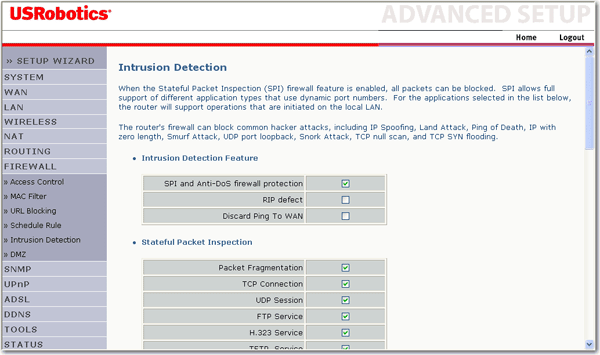
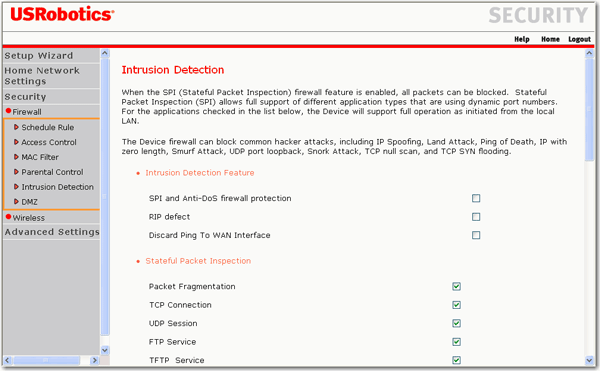
Detected Large Ping attack and dropped - should I be worried or anyone know how I can address this? : r/TPLink_Omada
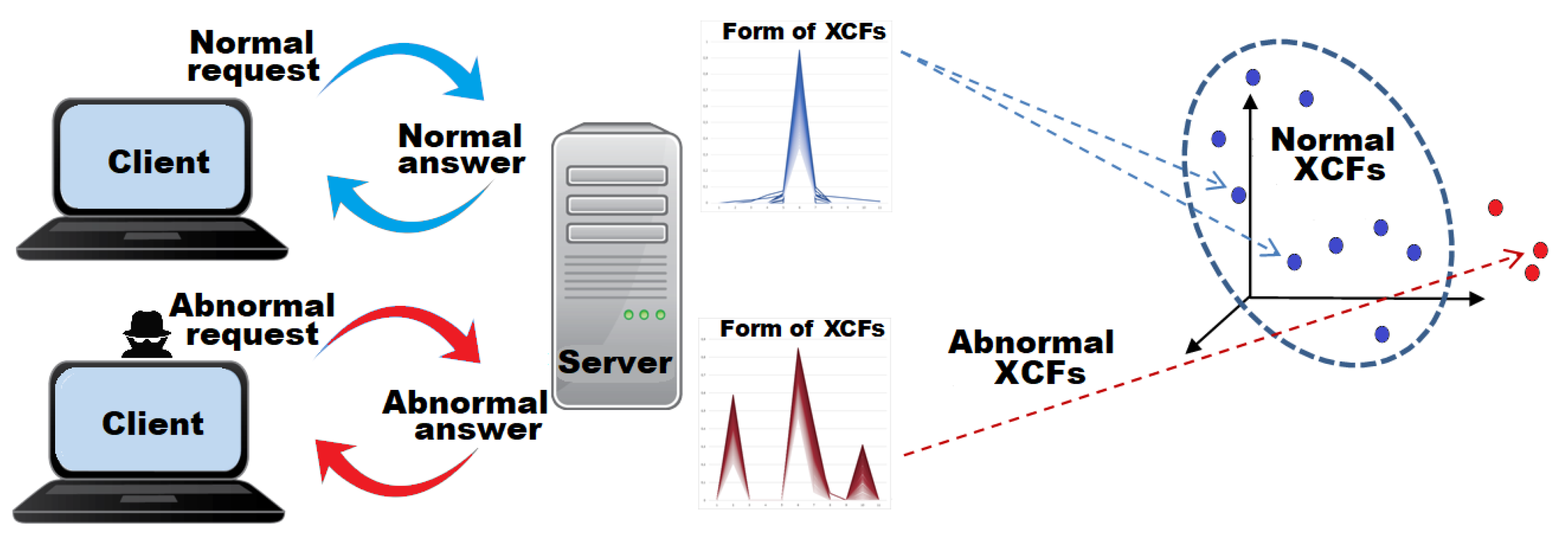
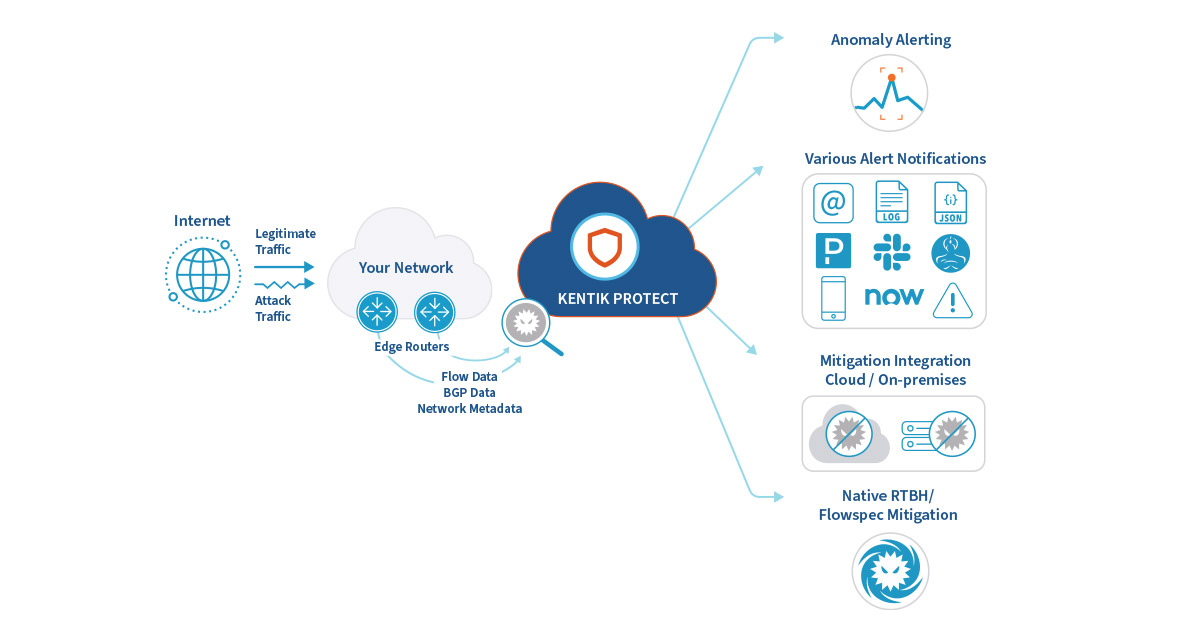
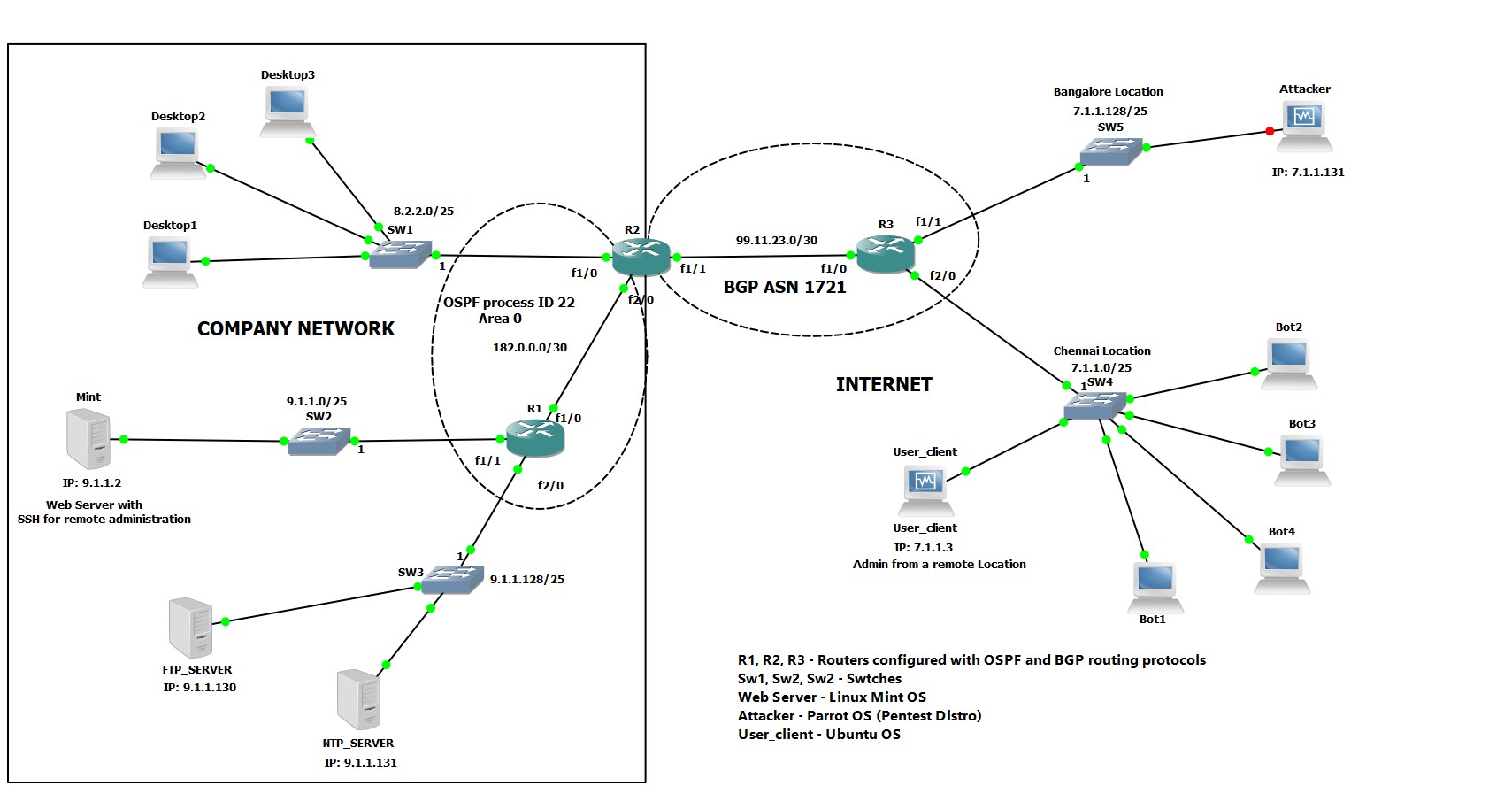
Information | Free Full-Text | Anomaly-Based Method for Detecting Multiple Classes of Network Attacks

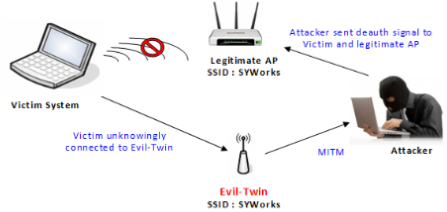
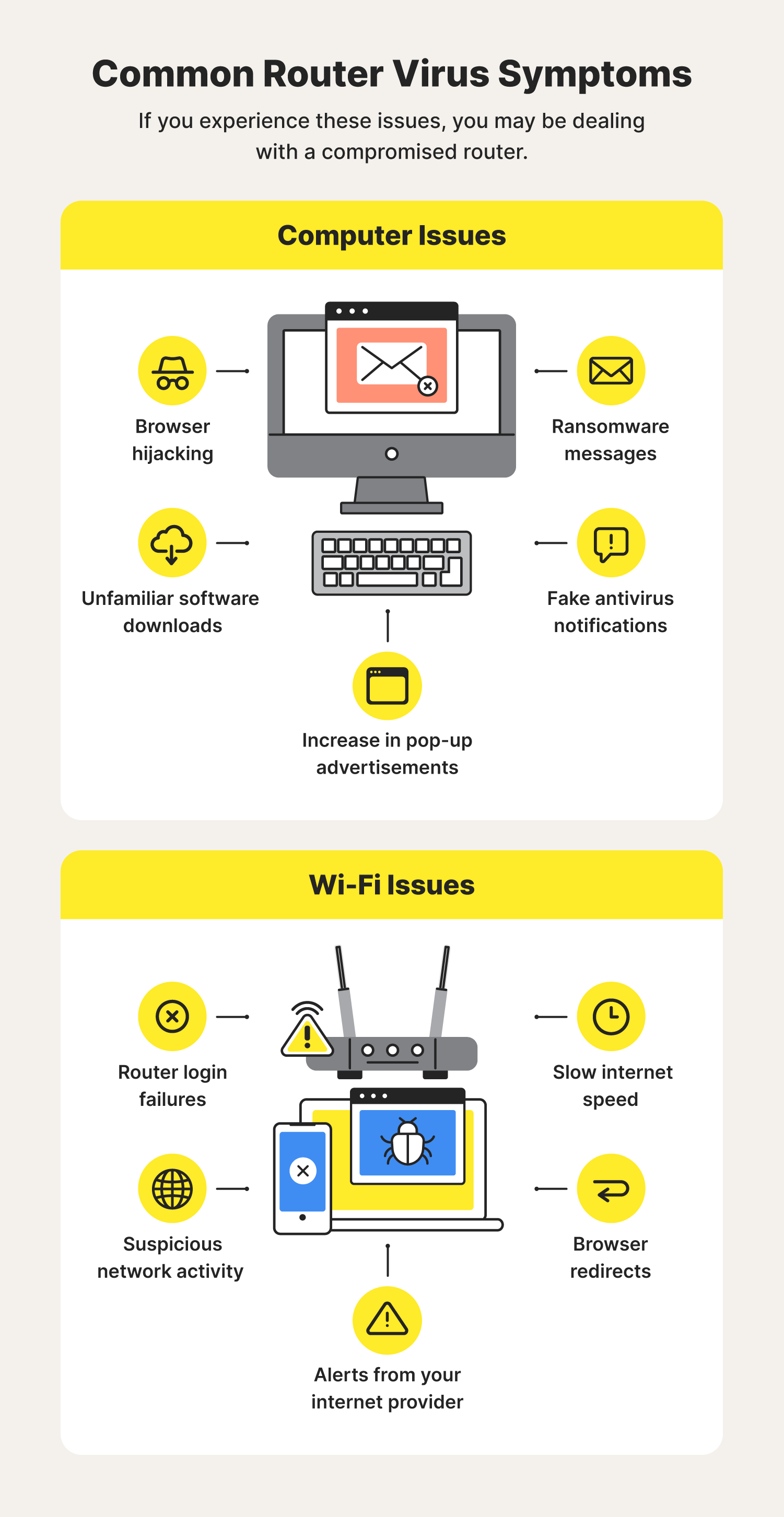
ZuoRAT, the game changing attack that emphasizes the need for router protection - SAM Seamless Network