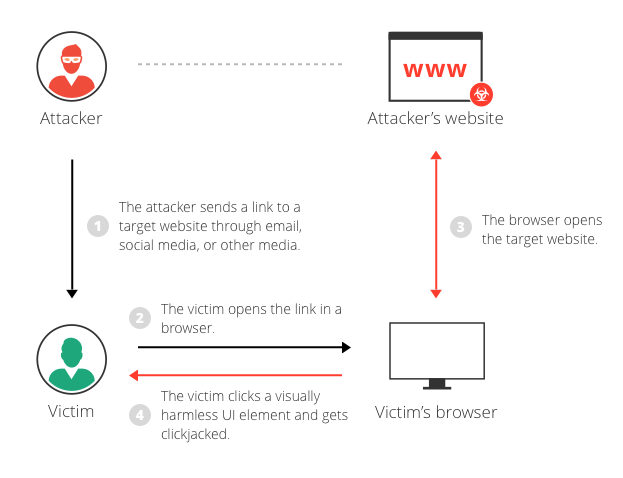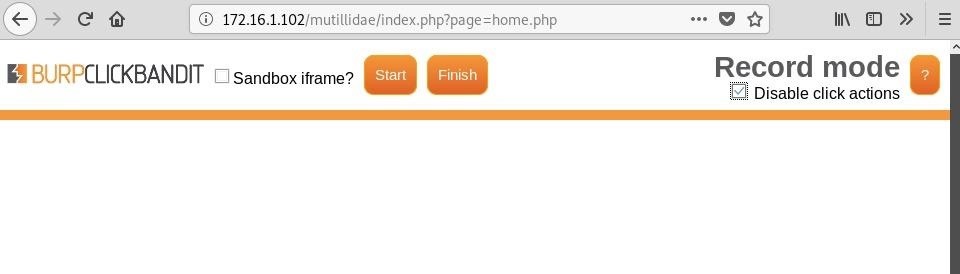
How to Generate a Clickjacking Attack with Burp Suite to Steal User Clicks « Null Byte :: WonderHowTo
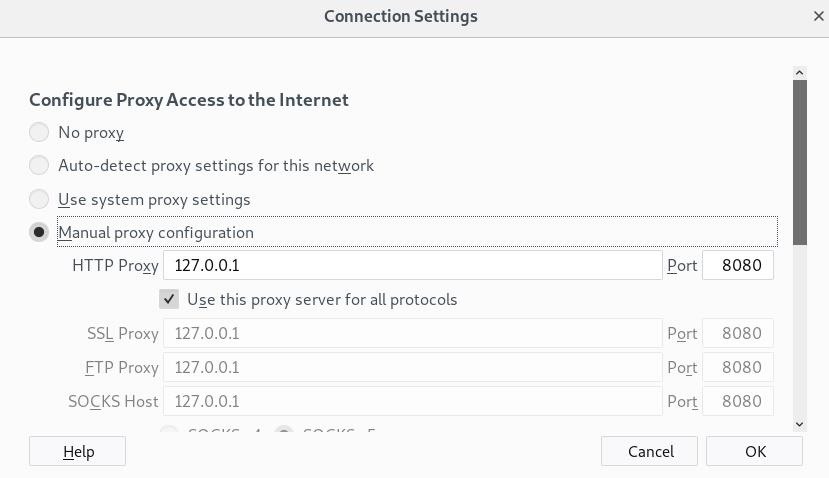
How to Generate a Clickjacking Attack with Burp Suite to Steal User Clicks « Null Byte :: WonderHowTo

How to Generate a Clickjacking Attack with Burp Suite to Steal User Clicks « Null Byte :: WonderHowTo
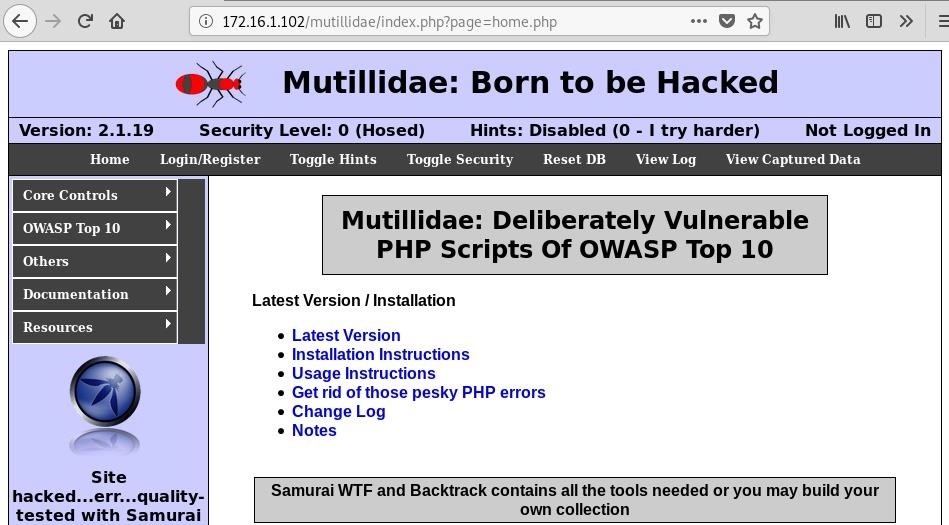
How to Generate a Clickjacking Attack with Burp Suite to Steal User Clicks « Null Byte :: WonderHowTo
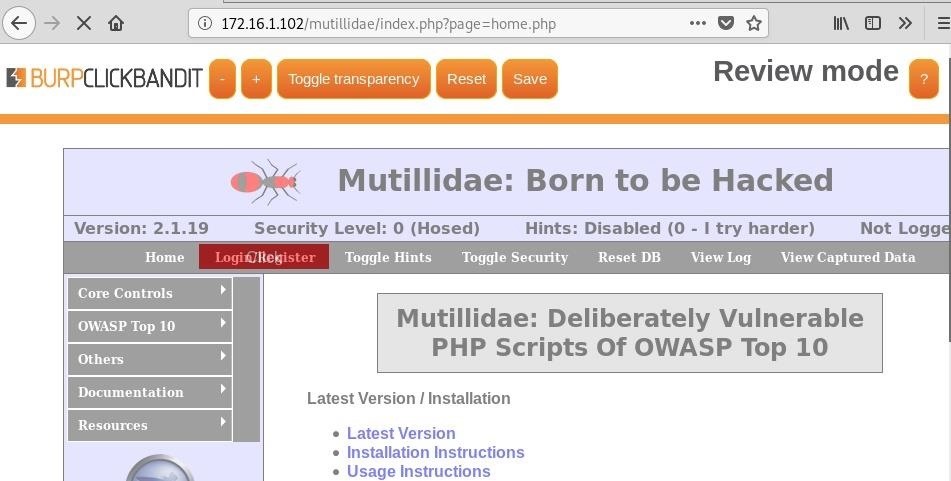
How to Generate a Clickjacking Attack with Burp Suite to Steal User Clicks « Null Byte :: WonderHowTo
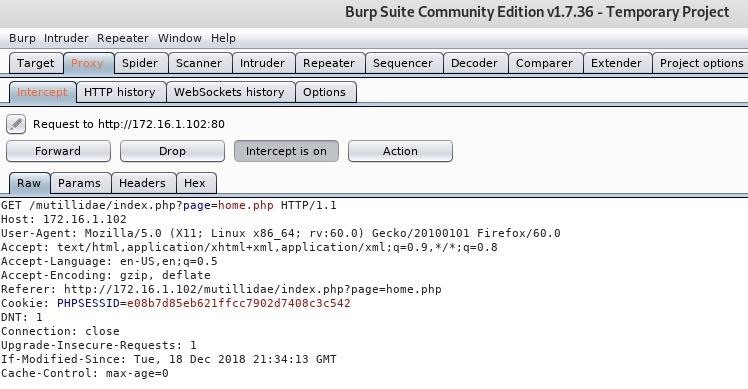

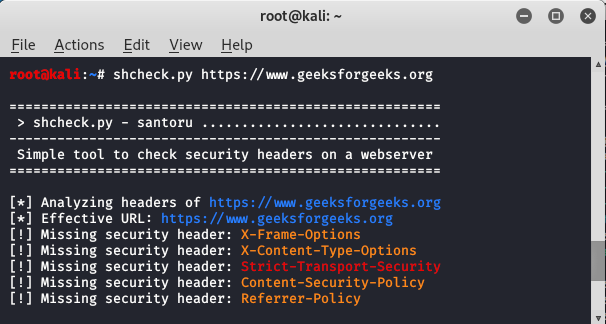



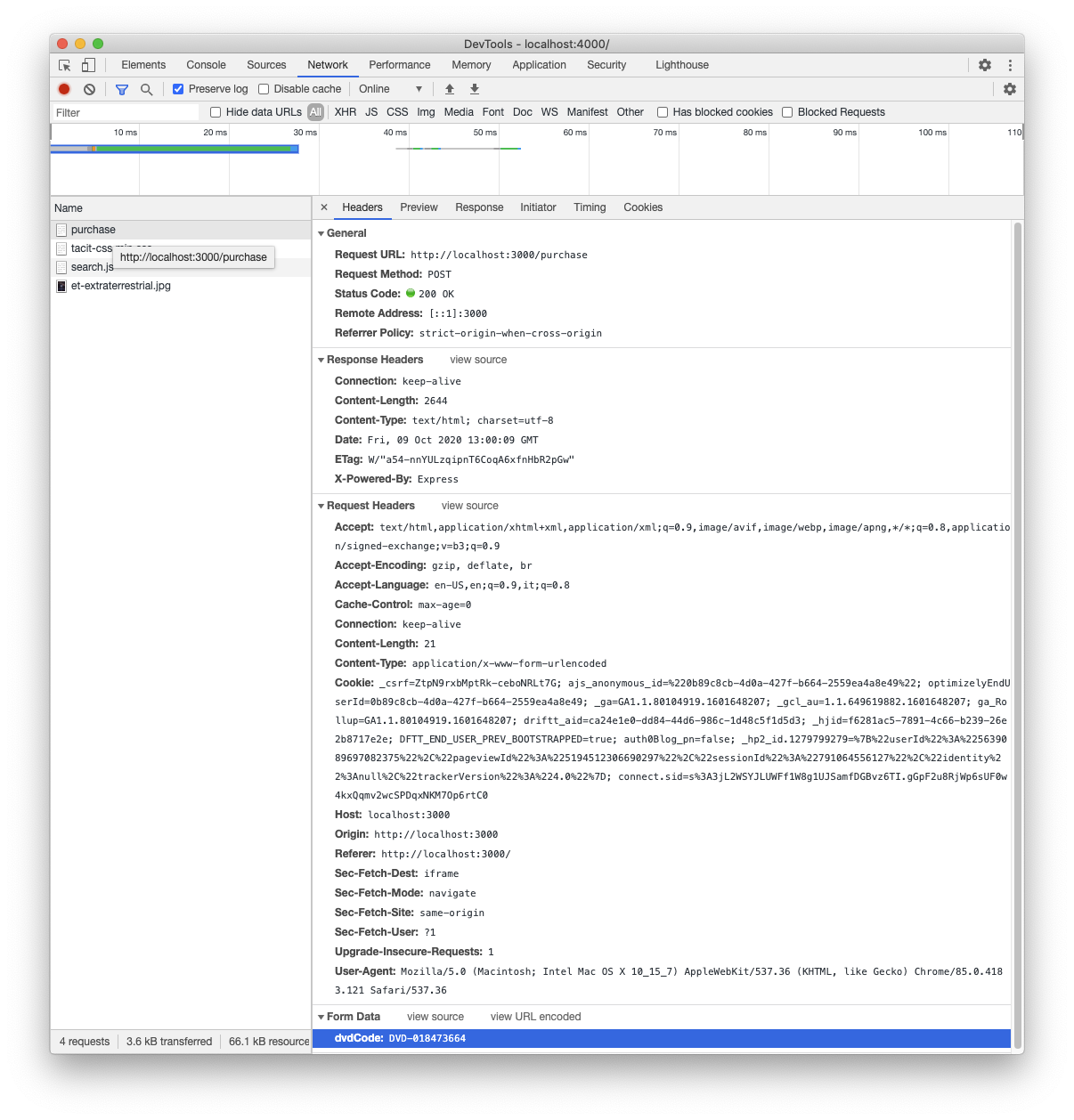



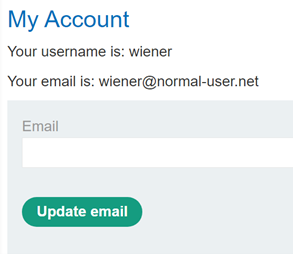
![What is a Clickjacking Attack? [+Examples & Prevention] What is a Clickjacking Attack? [+Examples & Prevention]](https://edgemesh.com/5e3d3268a134a79339be8368/6218ffe81407f1b009c178f7_JC2somFAvkQkEKfSy6ZLNOZwa1Q_-64HgwawhTHGG_75sLd9JbrkWoi90s5rFCBVg24jAlhQ6sjbDxbqI6HiboiNcnXcy8XKojfxbn14ayMzlFKiPJDbk-iMWq26VA.png?em-origin=assets.website-files.com)

![What is a Clickjacking Attack? [+Examples & Prevention] What is a Clickjacking Attack? [+Examples & Prevention]](https://edgemesh.com/5e3d3268a134a79339be8368/6218ffe7d465fe29f21889be_R5PTNnOrgZutWzKYUbnU0nF9Xj65mWS78FXZApyneciN7AA6AJa1O-LjEcKFMCPm2piyNO1KGreBwXWQUTPdjh6t8XUZ_xTGjwf95_eU1NRR-n14g2F3jvll5SkVJA.png?em-origin=assets.website-files.com)