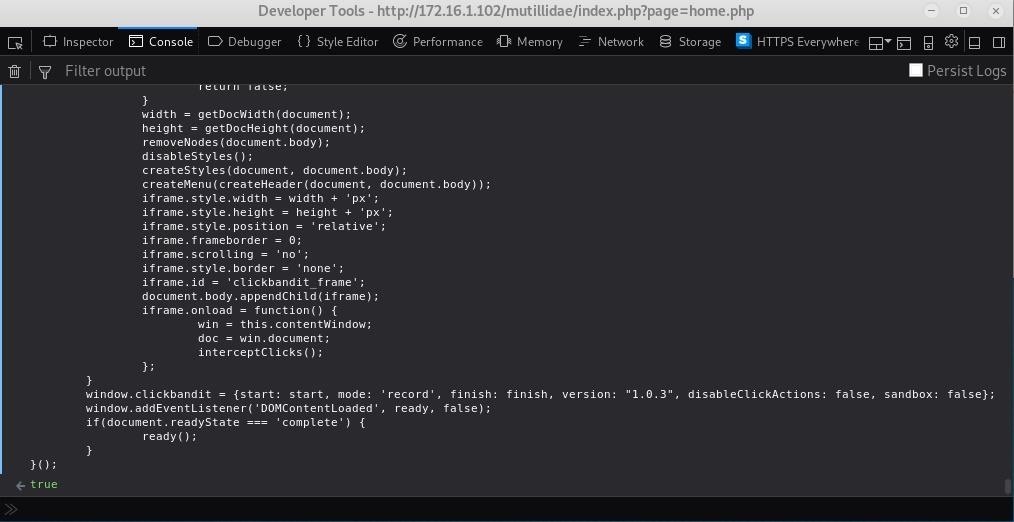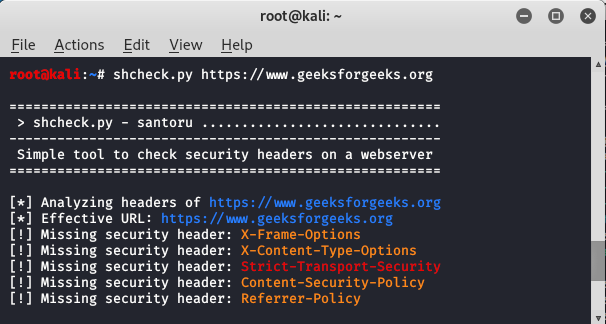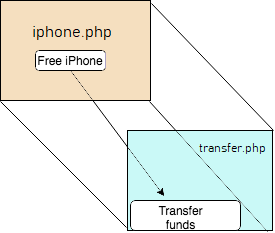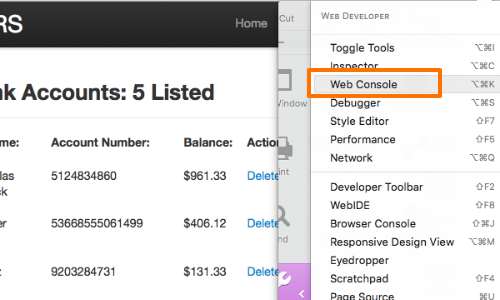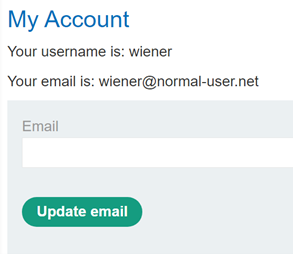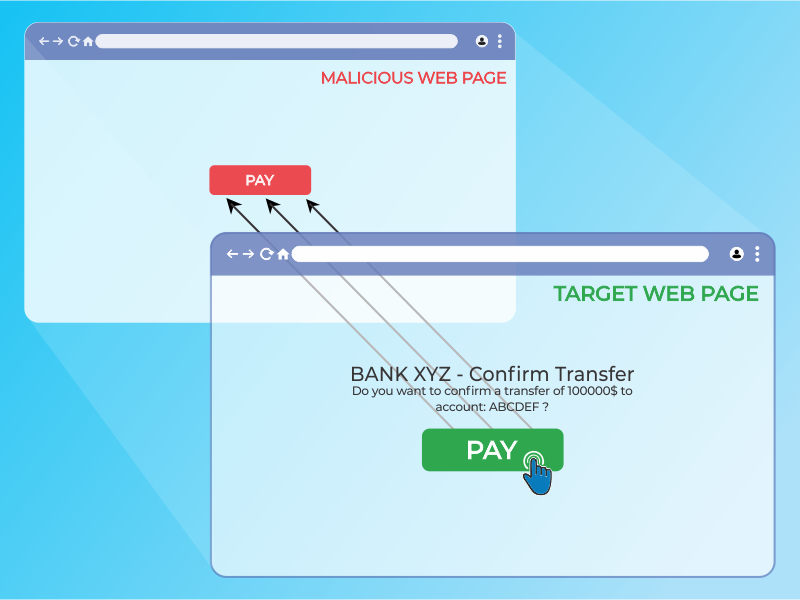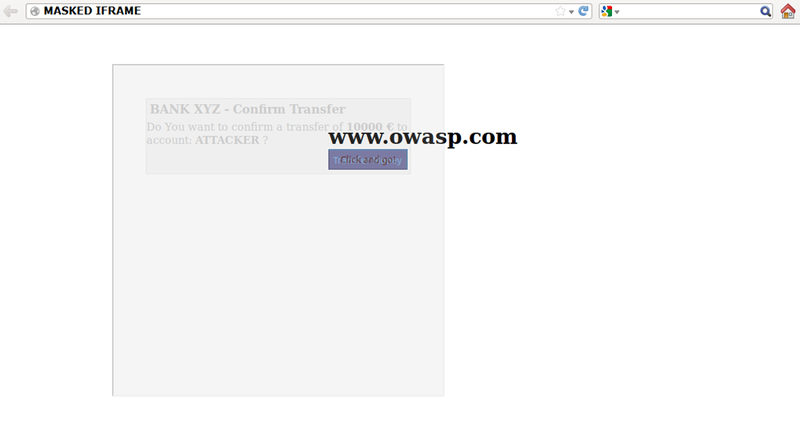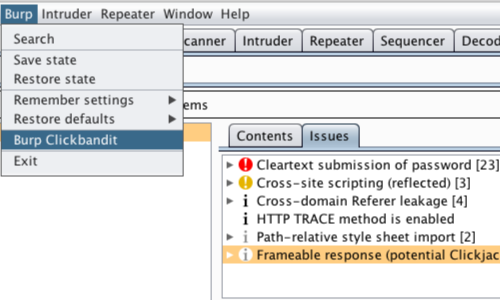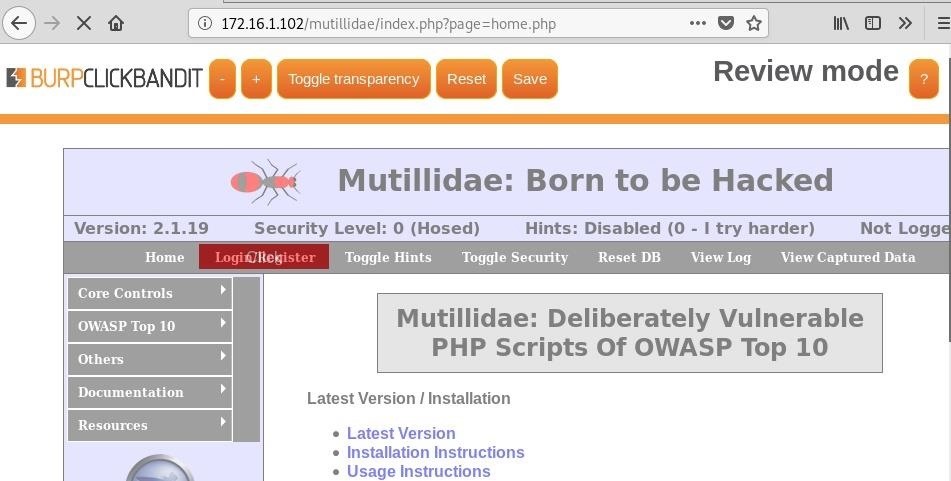
How to Generate a Clickjacking Attack with Burp Suite to Steal User Clicks « Null Byte :: WonderHowTo

How i made the multiple hall of fame in Nokia within 2 minutes | by Vedavyasan S (@ved4vyasan) | System Weakness
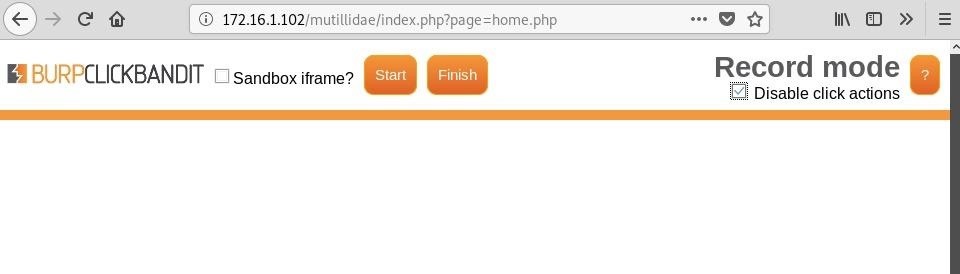
How to Generate a Clickjacking Attack with Burp Suite to Steal User Clicks « Null Byte :: WonderHowTo
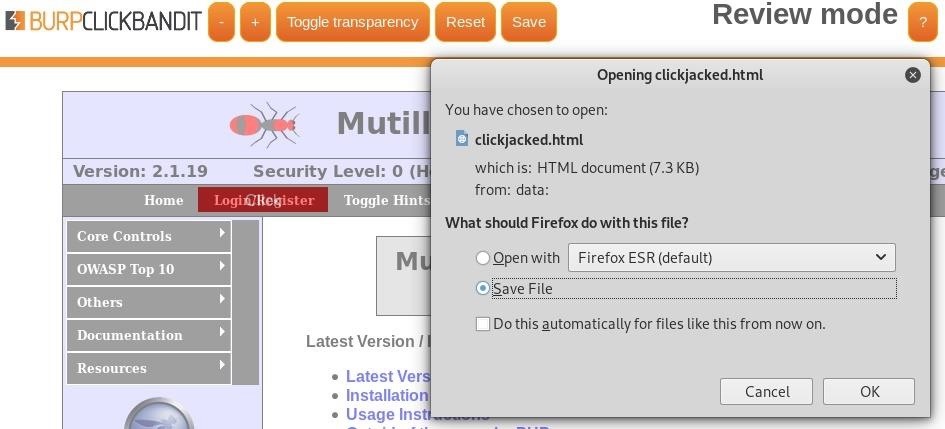
How to Generate a Clickjacking Attack with Burp Suite to Steal User Clicks « Null Byte :: WonderHowTo
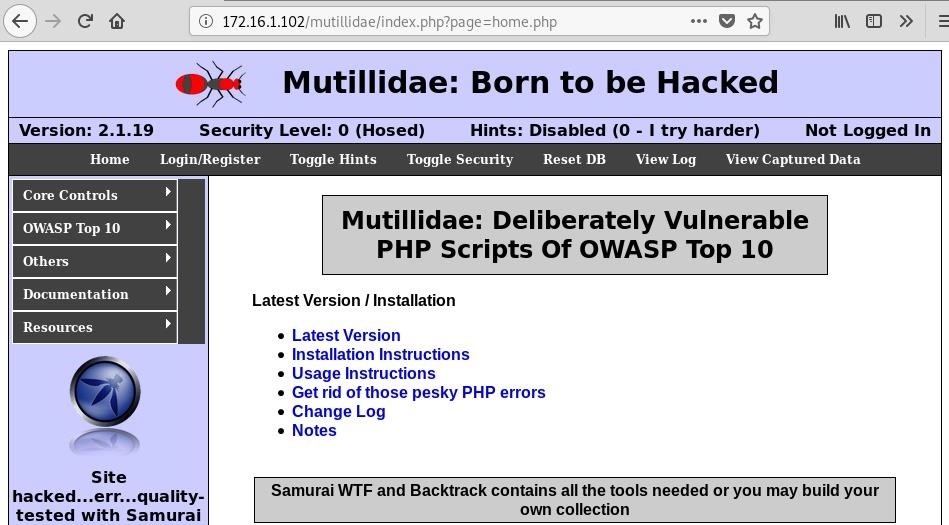
How to Generate a Clickjacking Attack with Burp Suite to Steal User Clicks « Null Byte :: WonderHowTo
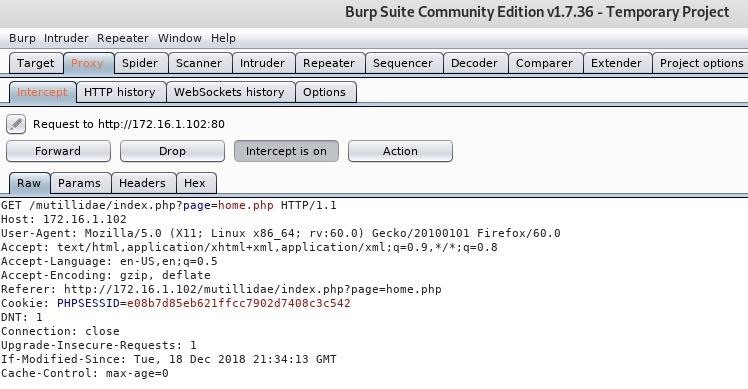
How to Generate a Clickjacking Attack with Burp Suite to Steal User Clicks « Null Byte :: WonderHowTo
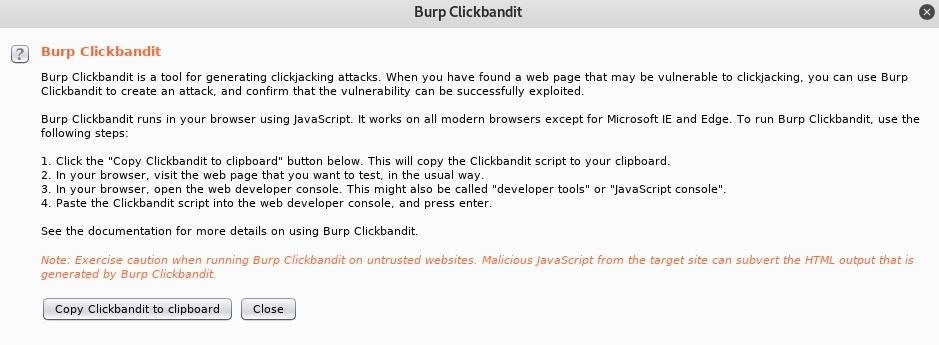
How to Generate a Clickjacking Attack with Burp Suite to Steal User Clicks « Null Byte :: WonderHowTo