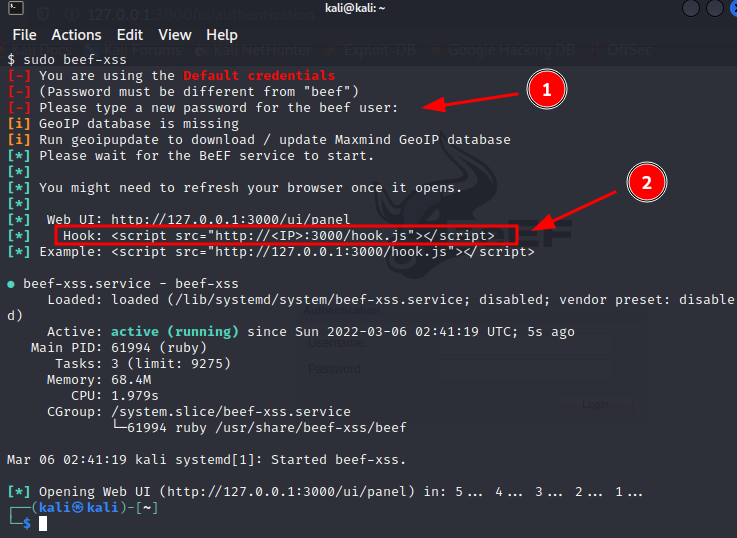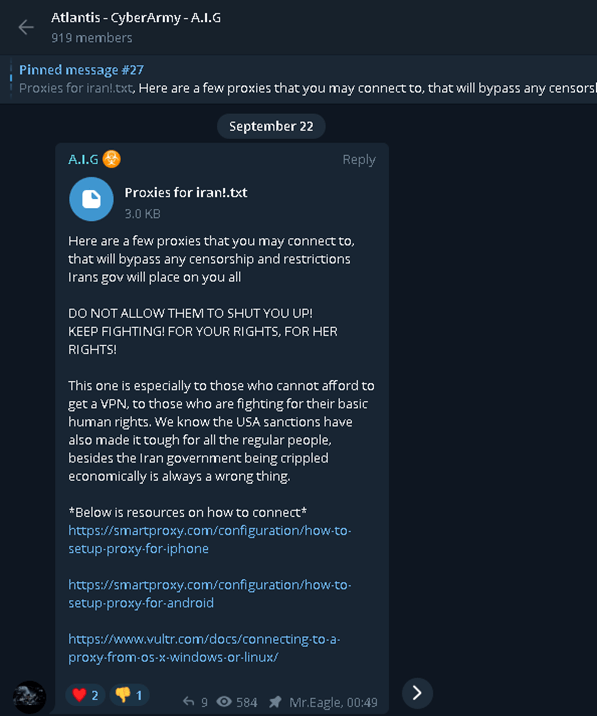
Hacker Groups take to Telegram, Signal and Darkweb to assist Protestors in Iran - Check Point Software

Which? on Twitter: "🚨How this WhatsApp scam works 1. You get text 2. Then a WhatsApp message from a friend asks you for the code. DO NOT SEND Your friend's WhatsApp has